Swiss-Engineered AI to Strengthen Resilience
After over a decade of institutional research, we have engineered sophisticated AI to empower security teams with unmatched precision, speed and efficiency in their daily operations.
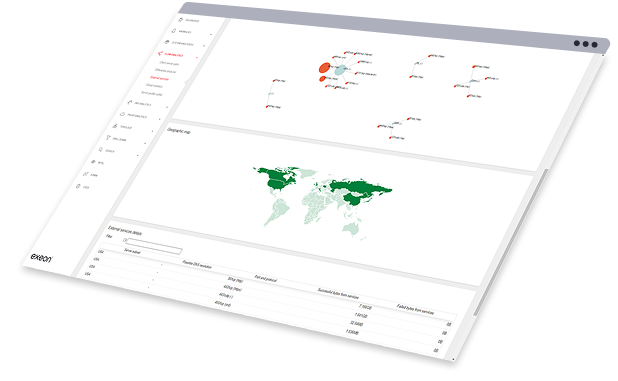
How AI empowers security teams
Return on Investment through efficient threat detection and reduced response times with AI (Forrester®)
Faster incident response through AI automation (Gartner®)
Reduction in false alarms with precise, machine learning-based detection (Gartner®)
Security teams must focus on real threats. That’s why AI and machine learning are the keys to becoming faster and more precise.
Monitor with surgical precision
Exeon's AI-driven metadata analysis and a clever whitelisting, filters safe traffic, eliminates false positives, and surfaces true anomalies across IT and OT.
Detect threats in billions of activities
Machine learning behavioral models analyze network traffic to identify known attack patterns and previously unseen anomalies for early, effective threat detection.
Automate rapidresponse
Risk-scored alerts flow into your SOAR platform via open APIs, where playbooks isolate hosts and block malicious traffic in seconds.
Supervised machine learning
Supervised models are pretrained on real-world attack patterns in controlled environments, enabling accurate, out-of-the-box detection for known threats from day one.
Unsupervised algorithms
Unsupervised algorithms learn typical behavior onsite, identifying anomalies unique to each environment in real-time without prior labeling or rules.
Expert use case integration
Expert use case integration correlates traditional indicators with network data, enriching detection algorithms with additional context for superior accuracy.
Risk-based alerting
Risk-based alerting and dynamic scoring mechanisms evaluate the severity and context of each incident, enabling security teams to triage effectively and focus response efforts on the most impactful threats.
No deep packet inspection (DPI)
Exeon analyzes metadata, not payloads — ensuring encrypted traffic remains private while maintaining full visibility into behavioral anomalies.

