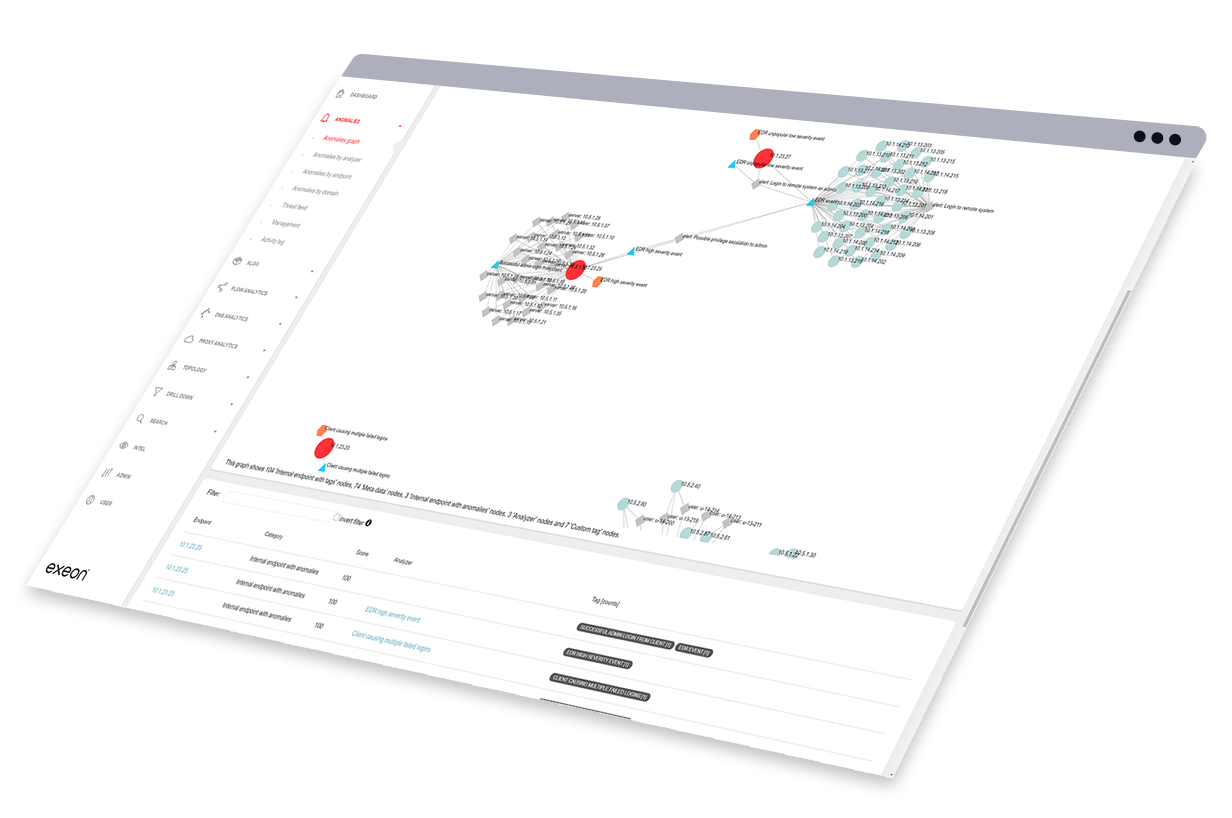
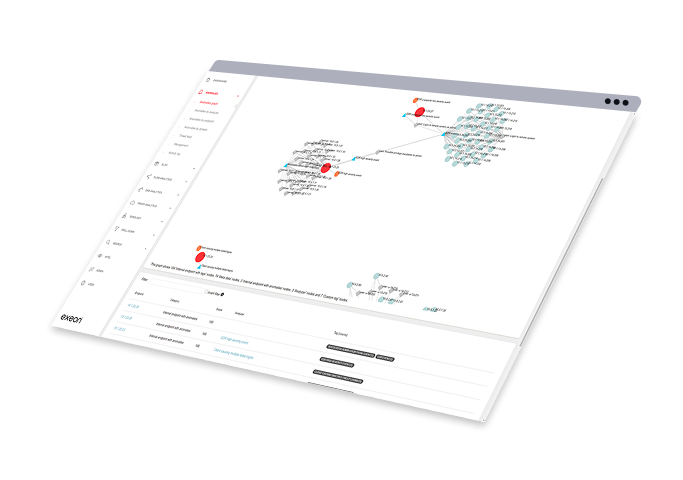
Full Network Visibility Without Decrypting Traffic
How rising encryption is challenging security monitoring
of traffic is encrypted nowadays, rendering traditional DPI-based solutions of lower effectiveness.
of organizations admit encryption hampers monitoring and issue detection, increasing blind spots.
anticipate quantum threats by 2030 and the hacker’s potential to break current data encryption methods.
Organizations will find themselves balancing comprehensive network visibility and threat detection with increasingly encrypted environments while dealing with challenges of privacy, compliance, and performance across hybrid IT/OT infrastructures.
Blind spots
Some traditional inspection tools can’t read encrypted traffic, leaving whole portions of your estate unmonitored and exploitable.
Added complexity
Adopting Zero Trust increases complexity and reduces visibility — especially with encrypted traffic. Exeon restores context through metadata analytics, enabling policy enforcement without deep packet inspection.
Alert fatigue, skill gaps
Security teams face massive data volumes, fragmented dashboards, and a shortage of skilled analysts — all while encrypted traffic further limits visibility, making it even harder to distinguish real threats from background noise.
Agentless deployment
Protect privacy, skip DPI
Compatible across all environments
Seamless integration
Trusted by the world's best companies















