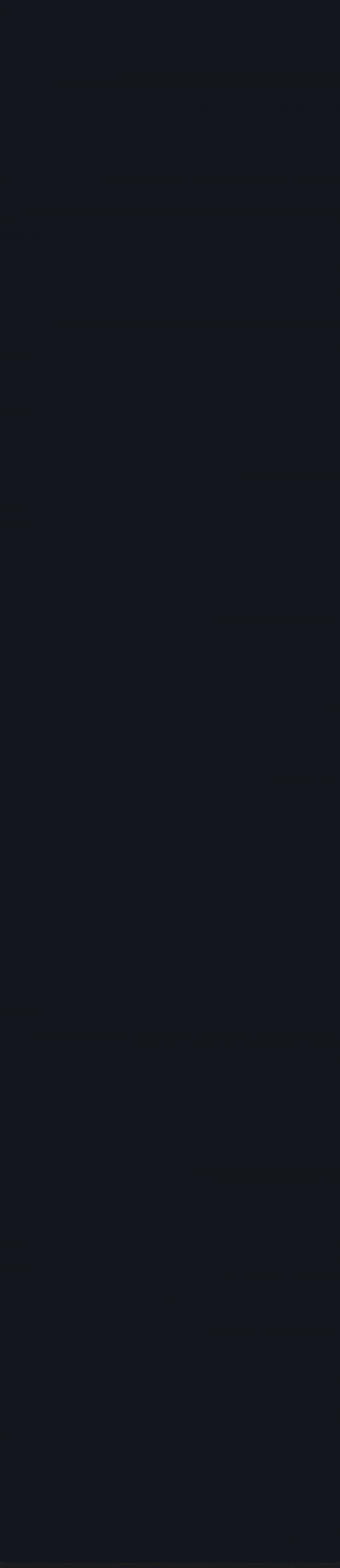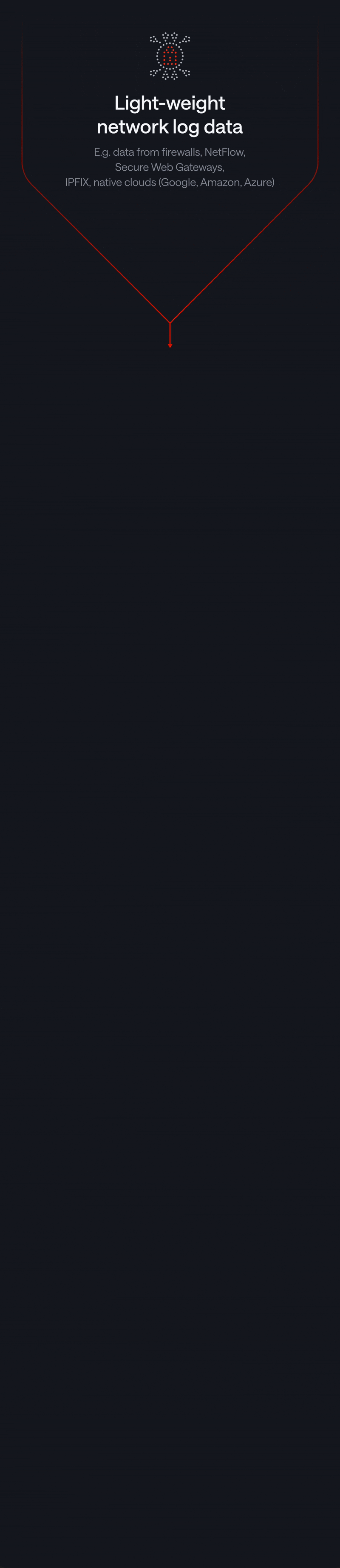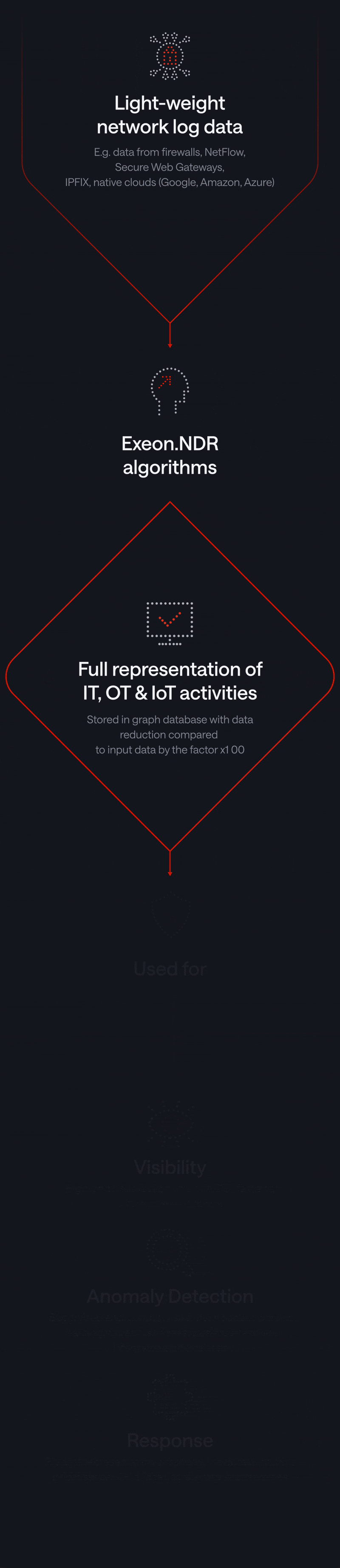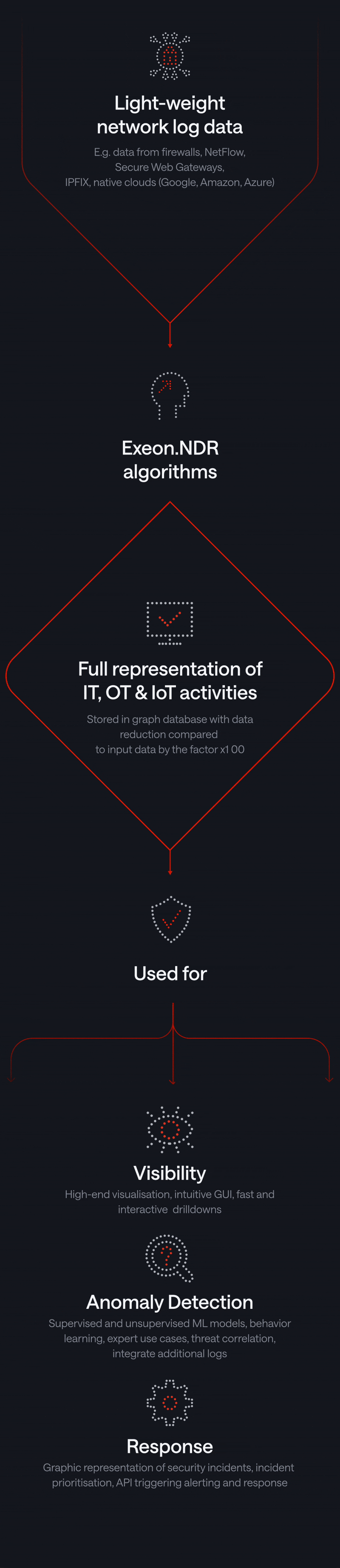
Next-Gen NDR: Lightweight, Performant, Flexible
