Introduction
In an increasingly connected world, the protection of Operation Technology (OT) networks is critical. The merging of IT and OT environments requires a comprehensive approach that should be compliant with regulatory frameworks such as the Network and Information Systems (NIS) Directive and the Digital Operational Resilience Act (DORA).
The Zero Trust principles provide a structural approach to securing IT and OT networks and already fulfill many of the requirements of the NIS and DORA regulations. By implementing Zero Trust, organizations can strengthen their cyber resilience, protect critical infrastructure and mitigate the impact of cyber threats. This blog explores the importance of applying regulatory compliance considerations and cyber-strategic principles to OT networks from a Zero Trust perspective to improve the overall security posture.
Understanding the Regulations
KRITIS and BSIG
The cybersecurity regulations governing Critical Infrastructures (KRITIS) and their network security requirements, particularly in the realm of OT, are diverse and jurisdiction dependent. One such regulation is the BSI-KritisV (Regulation on the Protection of Critical Infrastructures) in Germany, which mandates precise security measures for critical infrastructure operators, including risk management, incident reporting, and setting minimum security standards. Specifically, § 8a para. 1 of the Federal Act on the Protection of Critical Infrastructures (BSIG) imposes specific security requirements on critical infrastructure operators (KRITIS), emphasizing the establishment of adequate organizational and technical measures to safeguard information technology systems.

NIS2 and DORA
In the European Union, the Network and Information Systems Directive (NIS) plays a crucial role in enhancing cybersecurity and resilience in critical infrastructure. Its successor, NIS2, further strengthens cybersecurity practices among operators of essential services and digital service providers. NIS2 mandates collaboration between national authorities and operators to bolster the cybersecurity landscape in the EU, with a focus on sectors such as managed services and secondary activities. Compliance with national laws is essential due to potential variations from NIS2 provisions.
Financial institutions, however, are not subject to NIS2 requirements, as outlined in Section 28 BSIG-E (NIS2UmsuCG). They must adhere to DORA, a European legal framework aimed at improving digital operational resilience, particularly in the financial industry. DORA sets uniform requirements across all EU Member States, ensuring organizations can withstand, respond to, and recover from ICT-related disruptions and threats.
Some companies in the IT and telecommunications sector may face dual regulation under both DORA and NIS2 if classified as NIS2 establishments and categorized as critical ICT third-party service providers under DORA. This includes cloud providers, telecommunications solution providers, and managed services providers. Even group-internal IT service providers are not exempt from potential obligations under both DORA and NIS2.
Outside the EU, Switzerland passed an amendment to the Information Security Act on September 29, 2023, introducing a reporting obligation for cyberattacks on critical infrastructure. The amendment mandates the National Cyber Security Center (NCSC) to conduct technical analyses, process reports, inform manufacturers of vulnerabilities, and publish relevant information to protect Switzerland from cyber threats.
Why Zero Trust?
The Zero Trust principles are critical to improving network security. They include restricted trust assumptions, restricted user rights, “always-on” preparing for security incidents, and improving threat detection. Implementation requires comprehensive network monitoring, ongoing user identity checks, prevention of unauthorized lateral movement, and rapid threat detection and containment.
Zero Trust provides a solid framework for secure networks but requires constant vigilance against potential attacks and rapid response to anomalies. Monitoring, including encrypted traffic, is essential for security, but requires a balance between inspection and privacy standards.
Challenges in Applying Zero Trust to OT Networks
The convergence of IT and OT brings about significant changes and challenges in managing organizational infrastructure. IT encompasses the management of devices and systems, while OT focuses on manufacturing and technical operations, usually overseen by the Chief Technology Officer. OT assets consist of specialized equipment like programmable logic controllers (PLCs), which interact with physical sensors to regulate industrial processes. These assets often communicate via distinct protocols and are segregated into separate networks to prioritize availability and safety over confidentiality.

In critical infrastructure domains, uninterrupted communication is prioritized, leading to the development of Industrial Control Systems (ICS) communication protocols often lacking common IT security measures. Current industrial protocols, like the Inter-Control Center Communications Protocol (ICCP), enable communication between OT assets via TCP/IP and potentially with conventional IT assets.
