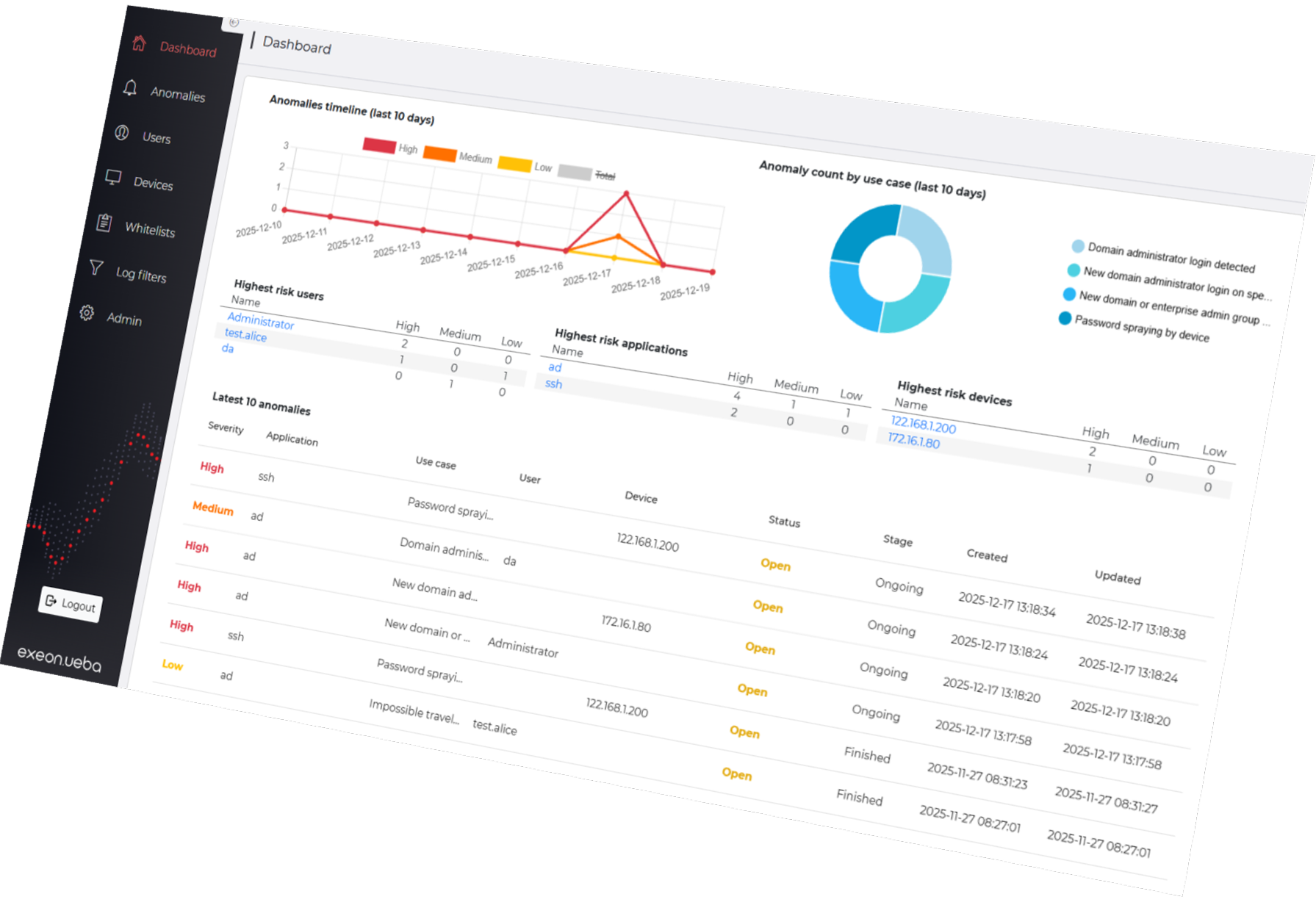
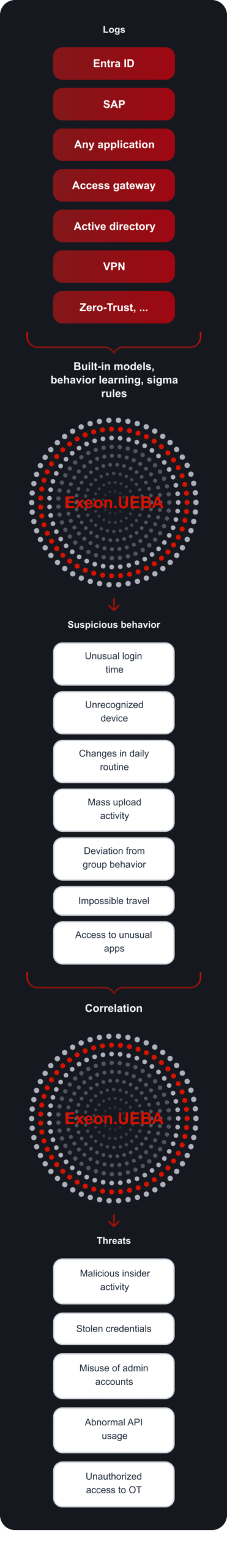
Highly scalable, privacy-compliant User and Entity Behavior Analytics (UEBA)
Modern attackers don’t break in – they log in. Stolen or misused credentials have become the primary entry point into your environment, and traditional defenses struggle to keep up.
Exeon.UEBA provides behavior analytics that detects suspicious activity across all identities and applications – with full data sovereignty.
Why UEBA Matters Today
Identity is the new attack surface
Attackers increasingly use valid credentials instead of technical exploits. Compromised accounts, misused privileges and automated agents enable silent infiltration – often hidden within normal activity. Traditional tools struggle to distinguish legitimate access from malicious behavior.
Modern environments demand another security approach
Cloud services, SaaS platforms and encrypted connections have reduced the effectiveness of deep packet inspection and sensor-based monitoring. Logs are now the most reliable source of truth, and behavior analytics is needed to interpret them.
Fragmented visibility leaves critical blind spots
Many organizations monitor only a handful of standard applications such as Entra ID, while custom apps, legacy systems and business-critical platforms remain largely unobserved. Attackers exploit these gaps by targeting overlooked identities and systems – whether through stolen credentials or insider misuse.