Our unique Network Detection & Response solution uses AI specially developed for advanced security analysis, relying solely on metadata and guaranteeing sovereignty of sensitive data.
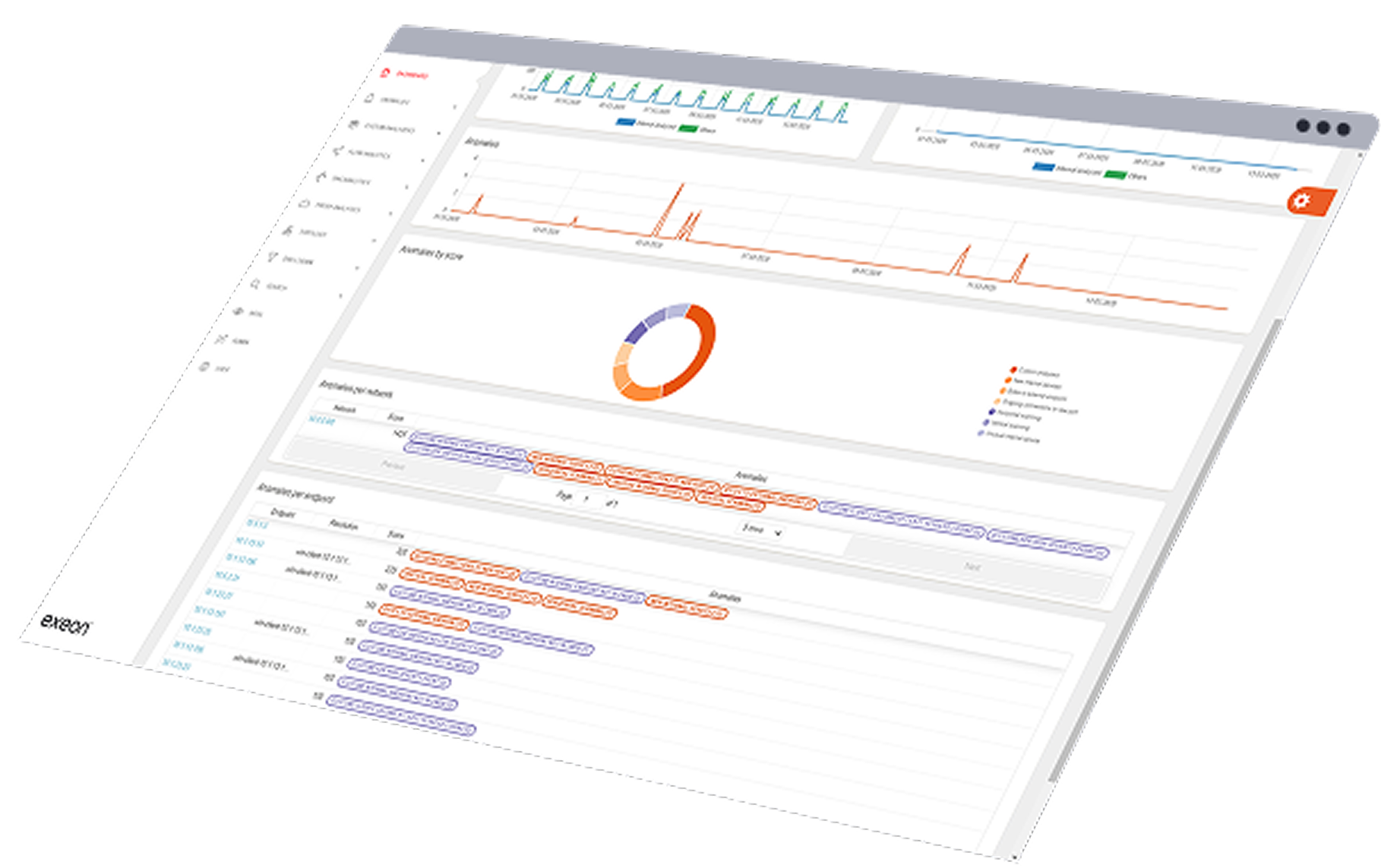
















