Schedule a demo
Powerful machine learning process log data to create enriched security intelligence while greatly reducing data volume and keeping your data 100% confidential.
Swiss engineering of the highest standards; let us show you live!
Can't see the form?
We noticed you may not be able to see our form. This occurs when privacy tools (which we fully support) block third-party scripts.
Firefox users:
Click the shield icon in your address bar → "Turn off Tracking Protection for this site"Chrome with privacy extensions:
Temporarily allow this site in your ad blocker or privacy extension settingsPrefer not to change settings?
Email us directly at contact@exeon.comWe use HubSpot forms for functionality, not tracking. Your privacy matters to us—that's why we're giving you these options.
Unlock deep network security
Custom demo
Discuss solutions to your individual security needs and watch Exeon.NDR in motion.
Proof of value
See the unseen: our experts run the monitoring of your system and find hidden vulnerabilities and risks, cutting through the noise for proactive threat hunting.
Go-live
From day one, you’re protected against known threats and within few days the tool learns your network’s communication patterns, detecting emerging threats through lateral movement and anomalies.
Go-live
From day one, you’re protected against known threats and within few days the tool learns your network’s communication patterns, detecting emerging threats through lateral movement and anomalies.
Why global companies and critical infrastructures trust Exeon
How advanced security analytics change the game
We’re on a daily mission to empower security teams to navigate the most sophisticated threats and safeguard complex, global IT infrastructures with confidence and Swiss precision.
Powerful AI
Built-in supervised and unsupervised AI algorithms detect attacks and identify suspicious network behavior. Its graph database allows for easy customization, enabling users to detect policy violations, misconfigurations, unauthorized traffic, and more.
Future-proof
Our monitoring and detection rely on metadata analysis—not packet payloads. Hence, they won’t be affected by the rapidly increasing traffic encryption and can be deployed in very high-bandwidth networks.
100% Data privacy
We make data protection our #1 priority. As Exeon runs completely within your network or cloud, you remain in full control of your sensitive data, which remains ultralightweight, efficiently stored, and highly scalable.
Watch the Exeon platform in action
No sales pitch—watch our guided threat detection videos to learn why our cybersecurity solution is trusted by large organizations internationally.