Behavior reveals threats that everything else misses
Detecting deviations in sequence, timing, context and access patterns is now the most effective method to spot identity-driven attacks early. Modern UEBA brings this capability to the entire environment – independent of users, platforms and data volumes.
Why Exeon.UEBA
Easy-to-integrate behavior analytics for identities, applications & data
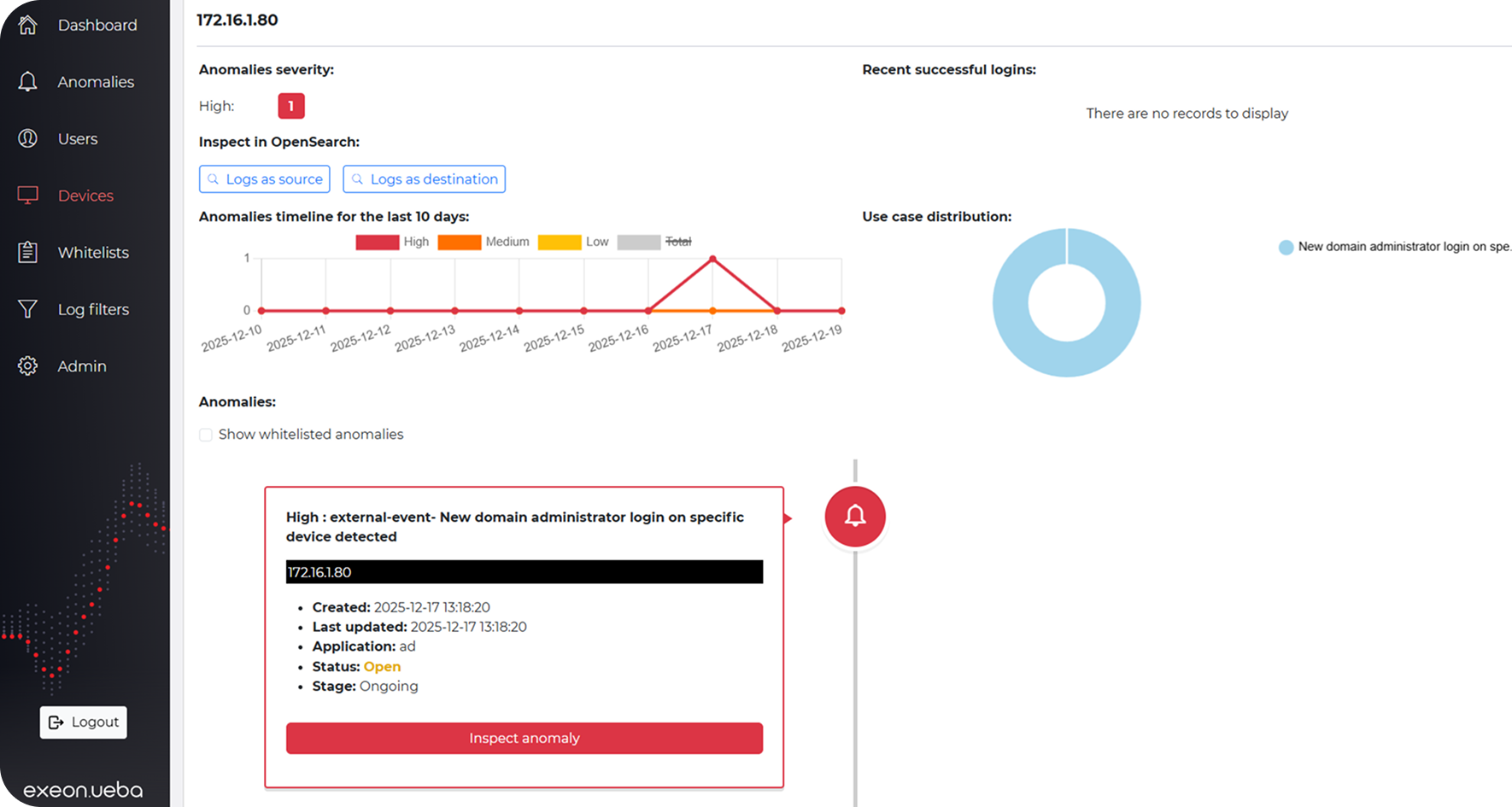
Unified visibility across identities & applications
Monitor all users, entities, apps, APIs, AI agents and legacy systems.
Flexible log onboarding for any application
Standardized log modelling enables fast integration of SaaS, on-prem and custom apps.
Efficient processing for reduced volume & cost
Deduplication, compression and normalization cut log volume and SIEM costs while improving detection efficiency.
Real-time stream processing for instant detection
A high-performance streaming engine, delivering instant alerts also when processing billions of data points.
Dual detection: expert use cases + adaptive AI
Expert-crafted logic is combined with learning-based models to detect subtle anomalies with high accuracy.
Privacy-first, sovereign deployment
