Complement EDR/XDR with NDR’s AI-Powered Precision
Exeon.NDR brings EDR/XDR to the next level with AI-driven APT detection and deeper network visibility, enabling faster threat response.
Problems EDR/XDR alone can’t solve
EDR/XDR can’t cover attackers that bypass endpoint protection agents. NDR delivers network-layer visibility to uncover blind spots and enable faster threat detection.
Zero-day exploits
Zero-day exploits move laterally in hours; endpoint-only tools rarely spot the first beacon.
Slow responses
Reactive security detects attacks too late. By the time a signature fires, attackers may have dwelled for days.
Blind spots
Security teams face too many false alerts while missing hidden threats. Intelligent detection is crucial for fast and effective responses.
How security teams benefit from integrating NDR
Advanced threat correlation & contextualization
Exeon fuses network anomalies with endpoint, identity and cloud signals, revealing beaconing, C2, or data exfiltration activity invisible to EDR alone.
- Higher-confidence alerts through multi-source correlation.
- Full kill-chain view across endpoint and network paths.
- Automated enrichment to speed analyst triage.
Automated response & mitigation
Real-time playbooks to quarantine infected hosts or block malicious flows via SIEM / SOAR integration.
- Network-level isolation stops lateral movement fast.
- Risk-based triggers reduce alert noise by 80%.
- Detailed incident data feeds post-mortem forensics.
Real-time detection EDR/XDR can’t do
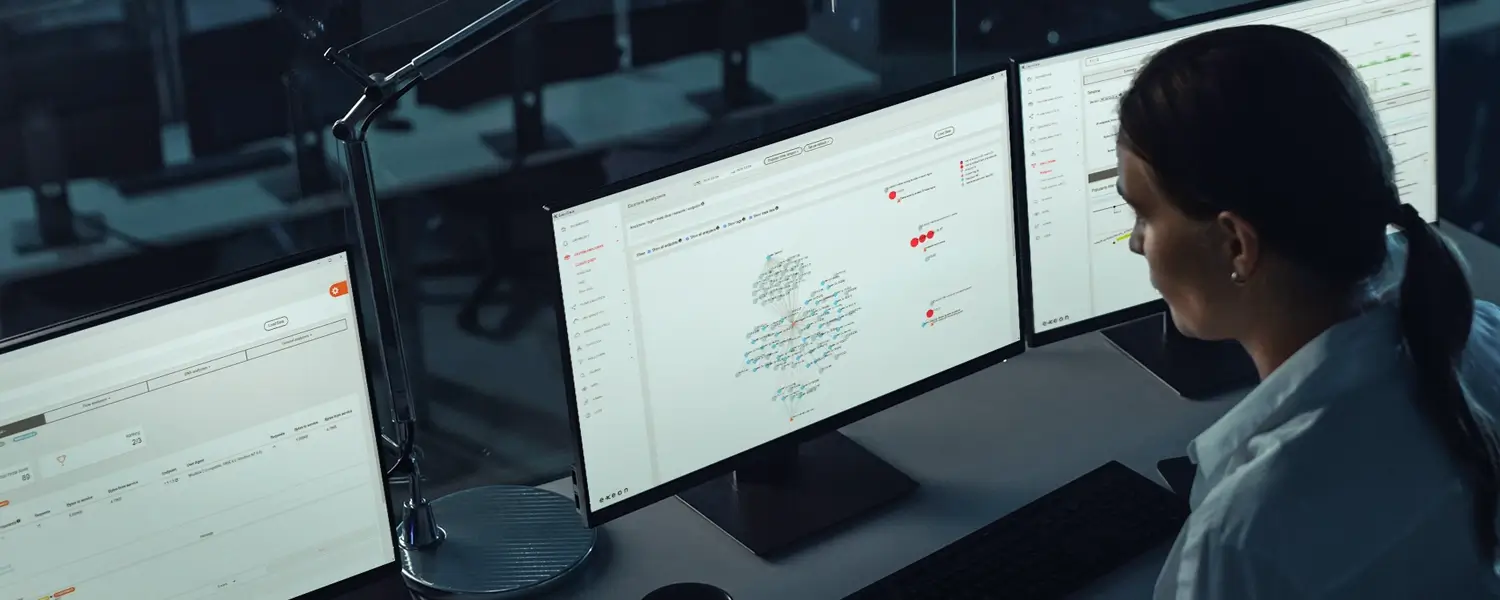
While EDR and XDR focus on endpoints and logs, they often miss threats moving laterally across the network. Network Detection and Response (NDR) closes this gap by analyzing metadata to detect suspicious behavior in real time — even in encrypted environments.
- Gain visibility into east-west traffic and threats that bypass endpoints.
- Reveal stealthy behaviors like beaconing and dormant connections.