AI-driven Exeon.NDR empowers threat hunting and detection & response capabilities
Complete visibility
Complete transparency into active devices across IT, OT & cloud infrastructures, enables teams to quickly identify critical threats.
Sophisticated security analytics
We run behavioral detection powered by supervised and unsupervised machine learning to simplify threat detection and uncover zero-day attacks: reduced complexity, increased effectiveness.
Risk-based alerting
All security events are aggregated and correlated to minimize false positives and reduce operational overhead. That way, reliable detection and triage with rich contextual insights ensure your team addresses the most critical attacks first.
Why Exeon.NDR

Powerful AI detection
Pre-built analytics and machine learning models automatically detect threats with minimal false positives. No need to build and maintain custom use cases.
No additional hardware
A software-only solution ready in hours, using existing enterprise infrastructure (firewalls, switches, etc.) as data sources. No additional hardware appliances or network sensors needed.
Holistic visibility
Unify data from routers, switches, firewalls, DNS, proxies, cloud platforms, and applications for detailed visibility of activities anywhere in the network.
Full data sovereignty
Our algorithms provide fast, reliable metadata analysis and are 100% effective on encrypted data. Exeon.NDR ensures flexible deployment – on-premises or in your cloud – with full data compliance.

Exeon.NDR explained
Exeon compared
Exeon eliminates the challenges of deep packet inspection (DPI) via agentless, metadata monitoring with open APIs for scalable log and flow ingestion, transparent ML‑driven custom detection, SOAR/SIEM‑optimized responses, and more.
Capabilities
Lightweight, efficient data analysis without traffic mirroring or sensors
Security analytics unaffected by encryption
Superior network visibility, not restricted to core switch traffic only
Fully on-prem data processing
Transparent Machine Learning models
Exeon
Vectra
Darktrace
ExtraHop
Book a demo.
Precision and excellence into one product: experience the power of metadata analysis with our experts.
Solutions covered by our product
Zero Trust Adoption
Exeon enables effective Zero Trust strategies with metadata and machine learning for comprehensive network security while maintaining 100% data privacy.
- Live metadata processing and ML for immediate threat detection
- Enable least privilege access with precise traffic analysis
- Implement continuous monitoring and auditing
Multi, Hybrid & Cloud Enhancement
Exeon provides unparalleled visibility into multi-cloud network traffic, helping organizations detect and respond to threats across their entire infrastructure.
- Continuous monitoring of network flows across all platforms & environments
- Automated threat hunting and incident response
- Seamless integration with EDR, XDR, SOAR, IPS systems
Compliance
Complex, new regulatory compliance is alleviated with Exeon’s “data privacy first” solution – on-prem, in the cloud, or in sensitive air-gapped networks.
- Enhances compliance by providing full network visibility, anomaly detection, and automated reporting
- 100% network transparency and early detection of advanced threats
- Ensuring adherence to NIS2, ISO 27001, GDPR, and more
Insider Threat Management
A multi-layered approach to detect and mitigate insider threats by leveraging AI-powered Network Detection and User and Entity Behavior Analytics.
- Comprehensive monitoring for full network and application visibility
- Monitors network traffic patterns and can spot anomalous behavior
- Real-time security insights via live dashboards
Exeon.NDR in action
Our technology is engineered to adapt to business specifications and individual requirements without compromising security, efficiency, and compliance.

