More Efficient and Scalable Network Analytics
Exeon outperforms with its hardware-free, scalable log analysis approach, holistic visibility, advanced machine learning, and cost-effective performance, even in encrypted environments.
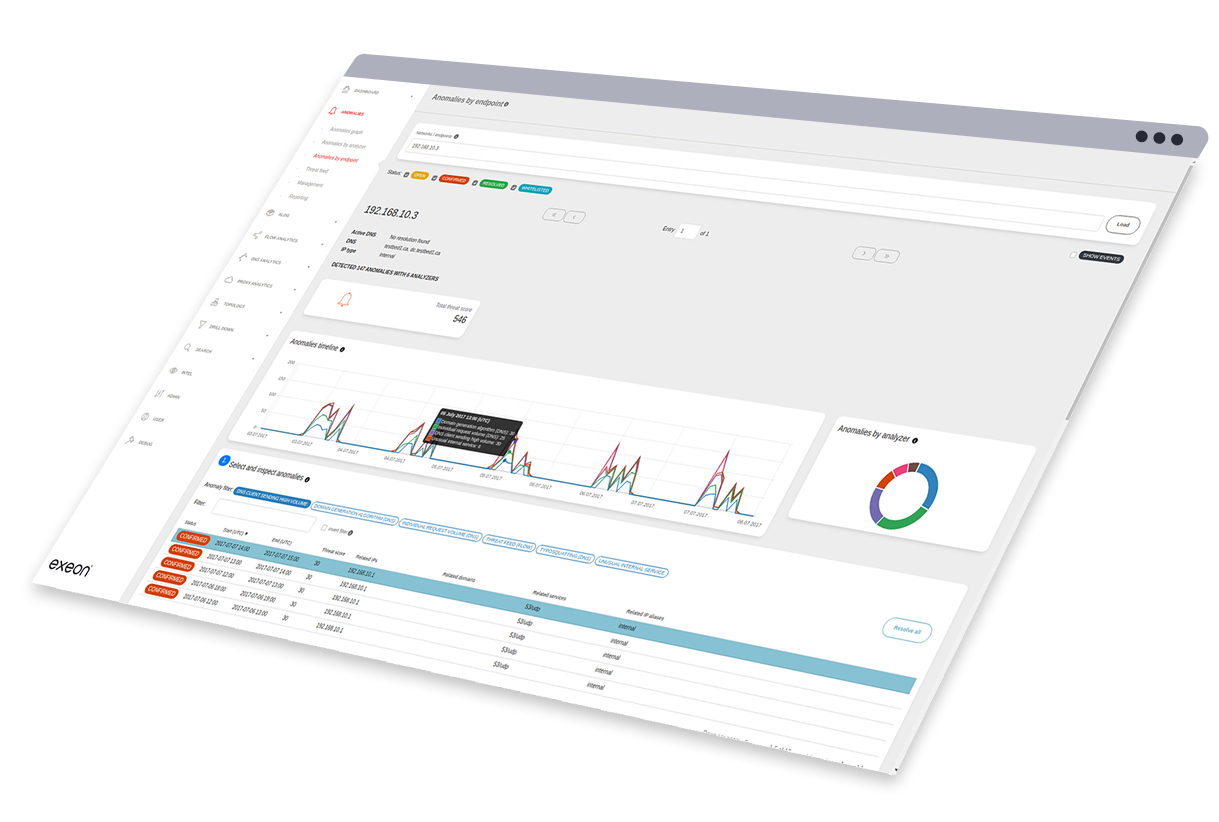
Exeon vs. Vectra
Vectra’s network analytics depend on hardware sensors and mirrored traffic, but encryption and core-switch limitations leave blind spots and force a shift to less effective metadata analysis.
Features
Machine learning
Deployment complexity
Data sources support
On-prem capabilities
Agent requirement
Scalability
Log enrichment
Asset discovery & mapping
SIEM optimization
Exeon
Transparent, white-box models can be tuned and enhanced by the user
Lightweight, using existing infrastructure; no sensors or agents needed, but possible
Broad support for log and flow data, including data lakes
Full on-prem capabilities, incl. detection, analysis & alerting, without any reliance on the cloud
Fully agentless
High scalability: our architecture allows on-prem, cloud & hybrid with full data ownership at any time
Supports enrichment via APIs and external data lakes
Asset discovery and mapping using correlated log and flow data
Preprocessing reduces log volume and lowers SIEM cost
Vectra
Proprietary AI and deep learning with limited explainability
Sometimes requires deployment of network sensors or cloud collectors
Focuses on network metadata, identity, & cloud telemetry; specific integrations often required
Forensic & investigation primarily through cloud-based services; limited on-prem, standalone functionality
No endpoint agents, but requires sensors for full visibility
Scales with packet-based processing; may require additional infrastructure
Enrichment via cloud and identity sources; less focused on log data
Entity attribution through host and account correlation
Sends alerts to SIEMs; may minimize ingestion volume
Why Exeon is the chosen platform
Exeon provides transparent, explainable AI with significantly lower false positives, ensuring actionable insights. Here’s how Swiss excellence changes the game.
Hardware-free efficiency
Exeon’s lightweight log data analysis eliminates the need for additional hardware. Say goodbye to traffic mirroring and network traffic sensors.
Holistic visibility despite encryption
Metadata-based approach for full network visibility across all assets, even in encrypted environments. No reliance on network probes, no blind spots.
Scalability & advanced features
Advanced ML, reduced log data, efficient storage, seamless integration, and immediate deployment make it a cost-effective, scalable solution.
Trusted by leaders
Exeon.NDR streamlines alerting and reporting to ease security teams’ workload and is used by organizations worldwide.