Built-in anonymization and encryption with full on-prem or air-gapped deployment options ensure data sovereignty and GDPR-compliant analytics.
The all-in-one behavioral analytics platform for identities, applications & data
Why Exeon.UEBA
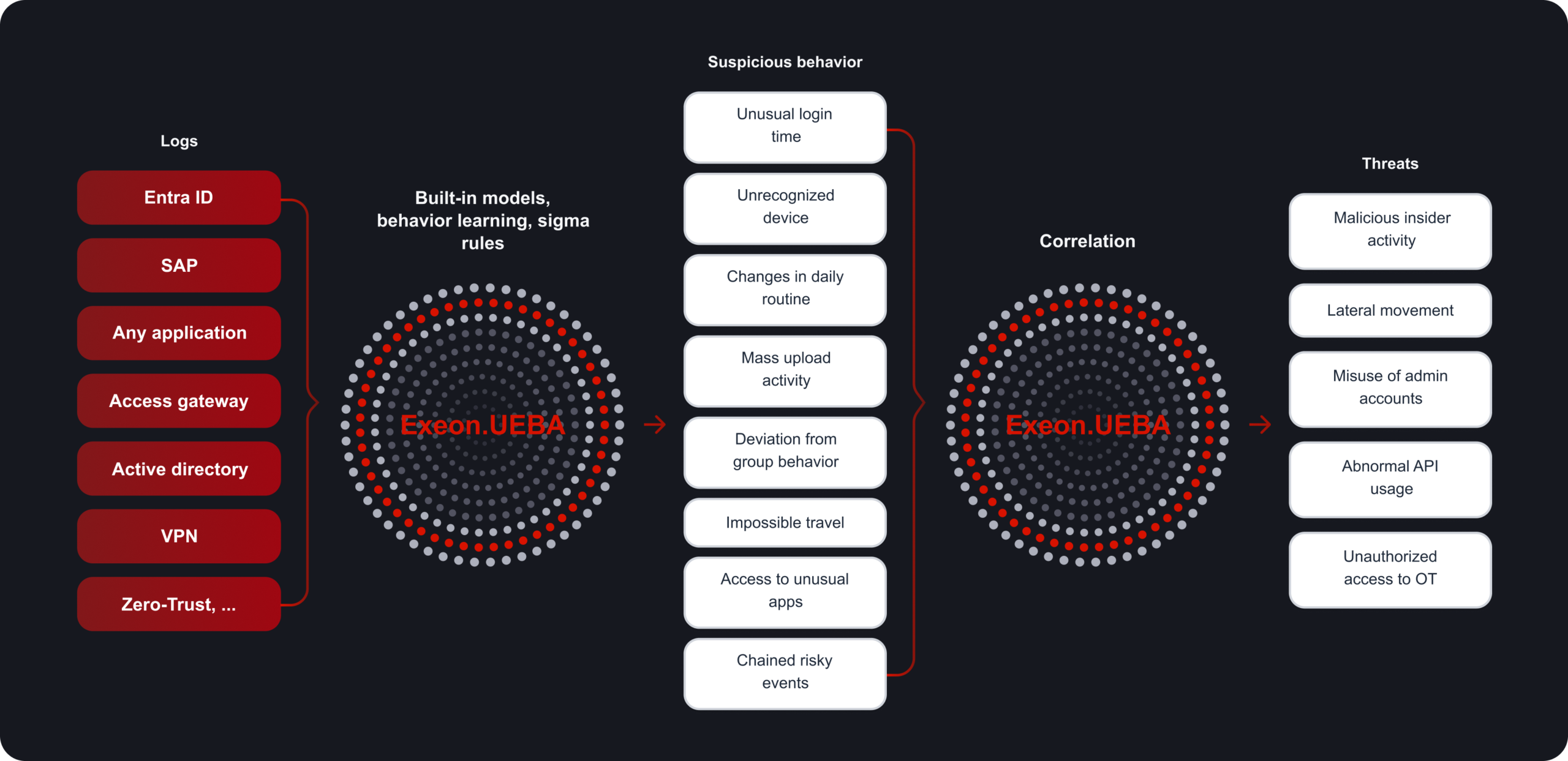
How Exeon.UEBA Works
Built differently – leveraging Exeon’s proven NDR expertise
Comprehensive log collection
Ingest identity, application and system logs from SaaS/IaaS/IAM provider, infrastructure systems and custom-built applications.
Smart data handling
Deduplication, compression and normalization reduce data volumes, improve detection efficiency and lower SIEM/storage costs.
Flexible detection
Combine expert-built behavioral analyzers with custom rules and AI-driven models for unique environments and specialized use cases.
Real-time alerting and automated response
Stream processing delivers sub-second alerts and allows automated containment actions via SOAR, IAM or ticketing integrations.
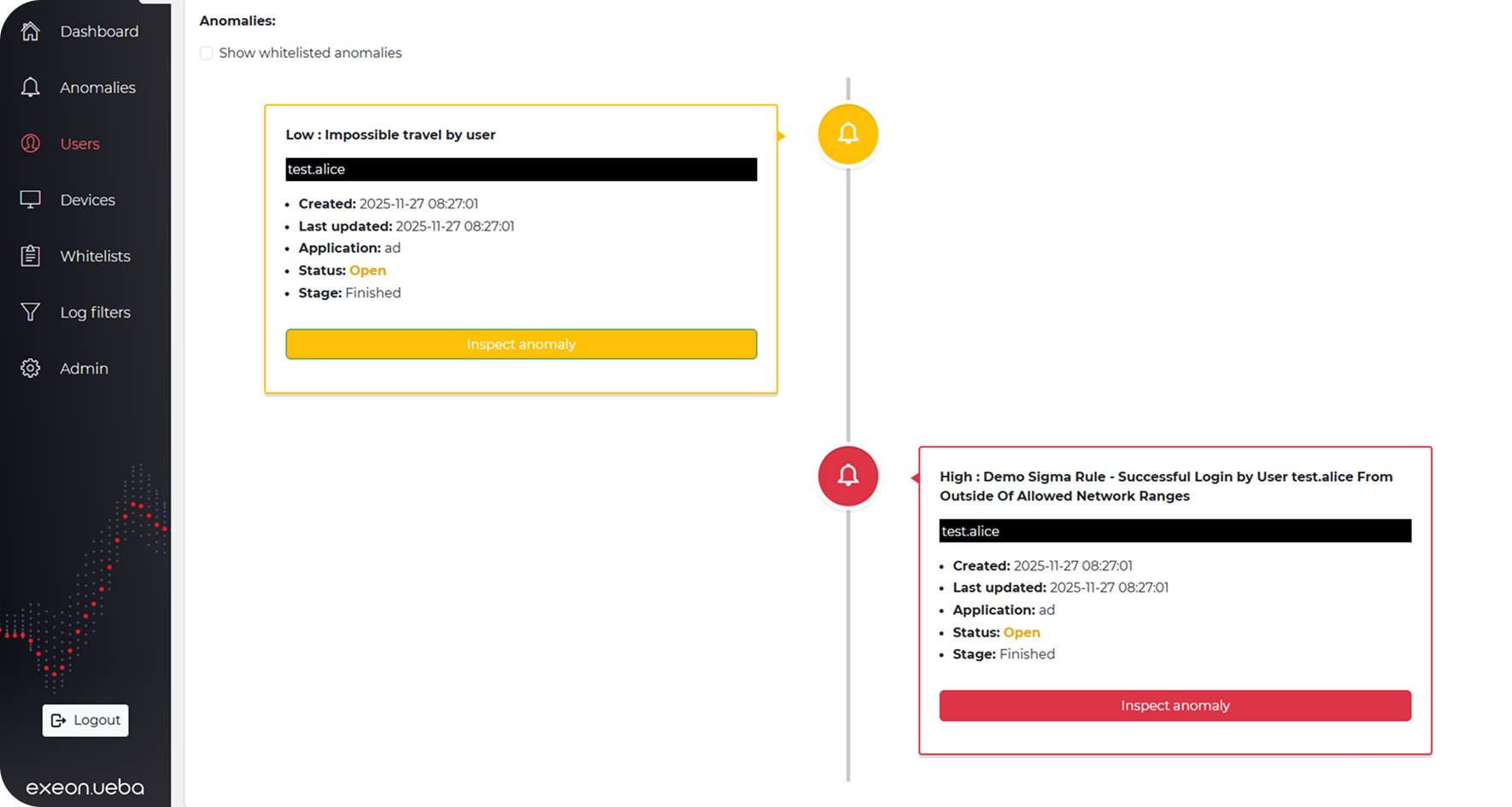
Investigation and behavioral timelines
Unified visibility into user and entity behavior across all systems simplifies investigation and improves analyst efficiency.
How Exeon.UEBA Compares
Approach
No UEBA
UEBA via SIEM
Typical UEBA Tools
Exeon.UEBA
Visibility
Minimal visibility into user/application behavior.
