Definition
Malware belongs to the category of harmful programs designed to perform unwanted and destructive activities on computers, mobile devices, networks, or other electronic devices. These programs are secretly installed or executed without the user’s knowledge or consent. Cybercriminals develop and deploy them to achieve malicious goals, ranging from financial gain and data theft for espionage to operating system corruption and attacks on hostile states.
How it works
Malware can compromise systems in different ways. Although its types vary, it generally follows certain steps to achieve malicious goals:
- Infection: Infections enter the system through security holes or vulnerabilities. This can occur by opening infected email attachments, visiting compromised websites, downloading infected files, or exploiting vulnerabilities in software or operating systems.
- Installation: These malicious programs install themselves or hide inside legitimate files to make them harder to detect. They may also use rootkit techniques to conceal themselves at deeper levels of the operating system, making detection difficult.
- Carrying out malicious activities: Depending on its type, it can perform various malicious functions. A few examples are:
- Deleting or encrypting files
- Recording keystrokes
- Stealing confidential information
- Sending spam emails
- Executing denial-of-service attacks, or
- Opening backdoors for remote access
- Spread: Worms and other types of malware can automatically spread to other systems by using network connections or sending infected files to other users. Thus, the software can spread to various devices and cause significant damage.
- Camouflage and disguise: These threats can use various methods to evade detection. They can change file names, infiltrate legitimate system processes, hide from security software, or employ anti-analysis techniques to make them difficult to function.
Attackers can remotely control certain types of threats. They can receive and execute commands, download updates to improve their functionality, or update themselves to bypass security measures.
The most dangerous malware types at a glance
Trojans, ransomware, and more—are you aware of the various types of cyber threats currently lurking in corporate networks and attempting to infiltrate your systems? The range of these harmful programs is constantly expanding. Among the numerous categories that exist today, the ones listed below are the most prevalent.

Ransomware, one of the malware types, is the biggest cyber risk concern of CISOs in 2025 according to WEF.
- Viruses: Viruses are one of the oldest and most well-known types of malware. They corrupt programs or files and spread by attaching themselves to other executable files. Viruses can delete files, corrupt data, interfere with system functions, or perform unwanted activities to cause damage.
- Worms: Worms are self-replicating threats that spread automatically across networks without a user actively executing an infected file. They move from one system to another by exploiting security holes and vulnerabilities. Worms can cause significant damage by consuming bandwidth, overloading system resources, or stealing sensitive data.
- Trojan horse: A Trojan horse is a type of malicious software that disguises itself as legitimate software and can infiltrate a system. It may appear as a useful application, computer game, or any other program that seems harmless. Once activated, the Trojan grants attackers access to the infected system, allowing them to steal personal data, gain access later, or perform other malicious activities.
- Ransomware: Ransomware is a particularly dangerous type of cyber threat that encrypts files or a user’s entire system and then demands a ransom to release the data. It can have a negative impact on businesses and individuals, causing significant financial damage and business disruption.
- Spyware: Spyware is a type of harmful software that secretly installs itself on a system and monitors user activities. Keystrokes, passwords, browsing activity, and other personal data are tracked and collected. This information is then sent to attackers, who can use it to commit identity theft, fraud, or other illegal activities.
- Adware: Adware is a type of malware that displays advertisements on an infected system. It is often installed alongside other free programs or software bundles. While adware isn’t as harmful as some other malicious software, it can harass users, slow down system performance, or collect personal data to display targeted advertisements.
- Keylogger: Keyloggers are malicious programs that secretly capture keystrokes. They can steal passwords, credit card details, and other sensitive information. Subsequently, this data can be used for fraud or identity theft.
- Rootkits: Rootkits are a particularly dangerous type of malicious software. This software allows attackers to gain unrestricted system access rights and hide their presence. They can be used to conceal other threats, bypass security precautions, or completely lose control of the system.
Signs of malware infection
Here are 10 ways to recognize such cyber attacks:
- Unexplained system slowdown: If your computer suddenly slows down and even simple tasks take a lot of time, this could indicate the presence of malicious software.
- Frequent crashes or system freezes: If your system crashes or freezes more often for no apparent reason, this could indicate a security threat.
- Pop-up ads and unwanted ads: Aggressive pop-ups, unwanted ads or links to dubious websites can indicate adware infections.
- Altered browser settings: A browser hijacking malware could be behind it if your default homepage, search engine, or other browser settings have been inexplicably changed and you haven’t done it yourself.
