Years ago, more than hundreds of thousands of Microsoft Exchange servers have been hacked globally, whereas the DACH region seems to be highly affected. In fact, four zero-day vulnerabilities were discovered in on-premises Microsoft Exchange Servers.
This article explains how Exeon.NDR can help to detect the intrusion through automated and manual network analysis.
An overview on the Microsoft Exchange hack
Microsoft has been reporting a massive attack on its Exchange Server over the last few days. Attackers have successfully penetrated Microsoft Exchange Server versions 2013 through 2019 via four vulnerabilities. Though the extent of the attack is yet unknown, it is set to affect hundreds of thousands of organizations worldwide, making it one of the most significant attacks to date. Worse, according to Kaspersky’s IT security experts, Germany and Switzerland are among the countries most affected.
The hackers managed to penetrate the affected systems and install so-called web shells. Using these, they can access the Exchange servers and mails even after the security patches.
Dangerously, attackers can leverage the web shell to deploy additional malware tools in the company network, such as PowerShell scripts, Mimikatz or Cobalt Strike. This leaves victims exposed to attackers spreading throughout the network, compromising, stealing, and encrypting data for ransom (ransomware attack) as they advance.

The scale of the attack is on a completely unprecedented level. Reputable security media report that even if patched on the same day of the announcement, there is a high probability that the web shell has been installed on servers. Those who have not patched yet have a high likelihood of being affected by the attack.
Faced with this critical situation, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an emergency directive: all civilian and government-run Microsoft Exchange servers should be updated immediately or, if necessary, disconnected from the systems.
How Exeon helps to detect compromised servers
Although the attack is very advanced, Exeon’s AI security platform helps to detect the intrusion. The detection relies mainly on two functionalities of Exeon.NDR:
1. Automated network traffic analysis
Exeon features several models detecting irregular data flows and patterns occurring when attackers try to spread within a network (Internal Reconnaissance, Lateral Movement, and data exfiltration). We suggest treating Exeon.NDR’s alarms triggered for on-premise Microsoft Exchange Servers with the highest priority. Typical anomalies include:
- Vertical scanning (flow)
- Horizontal scanning (flow)
- New internal services and new incoming connections (flow)
- Outgoing connections to new port/server/service (flow)
- Bytes to external endpoint (flow)
- Command and control (proxy)
- DNS volume (proxy & DNS)
- Domain Generation Algorithm (proxy & DNS)
Depending on the applications that run on the Exchange servers some of those communication patterns might go unseen to automated detection. Therefore, we strongly recommend conducting a manual analysis through Exeon.NDR in addition to the automatic detection.
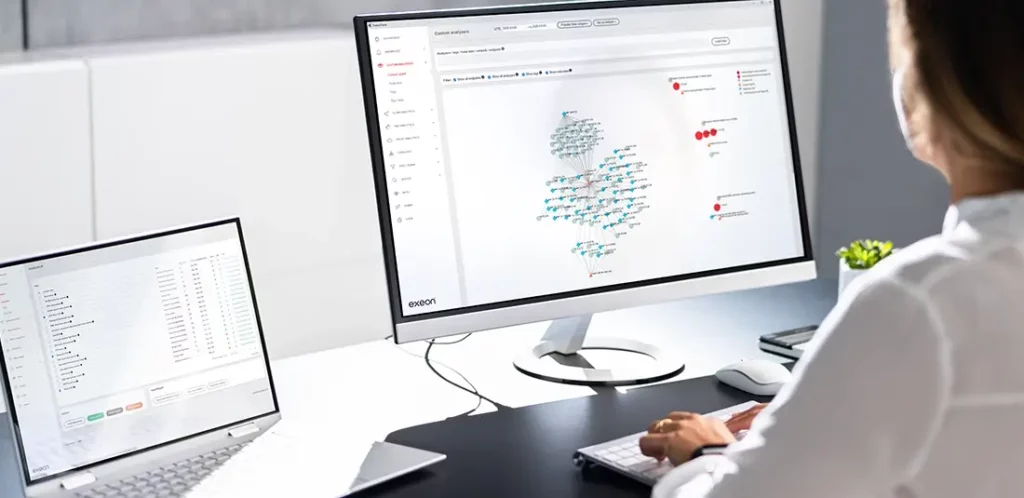
2. Investigation of Microsoft Exchange servers’ communication patterns
The “Client server pairs” flow visualization is particularly powerful for this investigation. There, an analyst can filter for the exchange servers by adding their IPs to the search bar at the top of the page. We recommend to check the three connection matrix visualizations (internal traffic/outbound traffic/inbound traffic) regarding the following aspects:
Client server pairs – Internal:
- Are there any signs of lateral movement? For example, the server is communciating with other internal devices newly via SSh (port 22/TCP), RCP (port 135/TCP), SMB (port 445/TCP), WinRm (port 5985/TCP and 5986/TCP).
- Is there any elevated Kerberos (port 88) or LDAP activity?
Client server pairs – Outbound:
- Does the server establish connections as a client that cannot be explained?
Client server pairs – Inbound:
- Are there connections with large amounts of outbound data?
- Are there connections from clients from unexpected geographic regions?
- Are there connections via remote control / administration tools? For example, Remote Desktop Protocol (RDP) on port 3389.
Confidence through comprehensive visibility
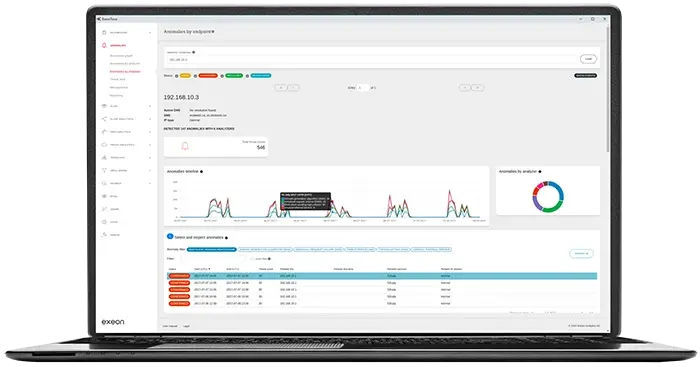
To summarize, unless there were already applications on the Exchange server that created similar data flows before the attack, Exeon’s Network Detection & Response platform automatically detects the anomalies with a high likelihood.
The additional manual analysis of the Exchange server through Exeon.NDR’s traffic visualization provides you with the additional confidence. For more details, watch the demo videos below.


