Why Companies Should Focus on Prevention and Detection First
Cyberspace threats are constantly increasing, and cyberattacks have considerable financial consequences. The average damage from a data breach in 2024 was around USD 4.88 million, an increase of 10% compared to the previous year (IBM Breach Report 2024). Companies must invest in robust cyber defense; incident response (IR) is central.
Incident response encompasses a range of measures and technologies that help companies be prepared for security incidents and detect and minimize them as early as possible. A well-prepared IR plan improves a company’s ability to respond and strengthens its overall security posture. The goal is to respond faster and minimize damage.
The NIST incident response way
The National Institute of Standards and Technology (NIST) is renowned for its rigorous cybersecurity standards, including the Cybersecurity Framework (NIST CSF) and the Computer Security Incident Handling Guide (NIST SP 800-61). These guides outline effective incident response in four key steps:
- Preparation: Establish security policies, communication plans, and tools like monitoring software. Strengthen defenses through risk assessments and system hardening.
- Detection and Analysis: Identify and assess threats with tools like Intrusion Detection Systems (IDS), EDR, Network Detection and Response (NDR), and SIEM for early, targeted response.
- Containment, Remediation, and Recovery: Isolate and neutralize threats to prevent spread. Implement patches, backups, and recovery measures to restore operations.
- Post-Processing: Analyze the incident to uncover vulnerabilities and refine the security strategy, ensuring continuous improvement.
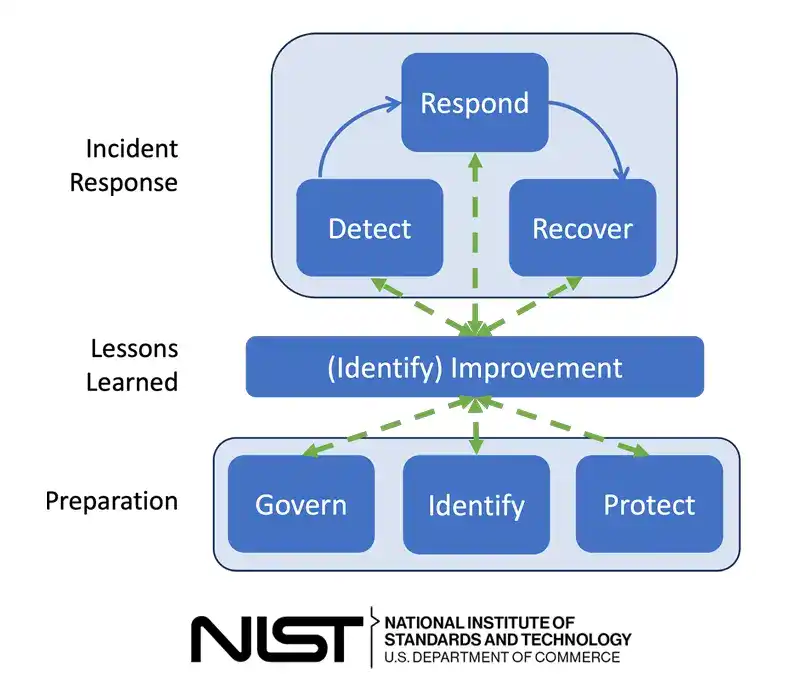
Source: NIST resource center
The NIS2 Directive and extended requirements
The EU NIS2 Directive also strengthens cybersecurity requirements across EU member states, particularly for incident response. It broadens its scope to include more critical sectors, such as healthcare, energy, and digital infrastructure, mandating that these sectors have robust IR measures.
Essential requirements include timely reporting of incidents within 24 hours for early alerts and 72 hours for detailed reports, promoting quick, coordinated responses to cyber threats.
NIS2 also emphasizes preventive measures, such as continuous risk assessments, IR planning, and regular security training for staff. Additionally, organizations must collaborate closely with national authorities and EU bodies to foster a collective defense posture.
NIS2 enforces compliance with significant penalties, encouraging organizations to strengthen their IR capabilities and ensuring they can respond swiftly and effectively to protect critical services and reduce potential cyber impacts.
Technologies to improve incident response: visibility is key
Visibility is crucial for incident response because it provides the comprehensive insights necessary to detect, investigate, and respond to security threats quickly and effectively. A machine learning-powered NDR tool is vital for effective incident response, as it enhances early detection, provides essential context, and enables rapid, well-informed reactions to threats.

By monitoring all network activity, an NDR tool can detect abnormal patterns that indicate early-stage threats, allowing incident responders to mitigate issues before they escalate. Additionally, visibility offers critical context to alerts, helping responders assess whether a threat is real or a false positive, which ensures prioritized and resource-efficient responses.
During an investigation, visibility across network layers enables responders to trace attack chains, perform root cause analyses, and understand attacker behavior, contributing to more robust defenses and preventing future incidents. Furthermore, visibility accelerates response speed by consolidating data, automating responses, and isolating affected systems, reducing overall damage.
It supports proactive threat hunting, allowing responders to uncover hidden threats that traditional monitoring might miss. Machine learning models within NDR tools adapt to new threats by learning from network activities, refining detection capabilities, and surfacing relevant alerts.
Finally, post-incident forensics enabled by detailed visibility aids in comprehensive analysis, compliance, and reporting, reinforcing a robust security posture for the organization.
Minimize potential damage
We saw that what a machine learning-powered NDR provides is critical for effectively managing and mitigating security incidents in a dynamic threat landscape. The platform Exeon.NDR continuously monitors network traffic, providing a detailed overview that enables early anomaly and threat detection. Advanced machine learning identifies known and unknown threats, enhancing the speed and accuracy of incident detection.
Its intuitive visualization tools and analytics facilitate rapid incident investigation and response. Exeon.NDR integrates seamlessly with existing security infrastructures, requiring no additional hardware for deployment.
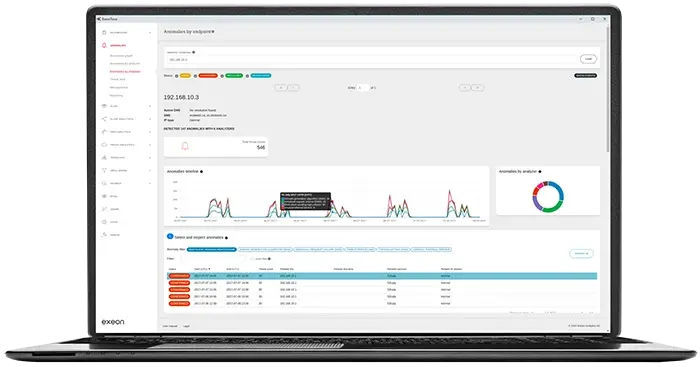
These capabilities allow organizations to detect, analyze, and respond to incidents effectively, minimizing potential damage and ensuring business continuity.
Conclusion
Incident response is an essential part of any cyber security strategy. Companies that invest in robust solutions such as NDR protect their data and minimize potential damage from attacks. Exeon offers a tailor-made solution: a comprehensive NDR platform that detects threats early, isolates attacks, and prevents damage quickly. Rely on Exeon to prepare your company optimally for the challenges of the digital age.
Reach out for any questions on how to protect your network and ensure optimal, efficient incident response.
For more on NDR, take a look at our recorded videos!