Partial visibility and costly at scale.
Good for standard systems; limited for custom apps.
Complete visibility, including custom apps & APIs.
Detection
Misses credential misuse & insider activity.
Rule-based & batch-
processed; noisy.
Mixed under high load; tuning required.
Real-time, high-fidelity behavioral detection at scale.
Operational Impact
High risk, late detection, no visibility.
Very high data volume and SIEM cost; alert-fatigue and slow response.
Moderate complexity and limited flexibility.
Lower SIEM/storage cost + automated response.
Exeon.UEBA applied to real-world needs
Compromised accounts & stolen credentials
Stolen or misused credentials allow attackers to blend in as legitimate users and move unnoticed through critical systems.
Exeon.UEBA identifies behavioral deviations that reveal compromised users or service accounts before damage occurs.
- Rapid containment before attackers escalate privileges or exfiltrate data
- Exposure of unauthorized activity across applications and APIs
- Fast response to privilege misuse or compromised internal accounts
Application & API Abuse
Business-critical, SaaS and custom-built applications often lack native behavior monitoring, creating exploitable blind spots.
Exeon.UEBA analyzes activity patterns to detect fraud, misuse and exfiltration attempts across all apps and APIs.
- Visibility into how users and services interact with sensitive applications
- Detection of unusual queries, downloads or API sequences
- Protection for custom and legacy systems often overlooked by traditional tools
Insider Threats & Privilege Misuse
Excessive permissions and unchecked access can lead to high-impact incidents – whether intentional or accidental.
Exeon.UEBA uncovers misuse of privileges and risky behavior inside sensitive systems.
- Identification of unusual actions by privileged or internal users
- Detection of unauthorized changes, access spikes or data handling
- Prevention of misuse that could expose confidential information
AI & Automation Misbehavior
AI agents, bots and automated service accounts increasingly access sensitive data – often without sufficient oversight.
Exeon.UEBA monitors their behavior to detect compromise, misuse or unintended actions early.
- Detection of abnormal or excessive activity from AI or automated identities
- Recognition of privilege escalation or unauthorized data access
- Prevention of harmful automation loops or AI-enabled exfiltration
Exeon.UEBA in action
Modern attacks hide within normal identity and application activity.
Exeon.UEBA uncovers these threats early by analyzing behavior across all users, applications and entities.

