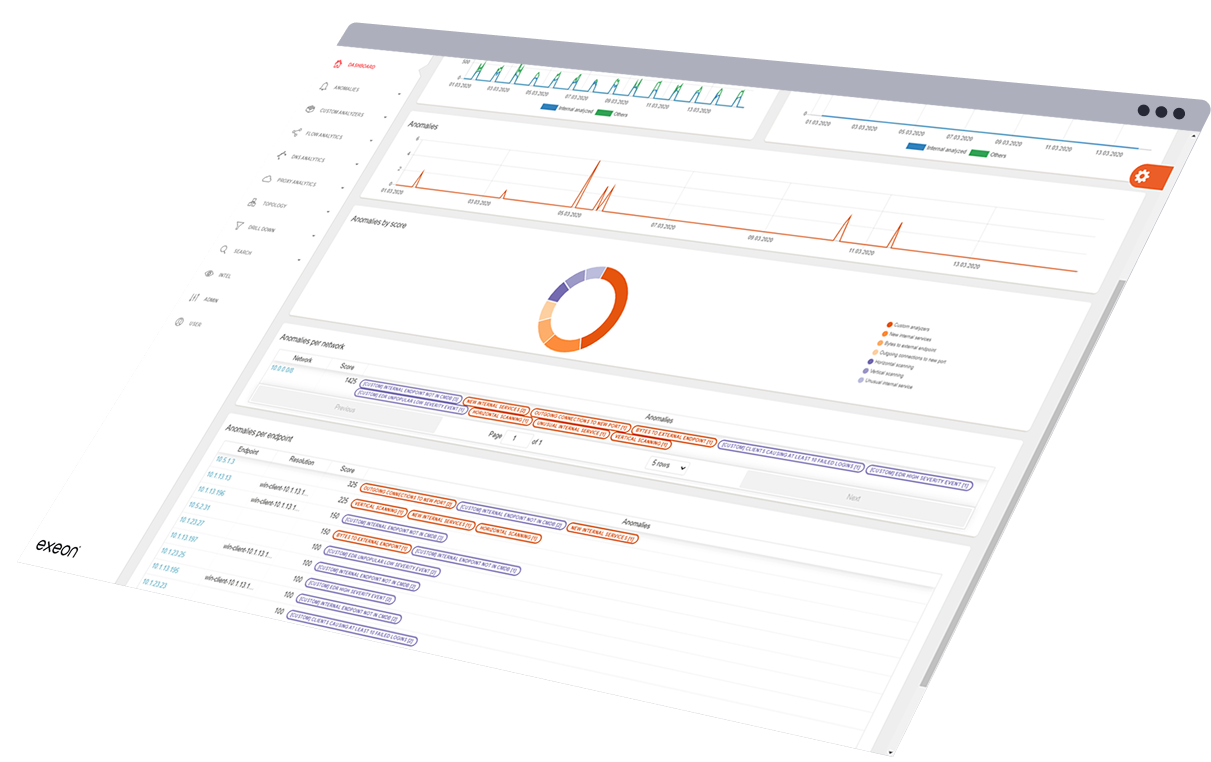
Cutting Through the Noise in Network Analytics
Exeon vs. ExtraHop
Features
Machine learning
Exeon
ExtraHop
Why Exeon is the chosen platform
Exeon provides transparent, explainable AI with significantly lower false positives, ensuring actionable insights. Here’s how Swiss excellence changes the game.
Extremely lightweight log analysis
While ExtraHop relies on dedicated sensors for traffic mirroring, we require no additional hardware for more scalability and cost efficiency.
It’s all in the metadata analysis
Exeon.NDR remains unaffected by encryption, providing complete network visibility. No limitations in handling encrypted data.
Future-proof machine learning
Forget hardware constraints—our advanced ML enables detection of complex threats, including even the most sophisticated ones.
Leaders who trust Exeon

Head IT Security, PostFinance AG
“PostFinance has chosen Exeon.NDR because of its open and future-proof architecture. Not needing any hardware sensors and being able to control data flows, we didn’t have to make any significant changes to our existing infrastructure. We are also convinced by the cooperation with the competent and technically outstanding Exeon team.”

CEO & Founder, Planzer
“As CEO and owner of a fast moving, international logistics company, I cannot afford any system interruptions due to cyber incidents. With Exeon.NDR, we have found a Swiss solution to monitor our network and quickly detect cyber threats.”

Director of Cybersecurity Research, KuppingerCole
“The management and analyst interfaces are intuitive and can yield important insights for customers. Exeon’s approach to data retention helps customers keep data local for regulatory compliance and reduces costs for long-term storage by only retaining event metadata. The solution supports the most pertinent standards for exchanging threat information.”
Empowering security teams worldwide
















Exeon.NDR in action
See how our AI-driven, encryption-agnostic technology closes visibility gaps left by other security tools—explore our use cases.

How AI benefits threat triage

Less false positives with AI

On-prem vs. cloud deployment

Guided threat detection tour

Your DORA Checklist

PostFinance Use Case

DORA, NIS2 & KRITIS Guide

DORA Use Case

Detect APTs: Finance Edition
Monitoring ATM Machines

NIS2 Compliance Checklist

NIS2, DORA & KRITIS Guide

DORA Compliance Checklist

DORA Banking Use Case

NIS2 Manufacturing Use Case

Use Case: Bank in Germany

Success Story: Logistics

Exeon.NDR for IT, OT & IoT

Success Story: Banking

Use Case: Manufacturing & NIS2

Success Story: Swiss Hospitals

Use Case: Healthcare & Compliance

Zero Trust in the finance sector

Meeting the unique needs of OT

From patient data to regulatory compliance

Financial sector applications

Made for the industrial world

Secure patient data & compliance

Public security, private data protected

AI against advanced threats

Global Manufacturer WinGD

Public Sector Use Case

Finance & Insurance

Manufacturing & Industrial