AI against advanced threats

Guided threat detection tour

On-prem vs. cloud deployment

Less false positives with AI

How AI benefits threat triage
Real-world success stories
Here’s how we provide our unique AI-powered technology to support security teams and managed security service providers in safeguarding corporate and personal data, operations, and reputation.

Network & Security Engineer, Solothurner Spitäler
“Exeon is our cybersecurity alarm system, alerting us to any network anomalies. What also really convinced us is the platform’s intuitive interface—it has become a tool to reliably monitor and secure our data and network.”

CISO, SWISS International Airlines
“As the Swiss national airline, we are driven by a passion for exceptional performance, in the spirit of our guiding principles. A stable and secure IT is the most important basis for an excellent customer service. For the security of SWISS IT, we use Exeon as a central cybersecurity tool, fully managed by our long-term partner Reist Telecom AG. A perfect combination and solution to monitor our network and quickly detect any kind of anomalies.”

ICT Project Leader, WinGD
“Exeon provides us with complete visibility of our network data flows and automatically detects suspicious behavior. Thanks to their AI algorithms, we immediately identify potential cyber threats and can respond quickly and efficiently. This way, we prevent attackers from moving undetected in our systems, infiltrating the infrastructure, or bypassing existing security measures.”

Regional Practice Head, Wipro
“Exeon is the ideal solution for transitioning from a legacy SOC to a Next-Generation SOC. It enhances detection capabilities, minimizes alert noise, and significantly reduces costs.”

Director of Cybersecurity Research, KuppingerCole
“The management and analyst interfaces are intuitive and can yield important insights for customers. Exeon’s approach to data retention helps customers keep data local for regulatory compliance and reduces costs for long-term storage by only retaining event metadata. The solution supports the most pertinent standards for exchanging threat information.”
Frequently asked questions
Learn how Exeon.NDR empowers your IT team with real time network insights and AI driven alerts to spot and stop threats before they cause harm. Our engineers are ready to answer further questions!
Why do you need an NDR solution?
Attackers are concealed within millions to billions of data points, making detection as challenging as finding a needle in the haystack. Network Detection & Response (NDR) has established itself as the leading method for identifying hackers in networks at an early stage before they cause damage. It focuses on monitoring network traffic and analyzing it in real-time to identify suspicious or malicious activities. NDR solutions are proactive in nature, aiming to provide a quick and effective response to potential security incidents. As a result, Network Detection & Response today is becoming the increasingly central pillar of a modern cybersecurity architecture.
Is Exeon.NDR able to analyze log data from Google Cloud Platform (GCP)?
Exeon.NDR can process this log data. It is fully capable of analyzing traffic flowing into and out of Azure, AWS and the Google cloud, providing full visibility into what is happening within the cloud.
Which technologies are used in Exeon.NDR?
The solution leverages supervised and unsupervised ML, predefined use cases, visualizations, and a graph database. Predefined use cases offer a significant advantage over Security Information and Event Management (SIEM) solutions, which can be challenging to implement. The graph database powers the XLOG analyzer.
How much load does the NetFlow export generate on the network?
NetFlow is usually deployed at a central site to provide detailed traffic analysis from remote locations. The ideal deployment depends on network topology and the location of the reporting server. If the reporting server is centrally located, placing NetFlow nearby ensures efficient data processing. Alternatively, enabling NetFlow at remote branches requires bandwidth for data export, typically using 1-5% of switched traffic.
Factsheet
Learn how Exeon.NDR safeguards your IT network with advanced threat detection. Our subscription includes the software license, setup, training, and expert support. Pricing is tailored to your analysis needs and the number of active internal IPs.

Talk to an expert
Let’s discuss your specific requirements – get in touch with us today to learn more about our NDR solution or to discuss your security needs.