- New programs or toolbars that appear suddenly: If you suddenly see new programs, toolbars, or extensions that you didn’t install yourself, it’s possible that your system is infected with unwanted software.
- Missing or corrupted files: If files are suddenly missing or inaccessible, it may indicate ransomware or other malicious programs.
- Unusual data consumption or network activity: If your data consumption or network traffic has increased significantly, this could indicate the presence of malicious software.
- Password problems: If your passwords stop working or your online accounts have been compromised, it could indicate a keylogger or spyware infection.
- Security software malfunctions: If your firewall or antivirus software suddenly stops working or is disabled, it could be a sign that a security threat is trying to evade detection.
- Unknown processes or suspicious activity in task manager: Monitor Task Manager for any unknown or suspicious processes running in the background. This could indicate a cybersecurity threat.
It’s important to note that these signs don’t always clearly point to a security issue, as there could be other causes as well. However, if you notice several of these clues at once, you should examine your system for potential vulnerabilities and take the appropriate measures to address them.
Malware protection strategies
How to avoid the malicious software: protecting your data, systems, and privacy from cyber threats is critical. Here are some important safety precautions you can take:
- Use reliable security software: Install high-quality antivirus and anti-malware software on all devices. Make sure the software is updated regularly to counter new threats.
- Keep your software up to date: Regularly update your operating system, applications, and security software. Patches and updates close security vulnerabilities that could be exploited by malicious software, protecting your system from cyber threats.
- Be careful when opening emails and attachments: Be suspicious of emails from unknown senders or suspicious content. Do not open attachments or click on links in such emails unless you are absolutely sure of their safety.
- Avoid visiting unsafe websites: Avoid accessing questionable websites or downloading files from untrusted sources. Look for the security icon, such as a lock as a symbol) in the browser’s address bar to ensure that the connection is encrypted.
- Enable the firewall: Make sure your firewall is enabled to block unwanted traffic and make it harder for malware to get in.
- Use strong and unique passwords: Use strong, unique passwords for your accounts that consist of a combination of letters, numbers, and special characters. Use a separate password for each account to minimize the risk of compromise.
- Enable two-factor authentication (2FA): Use the added security layer of two-factor authentication to ensure that even if your password is compromised, your account remains protected.
- Be careful with USB and external devices: Avoid connecting unknown or unsecured USB flash drives or external devices to your computer, as they could potentially contain malicious files or harmful software, posing significant security risks.