- Surface encrypted and unknown threats using AI-driven network behavior analysis.
Network visibility for hybrid threats
While EDR/XDR secures endpoints and cloud workloads, it often misses unmanaged devices, encrypted threats, and lateral activity in hybrid infrastructures. NDR complements this by delivering network-level visibility across on-prem, cloud, and IoT environments.
- Detects rogue assets, unmanaged endpoints, and unauthorized applications for full shadow IT & device discovery.
- Covers and monitors traffic across on-prem, multi-cloud, and legacy environments for misconfigurations and cross-zone threats.
- Identifies unusual communication flows that may indicate misconfigurations, exposed services, or unauthorized access paths.
How security teams benefit from Exeon.NDR
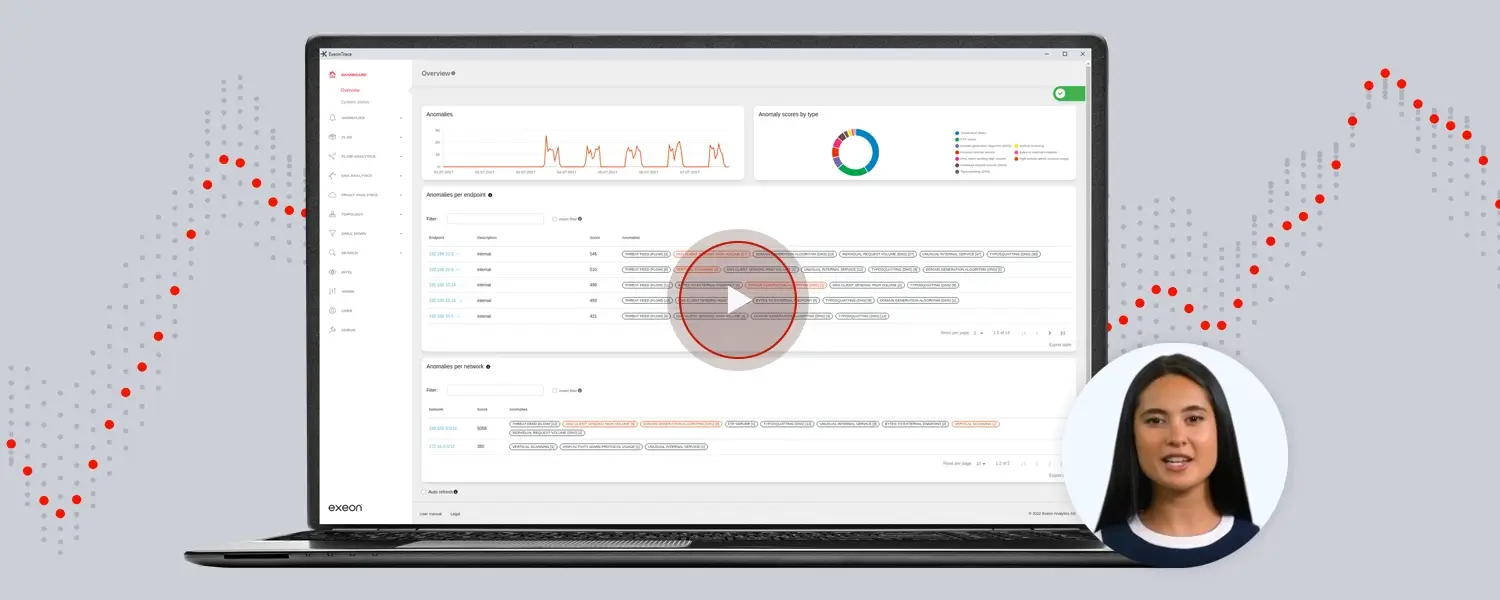
Full network visibility
Faster threat detection & response
Agentless & scalable deployment
Ensure regulatory compliance (GDPR, DORA, NIS2) with comprehensive network monitoring, audit logs, and threat forensics. Reduce breach impact by detecting and stopping attacks before data is exfiltrated.
Al-based attack and anomaly detection through NDR
Trusted by global organizations

















Related solutions for you
Scalability
Agentless, scalable security that covers unmanaged devices, IoT, and cloud assets—seamlessly integrating with your existing EDR/XDR for effortless expansion.
Deployment
Insights from our security experts
Cut through the cyber noise: blogs written by our thought leaders in AI-powered cybersecurity.
Your APT detection guide
A 24-page guide on AI-enhanced detection, the current threat landscape, and how organizations can improve their threat detection and response capabilities.

Ready to enhance your EDR/XDR with NDR?
Security teams significantly reduced dwell time and uncovered hidden threats thanks to Exeon.NDR.
Speak with us about detecting and stopping sophisticated attacks before they can spread.