Trusted by global organizations


















How security teams benefit from Exeon.NDR
See every network flow
Exeon passively collects metadata from IT, cloud, IoT and OT devices to deliver a unified view of all traffic. This holistic visibility uncovers lateral movement, C2 beacons and encrypted threats across every segment, eliminating blind spots.
Detect and respond faster
Our AI detects unusual activity such as zero-day attacks, insider threats, and emerging attack patterns as they happen. By scoring risks and working seamlessly with SOAR tools, it helps teams focus on most pressing threats to respond faster.
Deploy agentless at scale
A virtual appliance that includes lightweight data collection — no endpoint agents or extra hardware required. One policy set instantly covers legacy, unmanaged and cloud environments, scaling effortlessly as your infrastructure grows.
Automate compliance and cut risk
Ready-to-use documentation and audit logs for evidence and compliance-relevant data. Our event correlation and risk-based alerting eliminates the vast majority of annoying false positives and saves analysts dozens of hours of time every week.
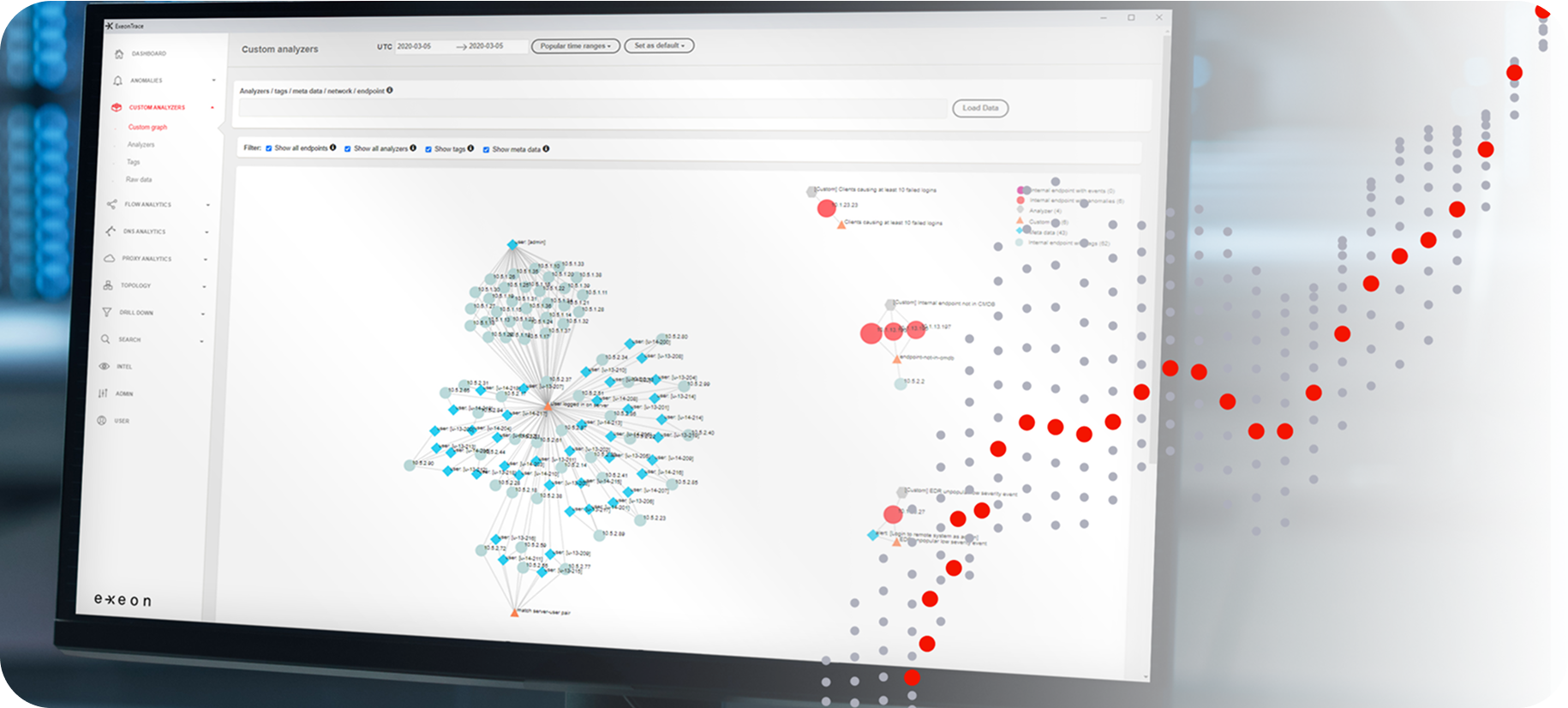
Al-based attack and anomaly detection through NDR
Market comparison
Exeon eliminates DPI’s challenges with its innovative metadata analysis approach, delivering real-time insights across physical, virtual, and cloud environments without invasive methods.
Capabilities
Lightweight, efficient data analysis without traffic mirroring or sensors
Security analytics unaffected by encryption
Superior network visibility, not restricted to core switch traffic only
Powerful Machine Learning algorithms
Fully on-prem data processing
Exeon
Vectra
Darktrace
ExtraHop
Security installations

IT / OT / IoT
It enables real-time threat detection, automated response, and threat hunting, reduces false positives, and empowers security teams to protect critical infrastructure with greater efficiency and precision.
- Real-time threat & anomaly detection
- Automated incident response and faster mitigation
- Supporting proactive threat hunting

SOC+
AI strengthens SOCs by automating threat detection, accelerating response times, and enhancing decision-making accuracy.
- Faster identification of threats
- Reduced workload by incident prioritization
- Increased accuracy when identifying complex attack patterns
Data Security
AI enhances data security by automating threat detection, improving data protection, and enabling faster responses to breaches.
- Real-time detection of data breaches
- Automated responses to mitigate threats quickly
- Enhanced protection against complex threats

Insider Threat Management
A multi-layered approach to detect and mitigate insider threats by leveraging AI-powered Network Detection and User and Entity Behavior Analytics.
- Comprehensive monitoring for full network and application visibility
- Zero Trust integration to enforce strict access controls
- Real-time security insights via live dashboards
AI & Security Use Cases
Our technology is engineered to adapt to business specifications and individual requirements without compromising security, efficiency, and compliance.

Public Sector Use Case

AI against advanced threats

Guided threat detection tour

On-prem vs. cloud deployment

Less false positives with AI

How AI benefits threat triage
What customers say about our AI technology
Security teams of global organizations report on their experience with our AI and machine learning.

CISO, SWISS International Airlines
“As the Swiss national airline, we are driven by a passion for exceptional performance, in the spirit of our guiding principles. A stable and secure IT is the most important basis for an excellent customer service. For the security of SWISS IT, we use Exeon as a central cybersecurity tool, fully managed by our long-term partner Reist Telecom AG. A perfect combination and solution to monitor our network and quickly detect any kind of anomalies.”

CEO & Founder, Planzer
“As CEO and owner of a fast moving, international logistics company, I cannot afford any system interruptions due to cyber incidents. With Exeon.NDR, we have found a Swiss solution to monitor our network and quickly detect cyber threats.”

Head Infrastructure & Applications, 3 Banken IT
“We especially appreciate the comprehensive network visibility that Exeon.NDR offers us.
The anomaly detection is also extremely accurate and allows our analysts to focus on the essential threats.”

ICT Project Leader, WinGD
“Exeon provides us with complete visibility of our network data flows and automatically detects suspicious behavior. Thanks to their AI algorithms, we immediately identify potential cyber threats and can respond quickly and efficiently. This way, we prevent attackers from moving undetected in our systems, infiltrating the infrastructure, or bypassing existing security measures.”

