Why use ML in cybersecurity?
In cybersecurity, machine learning algorithms analyze patterns and learn from data to identify potential threats, making it a crucial tool in detecting and preventing cyber attacks.
Advancements in the field
Advancements in threat detection and response with machine learning
The ever-evolving landscape of cyber threats demands a proactive and adaptive approach to security. Machine learning in cybersecurity excels at detecting new threats, including zero-day exploits and advanced persistent threats (APTs). By analyzing vast amounts of data through sophisticated algorithms, machine learning can identify anomalies that indicate potential security breaches, often faster and more accurately than traditional methods. This advanced capability is a cornerstone of modern threat detection and response strategies.
Collaboration between AI and human expertise
A balanced approach that combines the advanced algorithmic analysis with the nuanced understanding of human experts is crucial for an effective defense strategy. This collaborative model ensures a smooth integration of human decision-making in cybersecurity, fostering a more resilient and adaptable framework.
3 reasons why machine learning is critical against corporate cyber threats
- Integrating Emerging Technologies in Cybersecurity: The integration of emerging technologies like quantum computing and artificial intelligence is transforming cybersecurity. These advancements offer enhanced security capabilities but also present new challenges, requiring specialized skills for effective management and implementation. Their potential for bolstering cybersecurity measures is immense, necessitating an adaptive approach in security strategies.
- Machine Learning in Identifying Insider Threats: Insider threats represent a distinct challenge in the field of digital security. Advanced algorithms excel in monitoring and analyzing user behaviors within an organization, to identify unusual patterns that may indicate a security risk from within. These sophisticated tools provide an essential layer of defense by continuously scanning for activities that deviate from the norm, thereby enhancing the organization’s ability to address potential internal security breaches.
- Enhancing Cyber Resilience through Advanced Analytics: In today’s digital world, the importance of cyber resilience cannot be overstated. Advanced analytics play a crucial role in strengthening this resilience, providing insights that go beyond threat detection. By analyzing security data, organizations can gain a deeper understanding of attack patterns, which is invaluable in forming robust security policies and practices. This continuous analysis helps in adapting to the evolving nature of threats and maintaining a strong defense against potential attacks.

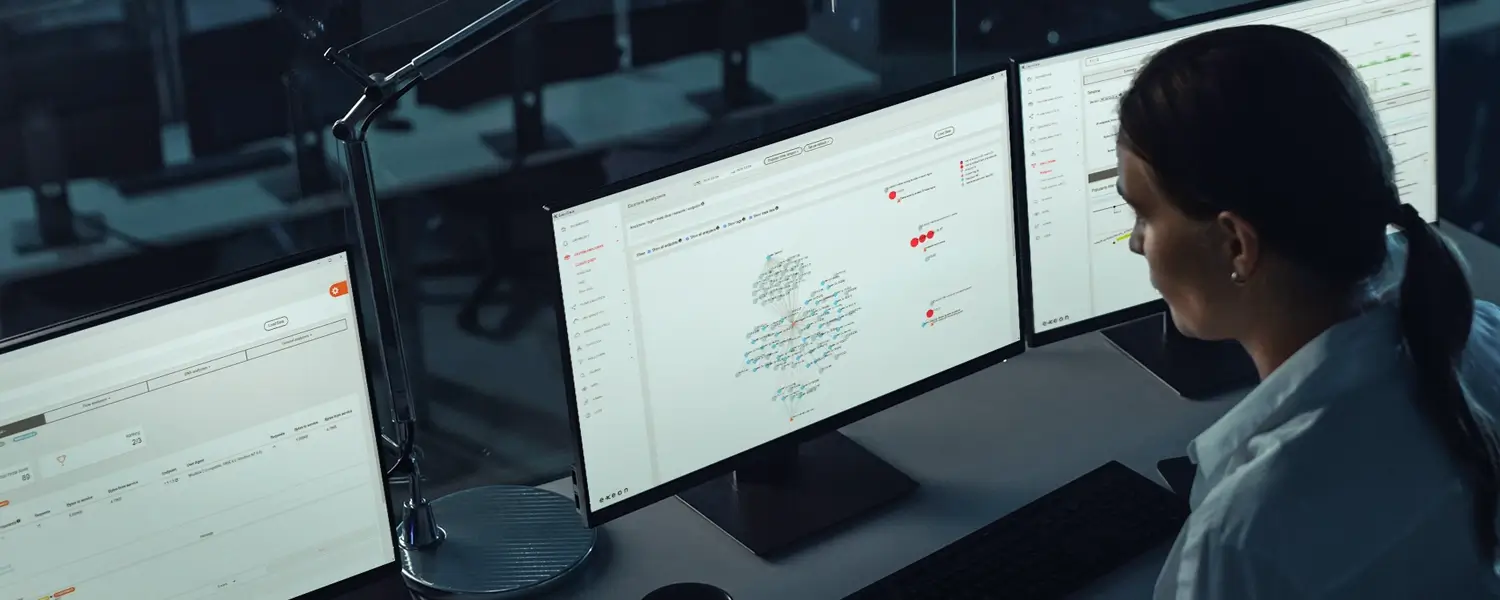
Exeon’s solution is equipped with powerful machine learning algorithms designed to detect sophisticated cyber threats by analyzing log data.
