Exeon, the Future of Network Detection and Response
Exeon’s cutting-edge NDR platform surpasses the limitations of IDS and IPS, redefining how networks are protected against Advanced Persistent Threats (APT) and supply chain attacks.
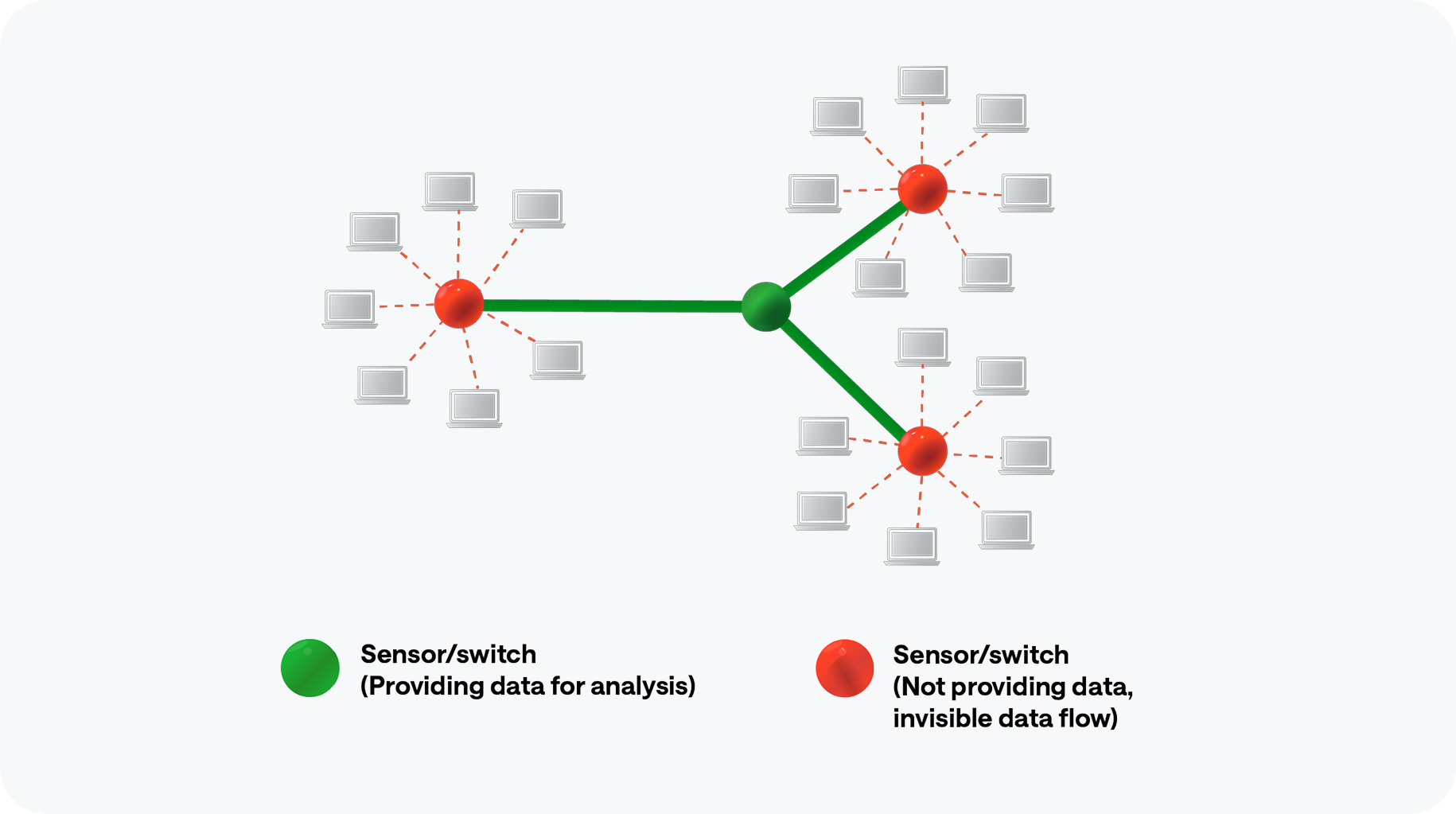
What they see
Deep Packet Inspection limitations
DPI needs mirrored traffic from core switches, limiting high-bandwidth use.
Encryption
challenges
Modern encryption (e.g. SSL/TLS) renders DPI, unable to inspect encrypted payloads.
Hardware dependencies
DPI often requires dedicated sensors, increasing costs and deployment complexity.
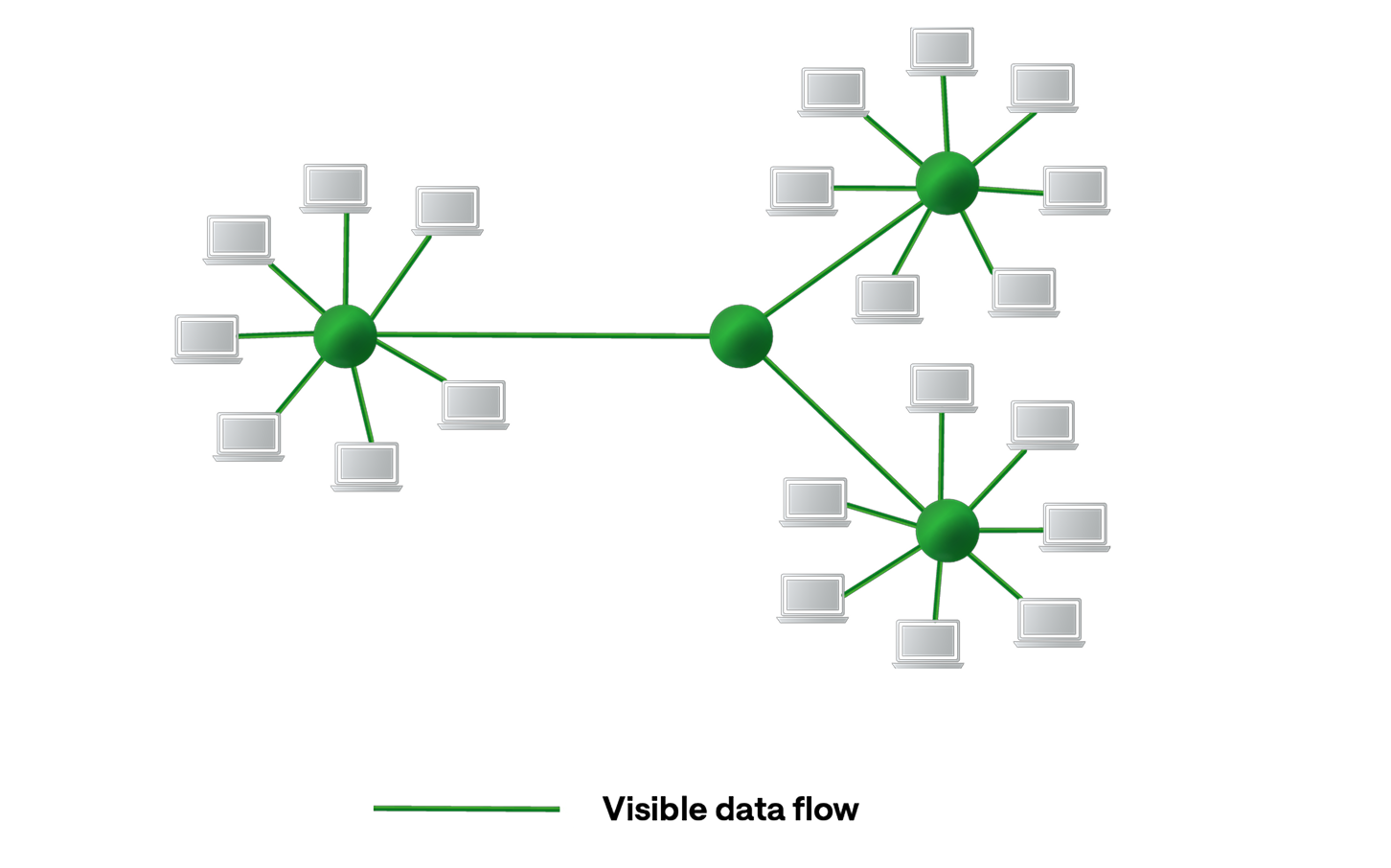
What we see
100% network visibility
Exeon analyzes lightweight metadata from diverse sources, including NetFlow, sFlow, firewalls, and cloud logs, for holistic visibility.
Encryption-agnostic
Metadata analysis focuses on IP addresses, protocols, and session lengths, making Exeon immune to encryption—best for high-bandwidth scenarios.
No hardware dependencies
Exeon is free of sensors or mirrored traffic for a cost-effective and scalable deployment.
Exeon compared to traditional NDR vendors
Exeon eliminates DPI’s challenges with its innovative metadata analysis approach, delivering real-time insights across physical, virtual, and cloud environments without invasive methods.
Capabilities
Lightweight, efficient data analysis without traffic mirroring or sensors
Security analytics unaffected by encryption
Superior network visibility, not restricted to core switch traffic only
Fully on-prem data processing
Transparent machine learning models
Exeon
Vectra
Darktrace
ExtraHop
What traditional solutions lack
As organizations face increasingly sophisticated threats, robust Network Detection and Response systems are critical— especially the following unique functionalities Exeon offers:
Vectra
Darktrace
ExtraHop
Exeon offers a lightweight, software-only solution, eliminating the need for hardware appliances and reducing operational complexity.
Our platform
Cutting-edge metadata analysis
Robust threat detection, unaffected by encryption.
Holistic
visibility
Across IT/OT and cloud infrastructures with Swiss precision.
Efficient data management
Lightweight log storage for long-term, reliable analysis.
Trusted by global organizations