How AI benefits threat triage

Less false positives with AI

On-prem vs. cloud deployment

Guided threat detection tour

Your DORA Checklist

PostFinance Use Case

DORA, NIS2 & KRITIS Guide

DORA Use Case

Detect APTs: Finance Edition
Monitoring ATM Machines

NIS2 Compliance Checklist

NIS2, DORA & KRITIS Guide

DORA Compliance Checklist

DORA Banking Use Case

NIS2 Manufacturing Use Case

Use Case: Bank in Germany

Success Story: Logistics

Exeon.NDR for IT, OT & IoT

Success Story: Banking

Use Case: Manufacturing & NIS2

Success Story: Swiss Hospitals

Use Case: Healthcare & Compliance

Zero Trust in the finance sector

Meeting the unique needs of OT

From patient data to regulatory compliance

Financial sector applications

Made for the industrial world

Secure patient data & compliance

Public security, private data protected

AI against advanced threats

Global Manufacturer WinGD

Public Sector Use Case

Finance & Insurance

Manufacturing & Industrial

Public Sector
Exeon
across industries
Modern environments differ in structure, regulation and risk – but identity-driven threats affect all of them.
Exeon.UEBA provides tailored behavioral visibility for every sector.

Finance & Insurance
Monitor privileged identities and sensitive workflows across core banking, trading, payment and AI-enabled platforms.

Manufacturing & Industrial
Protect production, R&D and engineering systems across hybrid OT/IT environments.

