For many organizations, an in-house or managed security operations center (SOC) plays a critical role in monitoring and defending against cyber threats. It is essential for organizations because it provides continuous monitoring, rapid threat detection, and effective response to protect against attacks. Its proactive approach enhances cybersecurity by identifying and mitigating potential risks, ensuring the overall resilience of the organization’s digital infrastructure.
However, as with any human- or machine-operated system, there is always the potential for error.
Some Common Mistakes of a (Managed) SOC:
- Incomplete visibility:
Missing critical network traffic and events due to incomplete monitoring or lack of visibility into certain areas of the network.
- Incomplete log analysis:
Failure to analyze and correlate all relevant logs, leaving blind spots in the detection capabilities.
- False positives/negatives:
Generating too many false positives (misidentifying normal activity as malicious) can lead to alert fatigue, while false negatives (missing actual threats) can be a significant security risk.
- Slow or ineffective incident response:
Mistake: Delayed or inadequate response to security incidents can lead to prolonged exposure to threats, increased damage and longer recovery times.
- Lack of context:
Failing to understand the context of security events, which can lead to misinterpretation and mis-prioritization of incidents.
- Over-reliance on automation:
Relying too heavily on automated tools without proper human oversight can result in missing nuanced threats that may require human analysis.
- Failure to keep up with threat intelligence:
SOC analysts need to stay informed about the latest threat intelligence to effectively detect and respond to emerging threats. Failing to do so can result in outdated defenses.
The One Thing That Helps Prevent SOC Failures

Network Detection and Response (NDR) solutions continuously monitor the flow of network traffic to promptly detect and address threats, ensuring the immediate identification of security incidents. These solutions provide a comprehensive view of network activity by examining data from multiple sources, including logs, packets, assets, and flows, so that no part of the network is overlooked.
By identifying normal network behavior and detecting anomalies, NDR tools can effectively prioritize and alert on potential malicious activity with increased accuracy.
Using advanced analytics and machine learning, tools such as Exeon.NDR, the Swiss platform, can significantly minimize false positives. The integration of threat intelligence feeds ensures that the Security Operations Center (SOC) has up-to-date information on known threats. This integration improves the ability to detect and respond to evolving attack techniques. NDR solutions complement human expertise by automating specific tasks and providing context to alerts.
NDR Now & Beyond
In the cybersecurity landscape, the importance of Network Detection and Response tools, exemplified by advanced solutions like Exeon.NDR, cannot be overstated. By harnessing the potential of analytics and machine learning algorithms, these tools are ushering in a new era of threat detection and incident response capabilities. A key benefit of NDR tools is their unparalleled ability to minimize false positives, a persistent challenge in traditional security setups.
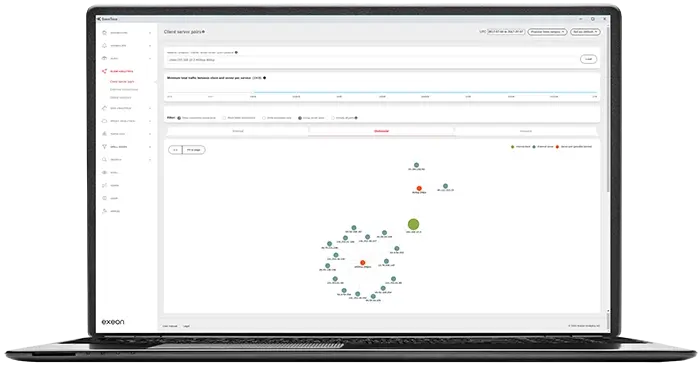
Exeon.NDR goes beyond traditional threat detection methods by meticulously monitoring and analyzing network behavior.
By establishing a baseline of normal activity, these tools can quickly identify and highlight deviations from the norm.
As a result, potential threats can be prioritized with an accuracy that surpasses legacy security protocols, resulting in a more streamlined and efficient cybersecurity posture where security teams can focus on the most critical alerts.
Summary
Common deficiencies in a SOC/managed SOC include incomplete visibility, insufficient log analysis, false positives/negatives, slow response to security incidents, lack of context, over-reliance on automation, and lack of up-to-date threat intelligence.
NDR solutions enhance the capabilities of a SOC or managed SOC by providing greater visibility, reducing false positives, enabling rapid incident response, integrating threat intelligence, and ensuring continuous monitoring.
The adoption of NDR tools like Exeon represents a pivotal step towards bolstering an organization’s cybersecurity defenses. These tools, with their advanced analytics, machine learning capabilities, and seamless integration with threat intelligence, offer a comprehensive solution to the evolving landscape of cyber threats. As organizations strive to stay one step ahead of adversaries, NDR tools emerge as indispensable allies in the ongoing battle for digital security. Are you ready for the year to come? How are your current security measures holding? Let’s talk!