What our customers say
Customers stay loyal to our future-proof, infinitely scalable, and cost-effective platform.

CISO, SWISS International Airlines
“As the Swiss national airline, we are driven by a passion for exceptional performance, in the spirit of our guiding principles. A stable and secure IT is the most important basis for an excellent customer service. For the security of SWISS IT, we use Exeon as a central cybersecurity tool, fully managed by our long-term partner Reist Telecom AG. A perfect combination and solution to monitor our network and quickly detect any kind of anomalies.”

Head IT Security, PostFinance AG
“PostFinance has chosen Exeon.NDR because of its open and future-proof architecture. Not needing any hardware sensors and being able to control data flows, we didn’t have to make any significant changes to our existing infrastructure. We are also convinced by the cooperation with the competent and technically outstanding Exeon team.”

Regional Practice Head, Wipro
“Exeon is the ideal solution for transitioning from a legacy SOC to a Next-Generation SOC. It enhances detection capabilities, minimizes alert noise, and significantly reduces costs.”

CEO & Founder, Planzer
“As CEO and owner of a fast moving, international logistics company, I cannot afford any system interruptions due to cyber incidents. With Exeon.NDR, we have found a Swiss solution to monitor our network and quickly detect cyber threats.”

Network & Security Engineer, Solothurner Spitäler
“Exeon is our cybersecurity alarm system, alerting us to any network anomalies. What also really convinced us is the platform’s intuitive interface—it has become a tool to reliably monitor and secure our data and network.”

Director of Cybersecurity Research, KuppingerCole
“The management and analyst interfaces are intuitive and can yield important insights for customers. Exeon’s approach to data retention helps customers keep data local for regulatory compliance and reduces costs for long-term storage by only retaining event metadata. The solution supports the most pertinent standards for exchanging threat information.”
See it with your own eyes.
Now that we’ve outlined all the reasons that make our NDR platform superior within the market, it’s time that you see it in action. Consult our security experts, no strings attached.