Detect Advanced Persistent Threats
In this APT demo, you’ll be walked through initial threat detection, domain generation algorithms (DGA), network scanning activities, machine learning for behavioral analysis, and much more.
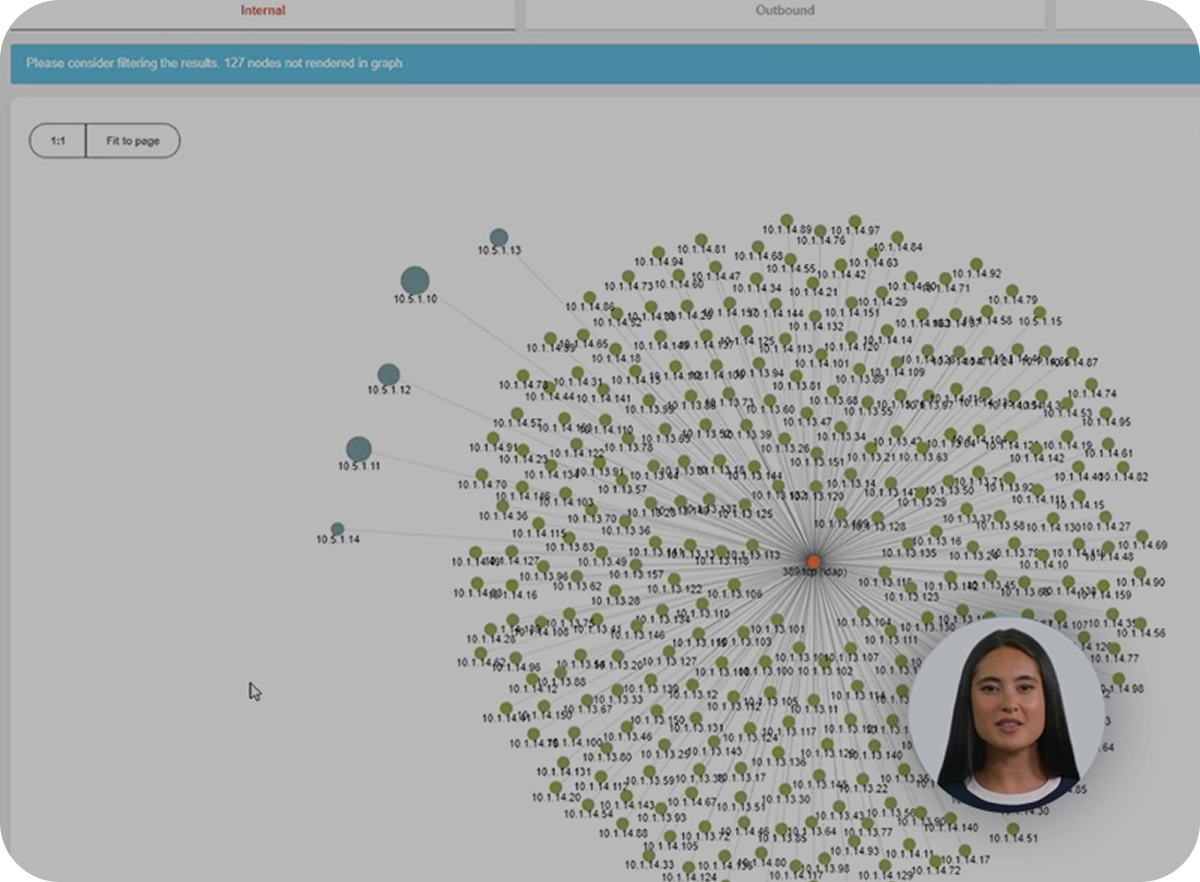
Detect malware attacks in corporate networks
Find out how Exeon.NDR monitors corporate networks, detects anomalies, and assesses security risks. The dashboard provides an overview of anomalies, risk scores, and network activity, while advanced machine learning algorithms help identify threats like malware and scanning behaviors.
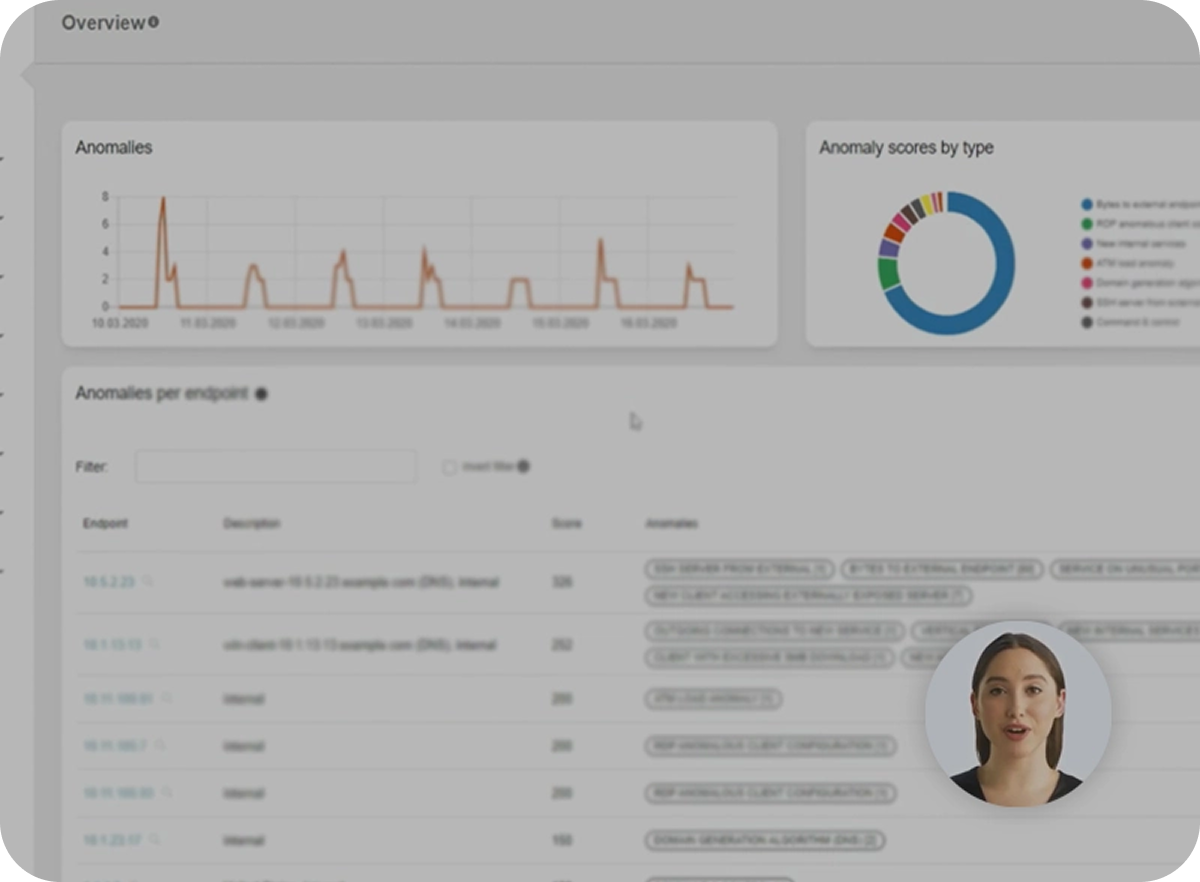
Banking sector: Security monitoring for ATM machines
Watch our unique approach to monitoring OT assets such as ATM machines: an example of how extended logs are used to create custom, new use cases and solve even complex requirements in a very simple way.
We make security teams better
Our customers prioritize protecting their sensitive data and exposed IT and cloud infrastructures. We give them the confidence they need.

