(image generated via DALL·E)
The Octo (ExobotCompact) malware family has become the dominant threat in the cyber security landscape. The release of Octo2, an evolved variant, demonstrates the increasing sophistication of modern malware. Octo2 targets Android devices and uses Domain Generation Algorithms (DGA) to generate dynamic Command and Control (C2) servers, making detection much more difficult. These characteristics and advanced anti-analysis techniques make Octo2 a particularly dangerous threat.
The emergence of sophisticated malware such as Octo2 poses a significant challenge for cyber security professionals. With its advanced features, such as enhanced remote access capabilities, advanced obfuscation techniques, and a new Domain Generation Algorithm (DGA), Octo2 is an example of an always faster-evolving threat landscape.
In this blog, you will learn how Exeon.NDR, a state-of-the-art Network Detection and Response (NDR) solution, can detect and mitigate such advanced threats using AI-driven analytics, incorporate threat intelligence feeds like MITRE ATT&CK in various network environments.
How Octo2 works
Octo2, the latest version of the Octo malware family, is a trojan that primarily targets Android devices. Octo2 disguises itself as legitimate applications such as Google Chrome or NordVPN and uses a dropper called Zombinder to be installed on devices. Once infected, it enables:
- The interception of push notifications
- Presentation of fake login pages
- Data theft and remote access
Its main “features” include:
One of the core technologies is the DGA, which generates random domain addresses to continuously maintain C2 communication. This makes Octo2 more difficult for security solutions to block and improves its stealth.
What’s new?
- Improved stability for remote access sessions
- Enhanced obfuscation techniques
- A new DGA for C2 communication
- Ability to exploit vulnerabilities in 64-bit Windows versions and Android systems
- Targeted blocking of push notifications from specific applications
All these features make Octo2 particularly dangerous, as it can carry out covert attacks, for instance, on bank customers and evade conventional detection methods.
NDR as the key to detection and prevention
AI-based NDR, like Exeon.NDR, provides, through UEBA, ML, and the use of the MITRE ATT&CK framework, a robust solution to combat advanced threats like Octo2. Here’s how the platform addresses the challenges of such malware:
- Comprehensive network visibility: it provides end-to-end visibility across all layers of network communication, including flow information of encrypted traffic. Exeon.NDR analyzes traffic at the lower layers of the OSI model and IP addresses up to higher layers that include applications and user interactions (e.g., HTTP and DNS at layer 7). This enables comprehensive visibility and data traffic analysis, regardless of the layer used. Even though some content is encrypted, the content of the communication, it uses metadata analysis to monitor the encrypted traffic. It uses so-called flow data (such as NetFlow, sFlow, or IPFIX) and other available metadata independently of the encryption.
- AI-powered behavioral analysis: the solution uses advanced machine learning algorithms to model standard network traffic patterns and detect real-time anomalies. This capability is critical for identifying Octo2’s unusual behaviors, such as using DGA for C2 communication.
- North-South and East-West traffic monitoring: it monitors both North-South traffic (between internal networks and external systems) and East-West traffic (within segmented internal networks). This comprehensive coverage enables the detection of lateral movement attempts, a common tactic used by advanced malware such as Octo2.
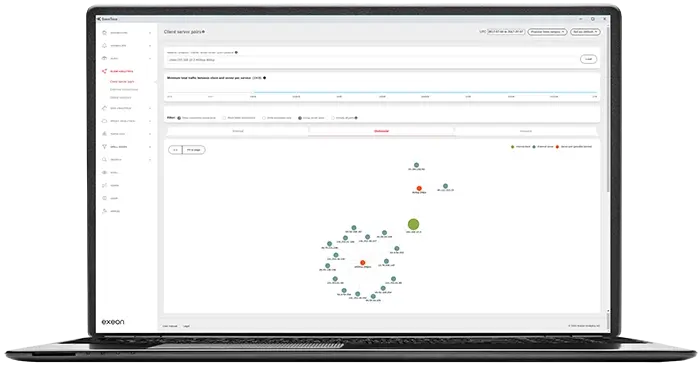
This way, suspicious activities such as unusual connection attempts or data exfiltration can be detected without directly decrypting the encrypted content.