- Back up your data regularly: Make regular backups of your important files and store them in a safe place. In case of a security threat, you can easily restore your data without paying a ransom.
- Raise awareness and train your colleagues and employees: Conduct training and awareness activities for employees to educate them about the risks of malware. Encourage your employees to practice security-conscious behavior and report suspicious activity.
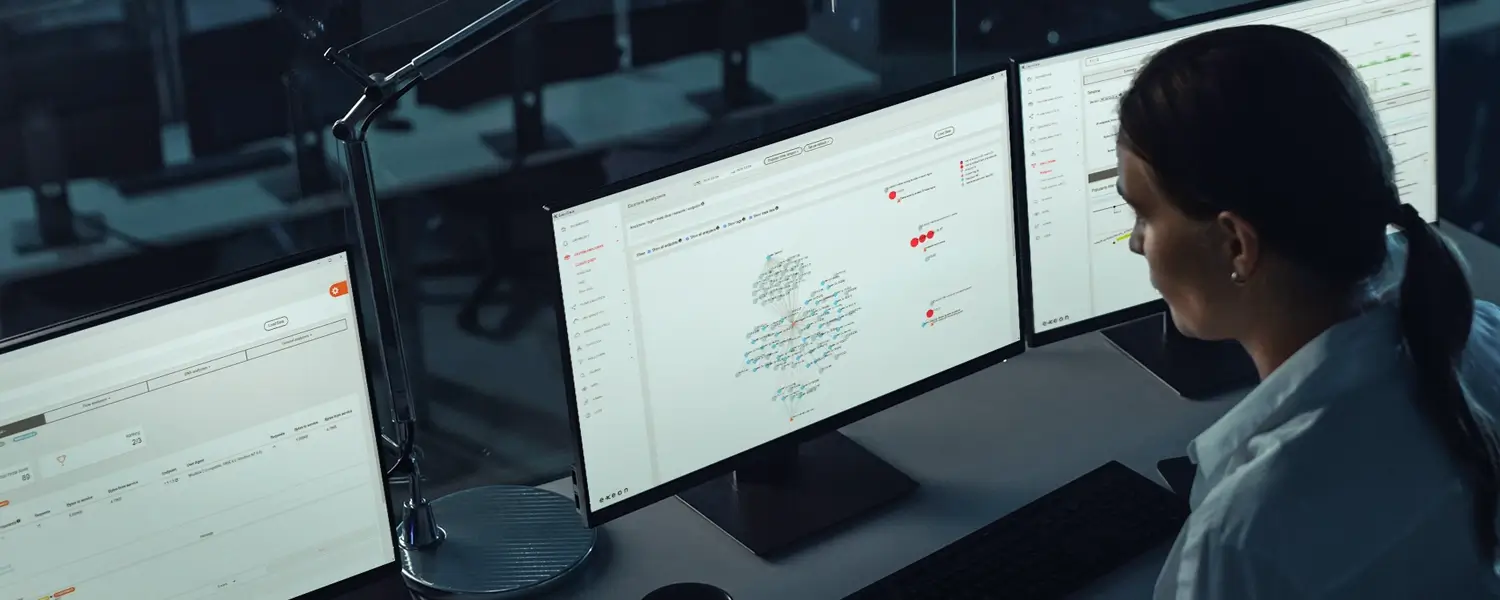
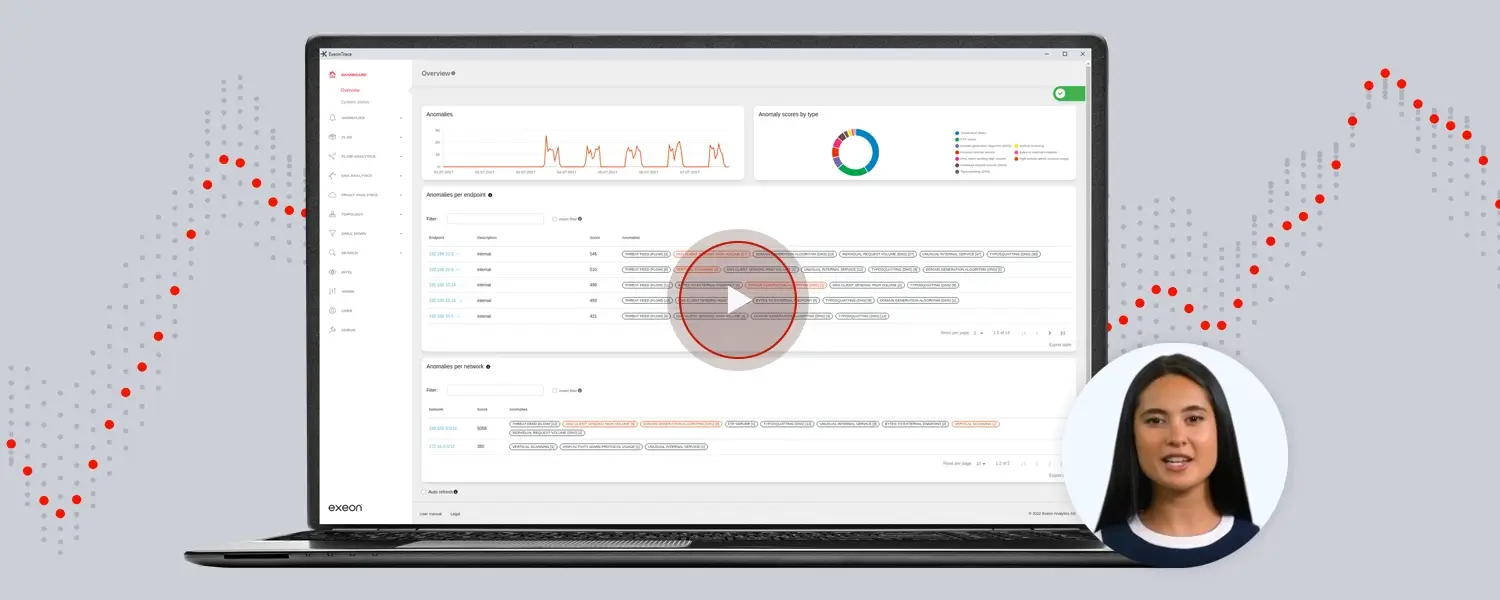
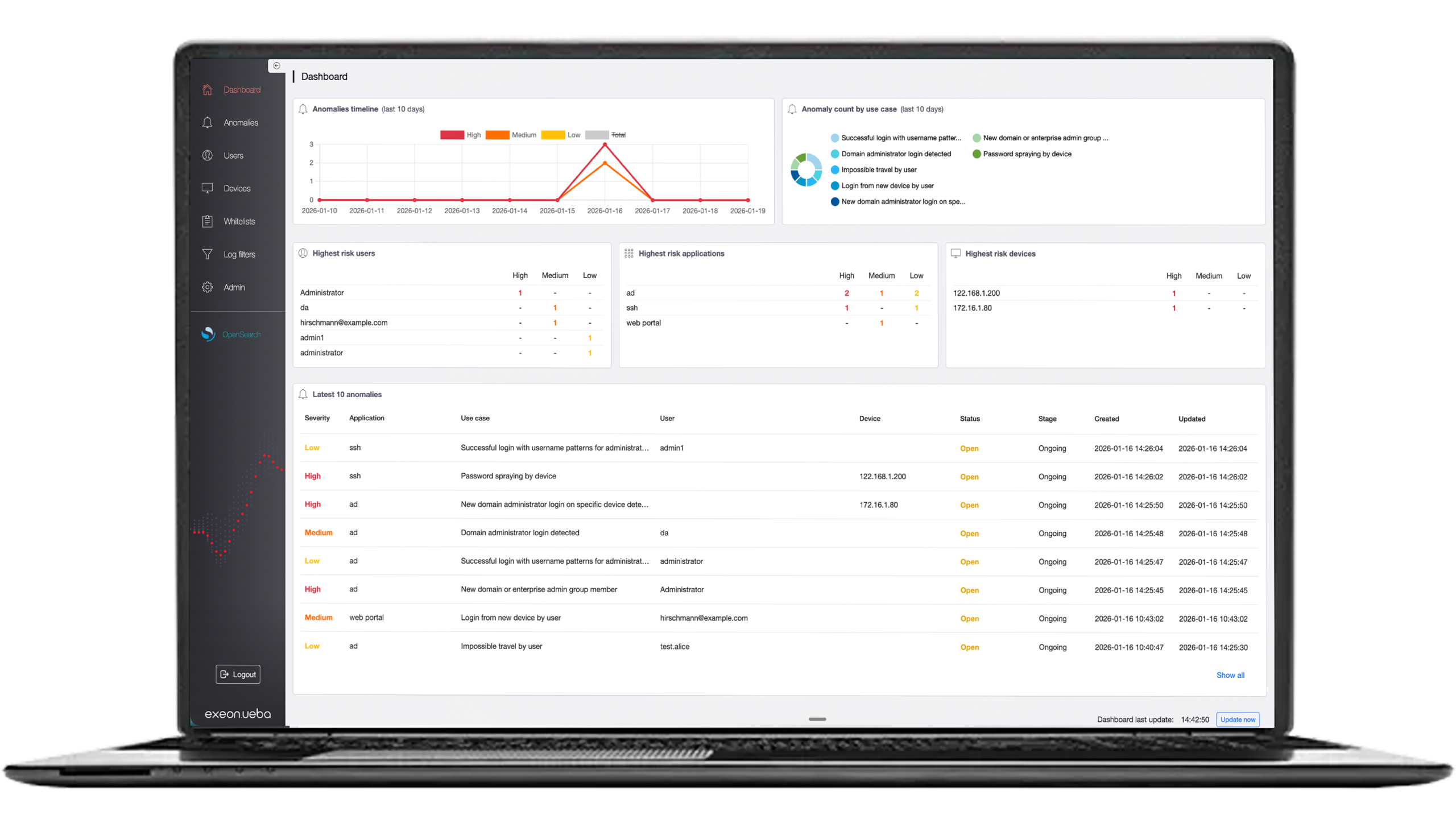
How NDR helps
An all-round strike against all threats in your network
Security solutions like Exeon.NDR are extremely effective protection from “simple” malware to Advanced Persistent Threats (APTs), i.e., very advanced, persistent threats.
When it comes to protecting your systems, it is crucial to deploy effective security solutions designed to prevent intrusions. Protective hardware and software targeted at endpoints include firewalls and security solutions that monitor these points to detect external attacks, such as those coming through PCs, file servers, smartphones, or Internet-of-Things (IoT) devices.
Most of the time, however, threats, especially more sophisticated ones, are already “in the system” and can only be stopped by analyzing network traffic with a so-called NDR (Network Detection and Response) to detect threats and intervene in time.
One such solution is Exeon.NDR, an advanced network monitoring and threat analysis platform. It offers a comprehensive set of features to help organizations protect themselves from malware threats.