Senior Product Portfolio Manager Cyber Defense, Swisscom
“Exeon offers numerous functional advantages over competing NDR products. With Exeon, we have the ability to leverage innovative technologies and advanced analytics to provide our customers with a best-in-class security solution. Together, we are committed to improving the security landscape.”

CEO, Real Security
“As leading distributors, we’re always on the lookout for reliable, innovative, and powerful solutions to strengthen our portfolio and shape the future of cybersecurity. Exeon has proven time and again to be a trustworthy and easy-to-work-with partner. Their solution, exeon.ndr, has already made a big impact across various sectors.”

CEO, EnBW Cyber Security
“We are looking for European, data protection-compliant solutions that are quickly implementable and AI-based. Exeon, as a Swiss company, is ideal for us because the tool is easy for our analysts to use and continuously learns. These advantages led to our decision regarding Exeon.”

CEO, Ensec
“For us as a managed security service provider, a reliable, fast and highly automated NDR solution like Exeon.NDR is the key to long-term and satisfied customer relationships. We are therefore delighted to partner with the Exeon team.”

CEO, RAS Infotech Limited
“After a comprehensive evaluation of various NDR technologies, we observed that most vendors rely heavily on collecting data from SPAN ports, which felt like searching for a needle in a haystack. However, Exeon.NDR stood out with its future-proof strategy that leverages metadata analysis, eliminating the need for traffic mirroring. This approach not only simplifies the process but also allows us to gather information from various branch switches, providing a 360-degree view of security threats across our network. Consequently, we decided to move forward with Exeon.NDR.”

Head IT Security, PostFinance AG
“PostFinance has chosen Exeon.NDR because of its open and future-proof architecture. Not needing any hardware sensors and being able to control data flows, we didn’t have to make any significant changes to our existing infrastructure. We are also convinced by the cooperation with the competent and technically outstanding Exeon team.”
Industry-focused, results-driven

Use Case: Bank in Germany
DORA compliance, tackling threats like APTs & ransomware, improved threat detection, and faster response times.

Success Story: Logistics
Fast-moving, international logistics company defeats system interruptions from cyber incidents with Exeon.NDR.

Exeon.NDR for IT, OT & IoT
Advanced ML and network log analysis for full visibility and any existing cybersecurity infrastructure — without agents or data leaving your network.

Success Story: Banking
A cybersecurity case study on PostFinance, one of Switzerland’s leading retail financial institutions.

Use Case: Manufacturing & NIS2
OT/IIoT integration and compliance: how a mechanical engineering company increases their cybersecurity posture.

Success Story: Swiss Hospitals
Read how our platform became an integral security monitoring tool to safeguard Solothurner Spitäler’s IT & OT networks.

Use Case: Healthcare & Compliance
Centralized visibility and monitoring of hybrid environments to safeguard critical medical systems.

Global Manufacturer WinGD
In this video testimonial, our customer WinGD explains how Exeon.NDR strengthens their cybersecurity.
Frequently asked questions
Further details on our platform’s powerful machine learning algorithms designed to detect sophisticated cyber threats by analyzing your log data.
How is supervised machine learning used in Exeon.NDR?
Supervised machine learning in Exeon.NDR is trained on labeled datasets, meaning it’s trained from past attacks and predefined threat patterns. This approach is particularly effective for detecting known threats, such as lateral movement or brute-force attacks. As for unsupervised ML, by matching current network activity with historical attack data, it quickly identifies suspicious behavior that fits previously seen attack signatures. For example, Exeon.NDR can detect command-and-control traffic based on patterns found in past attack logs, enabling security teams to respond swiftly.
How is unsupervised machine learning used in Exeon.NDR?
Unsupervised machine learning, on the other hand, does not rely on predefined patterns but instead identifies unknown or evolving attack patterns. It analyzes network behavior and flags anomalies that do not conform to normal activity. This makes it particularly useful for detecting new and sophisticated threats, such as zero-day attacks or advanced persistent threats (APTs). In Exeon.NDR, this capability helps uncover subtle attacker movements within a network, such as lateral movement, where an intruder spreads from one system to another while avoiding traditional detection methods.
Why do we use both supervised and unsupervised?
By combining supervised and unsupervised machine learning, we ensures a comprehensive security approach. Supervised learning allows for quick detection of known attack methods, providing immediate protection against familiar threats. At the same time, unsupervised learning enhances security by identifying novel or stealthy attacks that would otherwise go unnoticed. This dual approach maximizes detection accuracy while maintaining adaptability to evolving cyber threats.
What is the future of AI-powered cybersecurity?
The future lies in privacy-conscious security solutions that prioritize detecting threats through intelligent pattern analysis rather than invasive surveillance—ensuring strong protection without overstepping privacy boundaries.
How does behavior-based security enhance protection?
By focusing on network behavior rather than individual data packets, AI-driven security solutions can detect zero-day attacks and unknown threats based on deviations from normal patterns—offering stronger, privacy-friendly protection.
Talk to an expert
Have questions about AI-driven security that is future-proof and scales infinitely? Our experts are available to assist with strategic planning, network security, integrations, and more.