CISO, SWISS International Airlines
“As the Swiss national airline, we are driven by a passion for exceptional performance, in the spirit of our guiding principles. A stable and secure IT is the most important basis for an excellent customer service. For the security of SWISS IT, we use Exeon as a central cybersecurity tool, fully managed by our long-term partner Reist Telecom AG. A perfect combination and solution to monitor our network and quickly detect any kind of anomalies.”

Director of Cybersecurity Research, KuppingerCole
“The management and analyst interfaces are intuitive and can yield important insights for customers. Exeon’s approach to data retention helps customers keep data local for regulatory compliance and reduces costs for long-term storage by only retaining event metadata. The solution supports the most pertinent standards for exchanging threat information.”

ICT Project Leader, WinGD
“Exeon provides us with complete visibility of our network data flows and automatically detects suspicious behavior. Thanks to their AI algorithms, we immediately identify potential cyber threats and can respond quickly and efficiently. This way, we prevent attackers from moving undetected in our systems, infiltrating the infrastructure, or bypassing existing security measures.”
Empowering security teams worldwide
















Exeon.NDR in action
See how our AI-driven, encryption-agnostic technology closes visibility gaps left by other security tools—explore our use cases.

How AI benefits threat triage

Less false positives with AI

On-prem vs. cloud deployment

Guided threat detection tour

Your DORA Checklist

PostFinance Use Case

DORA, NIS2 & KRITIS Guide

DORA Use Case

Detect APTs: Finance Edition
Monitoring ATM Machines

NIS2 Compliance Checklist

NIS2, DORA & KRITIS Guide

DORA Compliance Checklist

DORA Banking Use Case

NIS2 Manufacturing Use Case

Use Case: Bank in Germany

Success Story: Logistics

Exeon.NDR for IT, OT & IoT

Success Story: Banking

Use Case: Manufacturing & NIS2

Success Story: Swiss Hospitals

Use Case: Healthcare & Compliance

Zero Trust in the finance sector

Meeting the unique needs of OT

From patient data to regulatory compliance

Financial sector applications

Made for the industrial world

Secure patient data & compliance

Public security, private data protected

AI against advanced threats

Global Manufacturer WinGD

Public Sector Use Case

Finance & Insurance

Manufacturing & Industrial

Public Sector
Experience the difference of Swiss security.
Now that we’ve outlined all the reasons why our NDR platform unique in the market, it’s time that you see it in action. Consult our security experts today.