This comprehensive monitoring enables the detection of suspicious activity related to malware such as Octo2, even in encrypted communications.
Facing Octo and co.
As shown, ExeonTrace, as an AI-based solution, provides network visibility and stands out as a defense against modern threats such as Octo2. Through UEBA, ML, and the use of the MITRE ATT&CK framework, it can take the following actions:
- Analyze DGA-based patterns: It can detect suspicious requests based on DGAs by monitoring and analyzing DNS traffic. Algorithms analyze the domain patterns and uncover suspicious communication channels.
- Custom rules for specific network configurations: It can detect anomalies based on particular configuration criteria. Customized analysis and automatic adjustments protect different networks, regardless of their complexity.
- Detection of command and control channels: It identifies C2 communication through anomalies in data traffic, including dynamically generated addresses used by DGAs.
- Automatic adaptation to new threats: ExeonTrace adapts to threats provided by the MITRE ATT&CK database through continuous updates.

Custom analyzers, customizable configurations, and multi-network adaptability
The flexibility of Exeon.NDR allows the creation of custom analyzers tailored to specific threats, such as Octo2:
- DGA detection: we have developed specific analyzers to detect the patterns associated with Octo2’s DGA. These analyzers look for DNS requests to seemingly random domain names, a telltale sign of DGA activity.
- C2 channel identification: Our platform can detect unusual traffic patterns that indicate C2 communication, even if it is obfuscated or encrypted.
- External feed and custom detection detections: Exeon.NDR integrates threat intelligence feeds and custom rules, enabling rapid adaptation to new threat variants such as Octo2.
Exeon’s agentless deployment and ability to work seamlessly with different network infrastructures make it ideal for detecting threats in various environments. Whether in the cloud, on-premise, or hybrid configurations, our solution can customize its detection mechanisms to identify Octo2 and similar threats.
The algorithm-driven threat-scoring engine detects and prioritizes anomalies and threats in real-time. This capability is critical for quickly detecting and responding to high-risk activity related to malware like Octo2.
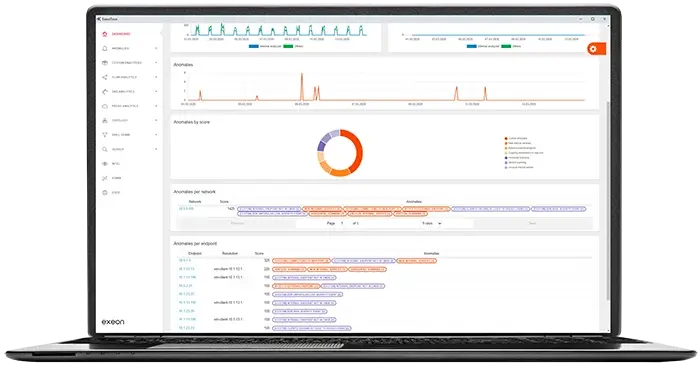
Advantages of NDR:
NDR provides organizations with a powerful tool to neutralize Octo2 threats effectively:
- Real-time detection and the possibility of blocking suspicious communications
- Transparent network monitoring for comprehensive insights into data flows
- Resource-saving implementation that integrates seamlessly into existing systems
- Protection against future variants through adaptive learning algorithms
Conclusion
Octo2 exemplifies the sophistication of modern malware, highlighting the urgency for advanced security solutions. Exeon.NDR leverages MITRE ATT&CK, AI-driven behavioral analysis, and comprehensive network visibility to detect and neutralize threats like Octo2. By identifying DGA patterns, blocking C2 channels, and analyzing activity in real-time, it provides robust protection against evolving threats. Its adaptive platform ensures rapid adjustments to detect new malware variants, keeping organizations secure. With its proactive and structured approach, it empowers businesses to stay ahead in cybersecurity, building resilience against the ever-changing tactics of sophisticated threat actors.
Are you ready to face the threats of APTs? See how Exeon.NDR can help you in this guided detection video.