IT environments often manage and configure OT devices, serving as hubs for data collection, normalization, processing, and reporting crucial for effective OT asset management. However, the migration of IT assets to cloud-based environments exposes OT assets to new cybersecurity challenges.
OT environments present unique risks due to aging platforms, proprietary protocols, safety-security trade-offs, and complexities in cloud migration, resulting in gaps in access management and associated risks. As IT transitions to hybrid environments incorporating on-premises and cloud services, traditional perimeter-based security measures become outdated.
Addressing these challenges requires enhanced risk reduction strategies and third-party access monitoring. Organizations must adopt a holistic approach to cybersecurity, integrating IT and OT security measures to ensure the resilience and protection of critical infrastructure in the face of evolving threats and technological landscapes. This entails implementing robust authentication, monitoring, and access control measures across both IT and OT environments while fostering collaboration between IT and OT teams to address emerging cybersecurity challenges effectively.
Implementing a NIS2-Compatible Architecture
Implementing an NIS2-compatible architecture in IT, IoT, and OT environments presents significant challenges due to the unique characteristics of OT equipment and its specific safety requirements, often hindering seamless integration with security standards: As described above, NIS2 for OT faces cybersecurity challenges due to its insecure design, prioritization of availability over security, lack of security mechanisms, outdated infrastructure, and inadequate inventory and management practices, exacerbating cybersecurity concerns.
And DORA? The second block of the DORA framework for the financial cyber-resilience, focuses on cyber risk management and begins with an assessment of the existing IT and cyber maturity level, followed by an assessment of security gaps due to IT/OT coupling and the according threat scenarios.
In this area, exercise concepts such as tabletop exercises and threat-oriented penetration tests are offered to simulate real cyber-attacks. The principles of DORA also explicitly extend to IoT devices and systems in critical infrastructure or financial services, with a focus on operational resilience, security and continuity. Recognizing the importance of OT, DORA addresses ICT-related risks in OT environments and emphasizes the need for comprehensive capabilities to ensure the continuous delivery of financial services in the event of disruption.
Zero Trust at Work

The Zero Trust Network Access (ZTNA) approach is a comprehensive strategy to address compliance challenges covering all from IT, OT to IoT. In line with DORA and NIS2, ZTNA is a bulwark against evolving cyber threats that strengthens cybersecurity measures and ensures compliance with critical infrastructure protection regulations.
As ZTNA places distrust and verification at its core. It represents a paradigm shift from traditional, perimeter-centric defense approaches to a proactive security framework, in line with modern security requirements that demand careful scrutiny of all organizations and data flows to mitigate risk: ZTNA promotes continuous monitoring of network traffic and user activity, which is also reflected in the DORA and NIS2 regulations that rely on continuous monitoring and compliance reporting too. By implementing the ZTNA principles, organizations should gain detailed insight into their network activity and comply with regulatory requirements. ZTNA supports a risk-based approach to access control which enables dynamic access decisions based on user identity, device health and contextual information, aligned with the themes of DORA and NIS2.
In addition, ZTNA emphasizes the importance of rapid incident detection and response to mitigate the impact of security breaches. ZTNA urges organizations to improve their incident response capabilities by quickly detecting and containing security incidents to limit the potential impact on critical business processes. It advocates a mindset that assumes malicious actors have already breached defenses, which is a departure from traditional paradigms based on blind trust.
Practical steps for implementing a robust, ZTNA, NIS2 and DORA-enabled architecture include:
- Visibility: Understand application and workload communication.
- Segmentation: Control remote connections and lateral movement.
- Monitoring: Use analytics for threat detection.
Network-related protection applications, such as firewalls and intrusion prevention systems (IPS), are only the basics for meeting security requirements in both IT and OT environments. However, as attackers increasingly target industrial areas, the ability to analyze traffic without inspecting the data packets itself e.g. for industrial protocols like Modbus becomes crucial. While Security Information and Event Management (SIEM) solutions can collect logs from various assets, they may not provide a comprehensive view of network and host activity in OT environments.