How to achieve secure, scalable monitoring with Exeon
Seamless integration across environments
Fit into IT, OT, cloud, and hybrid infrastructures, ensuring compatibility with both legacy and modern systems.
Effortless deployment with agentless monitoring
Utilize the network’s existing capabilities like Netflow or IPFIX for non-intrusive monitoring, eliminating the need for new sensors and reducing costs.
Compliance without decryption
Analyze network metadata instead of decrypting traffic, preserving privacy while meeting regulatory standards.
Optimized real-time performance
Enable high-speed, low-latency monitoring by avoiding resource-intensive decryption processes.
Future-proof security against growing encryption
Maintain continuous threat visibility with advanced metadata analysis as encryption adoption rises.
Bridging IT & OT security gaps
Detect anomalies across all network segments, ensuring comprehensive visibility and protection.
Exeon.NDR in action

Your DORA Checklist

PostFinance Use Case

DORA, NIS2 & KRITIS Guide

DORA Use Case

Detect APTs: Finance Edition
Monitoring ATM Machines
What our customers say

CISO, SWISS International Airlines
“As the Swiss national airline, we are driven by a passion for exceptional performance, in the spirit of our guiding principles. A stable and secure IT is the most important basis for an excellent customer service. For the security of SWISS IT, we use Exeon as a central cybersecurity tool, fully managed by our long-term partner Reist Telecom AG. A perfect combination and solution to monitor our network and quickly detect any kind of anomalies.”

Head IT Security, PostFinance AG
“PostFinance has chosen Exeon.NDR because of its open and future-proof architecture. Not needing any hardware sensors and being able to control data flows, we didn’t have to make any significant changes to our existing infrastructure. We are also convinced by the cooperation with the competent and technically outstanding Exeon team.”

CEO & Founder, Planzer
“As CEO and owner of a fast moving, international logistics company, I cannot afford any system interruptions due to cyber incidents. With Exeon.NDR, we have found a Swiss solution to monitor our network and quickly detect cyber threats.”

Head Infrastructure & Applications, 3 Banken IT
“We especially appreciate the comprehensive network visibility that Exeon.NDR offers us.
The anomaly detection is also extremely accurate and allows our analysts to focus on the essential threats.”