Public Sector
Operate with complete data sovereignty and strict privacy controls. Exeon.UEBA detects identity misuse and privilege escalations...
What customers say about Exeon.UEBA
Organizations in highly regulated and high-security environments rely on Exeon to gain behavior visibility and protect sensitive applications and identities. Exeon.UEBA builds on the same proven analytics foundation trusted by the public sector, financial institutions, critical infrastructure providers, utilities, and military organizations.
Situation
Organizations operating large, complex environments with thousands of identities and a mix of standard, SaaS, and highly customized business applications.
Their SIEMs typically struggle to reveal subtle behavioral anomalies, and existing tools cannot handle the high log volumes or the strict data sovereignty requirements.
Critical user, application and service-account activities remain blind spots.
Solution
Exeon.UEBA can be deployed in fully sovereign environments – including full on-prem setups – ingesting logs from core systems, identity platforms, financial applications, APIs and custom-built tools.
Log data is transformed into a standardized model, enabling real-time behavior analytics across users, entities and applications while keeping identity data protected through anonymization and encryption.
Outcome
- Full visibility into previously unmonitored “crown-jewel” applications
- Fast rollout – operational within hours, not days
- Significantly reduced SIEM data volume and operational cost
- Improved focus and response through high-quality, behavior-based alerting
Impact
- Threat detection coverage of ALL applications
- Log data volume & cost reduction
- Fast start: Operational within hours
Frequently asked questions
Discover how Exeon.UEBA delivers complete visibility into user and entity behavior to spot compromised accounts, insider risks and suspicious application activity instantly. Our experts are happy to help with any additional questions.
What is UEBA and how does Exeon.UEBA work?
User and Entity Behavior Analytics (UEBA) detects threats by analyzing how identities, applications and services normally behave.
Exeon.UEBA ingests logs from all systems, builds behavioral baselines and identifies anomalies in real time.
Which log sources does Exeon.UEBA support?
Exeon.UEBA supports any log source, including SaaS, on-prem, legacy and custom applications.
It also integrates identity providers (e.g., AD, Entra ID), VPN/ZTNA/SASE systems, APIs, AI agents and infrastructure components.
Does Exeon.UEBA work with custom or proprietary applications?
Yes. Custom log collectors and a flexible normalization pipeline allow Exeon.UEBA to ingest and analyze logs from any custom-built system, without additional development.
How does Exeon.UEBA ensure data privacy for users and identities?
Sensitive identity attributes – such as usernames, IDs or email addresses – can be anonymized or encrypted at ingestion.
This ensures that behavior analytics operates on protected data while still maintaining detection quality and full analytical context.
Which deployment options does Exeon.UEBA support?
Exeon.UEBA offers full flexibility:
- On-premises for maximum data sovereignty
- Private cloud deployments (customer-controlled)
- Hybrid models combining on-prem and cloud components
All options are designed for regulated environments and strict internal compliance requirements.
How does Exeon ensure data sovereignty?
Exeon.UEBA can be deployed entirely within the customer’s infrastructure, with no dependency on external clouds or external data processing.
Customers retain full control over log data, identity data, storage, access rights and operational boundaries – meeting the sovereignty requirements of the public sector, critical infrastructure and regulated industries.
Does Exeon.UEBA detect insider threats?
Yes. Exeon.UEBA identifies abnormal access, unusual data usage, privilege misuse and suspicious patterns typical of insider attacks – even when activity looks legitimate. It leverages pre-built use case detection rules which are based on more than a decade of experience, custom detection patterns and combines this with AI-based behavioral detection.
What is the difference between Exeon.UEBA and UEBA features inside a SIEM?
SIEM-based UEBA is often rule-driven – which need to be manually added and tuned – and limited by batch processing and high data-ingest costs.
Exeon.UEBA uses real-time streaming analytics, smart log pre-processing for decreased data volumes and flexible behavior models to deliver faster, more accurate detection at lower cost.
Does Exeon.UEBA integrate with SIEM, SOAR and IAM tools?
Yes. All detections and context can be forwarded to existing SIEM, SOAR or ticketing systems.
Automation options (e.g., user/session isolation) are available through standard API integrations.
How fast can Exeon.UEBA be deployed?
Most customers achieve meaningful visibility within days, thanks to direct log ingestion and a standardized data model.
No endpoint agents, network sensors or specific log formatting tools are required.
What attack types does Exeon.UEBA detect?
Exeon.UEBA identifies any suspicious entity behavior including account compromise, insider threats, privilege misuse, or data exfiltration across applications, API misuse and abnormal activity from AI agents or service accounts.
Ready to optimize your SOC?
Your cybersecurity is our priority. Connect with us to discuss how our AI technology enhances protection, boosts efficiency, and reduces costs.