Director of Cybersecurity Research, KuppingerCole
“The management and analyst interfaces are intuitive and can yield important insights for customers. Exeon’s approach to data retention helps customers keep data local for regulatory compliance and reduces costs for long-term storage by only retaining event metadata. The solution supports the most pertinent standards for exchanging threat information.”

CISO, SWISS International Airlines
“As the Swiss national airline, we are driven by a passion for exceptional performance, in the spirit of our guiding principles. A stable and secure IT is the most important basis for an excellent customer service. For the security of SWISS IT, we use Exeon as a central cybersecurity tool, fully managed by our long-term partner Reist Telecom AG. A perfect combination and solution to monitor our network and quickly detect any kind of anomalies.”

Head IT Security, PostFinance AG
“PostFinance has chosen Exeon.NDR because of its open and future-proof architecture. Not needing any hardware sensors and being able to control data flows, we didn’t have to make any significant changes to our existing infrastructure. We are also convinced by the cooperation with the competent and technically outstanding Exeon team.”
Exeon in action
Learn how our next-gen analytics empower teams with precision, speed, and efficiency.

Your DORA Checklist

PostFinance Use Case

DORA, NIS2 & KRITIS Guide

DORA Use Case

Detect APTs: Finance Edition
Monitoring ATM Machines
Book a demo.
Schedule a free consultation to see exactly how Exeon can protect your network and infrastructure. No strings attached.
Can't see the form?
We noticed you may not be able to see our form. This occurs when privacy tools (which we fully support) block third-party scripts.
Firefox users:
Click the shield icon in your address bar → "Turn off Tracking Protection for this site"Chrome with privacy extensions:
Temporarily allow this site in your ad blocker or privacy extension settingsPrefer not to change settings?
Email us directly at contact@exeon.comWe use HubSpot forms for functionality, not tracking. Your privacy matters to us—that's why we're giving you these options.