Director of Cybersecurity Research, KuppingerCole
“The management and analyst interfaces are intuitive and can yield important insights for customers. Exeon’s approach to data retention helps customers keep data local for regulatory compliance and reduces costs for long-term storage by only retaining event metadata. The solution supports the most pertinent standards for exchanging threat information.”

Network & Security Engineer, Solothurner Spitäler
“Exeon is our cybersecurity alarm system, alerting us to any network anomalies. What also really convinced us is the platform’s intuitive interface—it has become a tool to reliably monitor and secure our data and network.”

ICT Project Leader, WinGD
“Exeon provides us with complete visibility of our network data flows and automatically detects suspicious behavior. Thanks to their AI algorithms, we immediately identify potential cyber threats and can respond quickly and efficiently. This way, we prevent attackers from moving undetected in our systems, infiltrating the infrastructure, or bypassing existing security measures.”

Senior Product Portfolio Manager Cyber Defense, Swisscom
“Exeon offers numerous functional advantages over competing NDR products. With Exeon, we have the ability to leverage innovative technologies and advanced analytics to provide our customers with a best-in-class security solution. Together, we are committed to improving the security landscape.”

Regional Practice Head, Wipro
“Exeon is the ideal solution for transitioning from a legacy SOC to a Next-Generation SOC. It enhances detection capabilities, minimizes alert noise, and significantly reduces costs.”

CEO, Real Security
“As leading distributors, we’re always on the lookout for reliable, innovative, and powerful solutions to strengthen our portfolio and shape the future of cybersecurity. Exeon has proven time and again to be a trustworthy and easy-to-work-with partner. Their solution, exeon.ndr, has already made a big impact across various sectors.”
Further solutions

Hybrid & Multi-Cloud Enhancement
- Real-time monitoring of network flows across all platforms & environments.
- Automated threat hunting and incident response.
- Seamless integration with EDR, XDR, SOAR, and IPS systems.

Compliance
- Enhances compliance by providing full network visibility, anomaly detection, and the context needed for reporting and integration with SOAR playbooks.
- 100% network transparency and early detection of advanced threats.
- Ensures adherence to NIS2, ISO 27001, GDPR, and more.

Data Security
- Network traffic monitoring that keeps your data fully private.
- No data decryption and 100% compliance.
- No blind spots, no undetected data exfiltration.

Deployment
Secure your network quicker with a powerful AI-driven NDR in your existing infrastructure, without hardware dependencies and operational disruptions.
- Lower costs and hardware-free.
- Fewer false positives via AI-driven detection.
- Deep visibility across cloud & on-premises.
Industry-tailored, threat-focused

Use Case: Bank in Germany
DORA compliance, tackling threats like APTs & ransomware, improved threat detection, and faster response times.

Success Story: Logistics
Fast-moving, international logistics company defeats system interruptions from cyber incidents with Exeon.NDR.

Exeon.NDR for IT, OT & IoT
Advanced ML and network log analysis for full visibility and any existing cybersecurity infrastructure — without agents or data leaving your network.

Success Story: Banking
A cybersecurity case study on PostFinance, one of Switzerland’s leading retail financial institutions.

Use Case: Manufacturing & NIS2
OT/IIoT integration and compliance: how a mechanical engineering company increases their cybersecurity posture.

Success Story: Swiss Hospitals
Read how our platform became an integral security monitoring tool to safeguard Solothurner Spitäler’s IT & OT networks.
Frequently asked questions
How does Exeon monitor encrypted traffic without decryption?
What are the benefits of monitoring without decryption?
Monitoring without decryption ensures data privacy, reduces computational overhead, and maintains network performance while still providing full visibility into security threats across IT and OT environments.
Other benefits of security monitoring without decryption include simplifying compliance with data protection regulations like GDPR and HIPAA, as it avoids the need to access sensitive data directly. It also minimizes the risk of exposing sensitive information during monitoring, reduces the complexity of encryption management, and allows organizations to maintain a more efficient and lightweight security infrastructure, ensuring minimal impact on network resources and performance.