Network defense is a complementary measure to endpoint protection and a critical step in mitigating undetected vulnerabilities, when endpoint protection faces challenges in OT-based production facilities, due to technical limitations and warranty restrictions, resulting in many devices operating without adequate protection.
How an AI-powered Network Detection and Response (NDR) system addresses challenges in (co-)monitoring OT security and ensures compliance
An NDR like Exeon.NDR leverages machine learning to detect and respond to network threats. It establishes normal patterns in network traffic and identifies deviations that may indicate malicious activity. While most network traffic is now encrypted, ExeonTrace monitors and analyzes network communication and uses AI and machine learning to enhance threat detection.
Files traversing the network are often encrypted and cannot be easily decoded through passive monitoring.
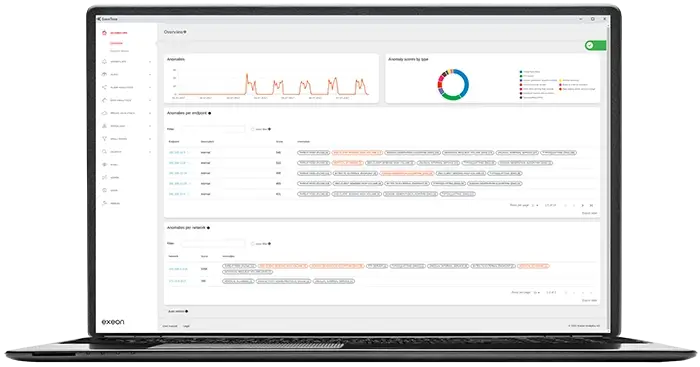
Exeon.NDR recognizes file traversal patterns across the network, even in encrypted environments by analyzing their behavior to enhance visibility and threat detection.
Traditional NDR solutions rely on traffic mirroring, which becomes challenging due to increased encryption, distributed IO and OT networks, and higher bandwidths. Exeon avoids this limitation by analyzing lightweight log data instead of relying solely on traffic mirroring. It collects metadata from existing network sources (such as switches and firewalls) without needing hardware sensors. And its open and future-proof architecture allows easy deployment without major changes to existing infrastructure.
Exeon provides comprehensive visibility, efficient threat detection, and rapid incident response and it aligns with NIS2 and DORA requirements by continuously monitoring IT, cloud, and OT networks. It detects anomalies, prevents attackers from moving undetected between environments, and strengthens overall cybersecurity and the absence of hardware appliances simplifies deployment and maintenance, ensuring scalability and compliance.
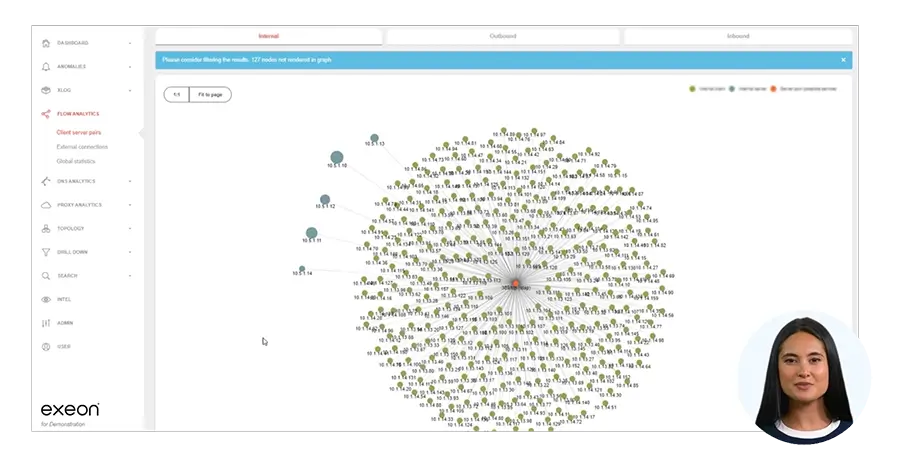
See OT detection in action
Ready to experience NDR and see how Exeon can detect anomalies and potential cyber threats throughout your entire network? Watch our video tour!