The intersection of cybersecurity and regulatory compliance
As technology evolves, so do the requirements for regulatory compliance in cybersecurity. Aligning cybersecurity practices with regulatory demands is not just about adherence to laws; it’s about ensuring that organizations maintain the highest level of security while protecting sensitive data and customer information. This balance is essential for building trust and ensuring long-term success in the digital marketplace.
Future of Machine Learning in Cybersecurity
Continuous learning systems, powered by machine learning in cybersecurity, are becoming critical for effective defense against evolving threats. These adaptive systems continuously update and refine their algorithms to stay ahead of emerging risks, ensuring that security measures remain robust and effective. By integrating machine learning-driven continuous learning systems, organizations can future-proof their cybersecurity strategies, seamlessly adapting to new challenges and maintaining resilience in an ever-changing digital landscape.
A bright future: Machine learning revolutionizes cybersecurity
The future of Machine Learning in cybersecurity is poised for groundbreaking advancements, shaping the way organizations defend against ever-evolving cyber threats. With rapid innovation in automated systems, machine learning is becoming an indispensable cornerstone of modern cybersecurity strategies.
Integrating ML with blockchain and IoT for advanced security
The integration of machine learning with emerging technologies like blockchain and the Internet of Things (IoT) is set to further revolutionize security capabilities, enabling more robust, scalable, and intelligent defenses against cyberattacks.
Addressing modern challenges in cybersecurity
As cyber threats grow increasingly complex, organizations face challenges such as IT staff shortages and the exponential growth of data generated by modern networks. Machine learning in cybersecurity addresses these hurdles by automating threat detection and enabling systems to identify deceptive attack patterns that are often too subtle for traditional methods.
Transforming network monitoring with predictive analytics
Predictive analytics, powered by machine learning, is transforming network monitoring and threat management. These tools excel in identifying both known and unknown attack patterns, providing early warnings and actionable insights to preempt potential breaches.
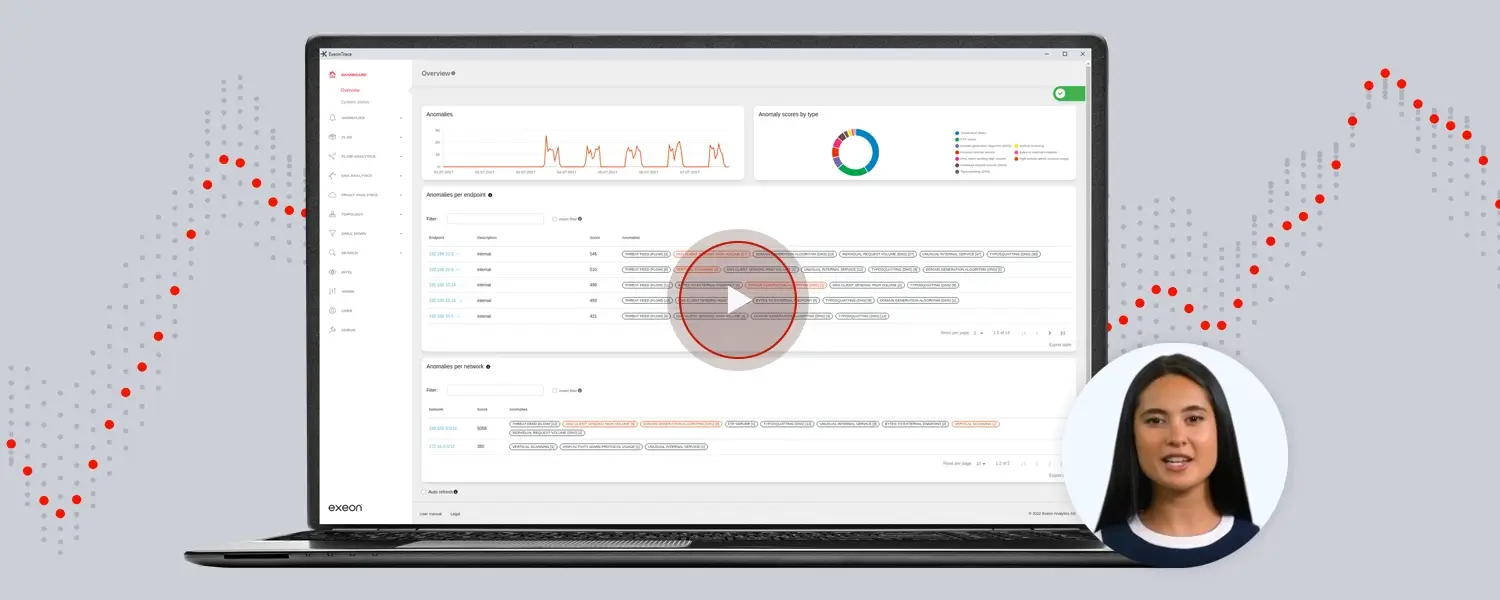
“We, at Exeon, leverage machine learning algorithms and its baselining capabilities for the NDR platform Exeon.NDR. The application of ML ranges from detections for domain generation algorithms to traffic volume analytics, command-and-control channel detections and identifying lateral movement.
In our blog post on the future of network security, we explain the general benefits of using ML and predictive analytics.”
— Andreas Hunkeler, Senior Cybersecurity Engineer
The fusion of machine learning with advanced technologies offers unparalleled opportunities to enhance cyber resilience. Organizations that integrate machine learning into their cybersecurity frameworks will not only keep pace with evolving threats but also set new standards for proactive defense, making machine learning in cybersecurity an essential driver of innovation and protection.
Exeon.NDR: game changer in cybersecurity
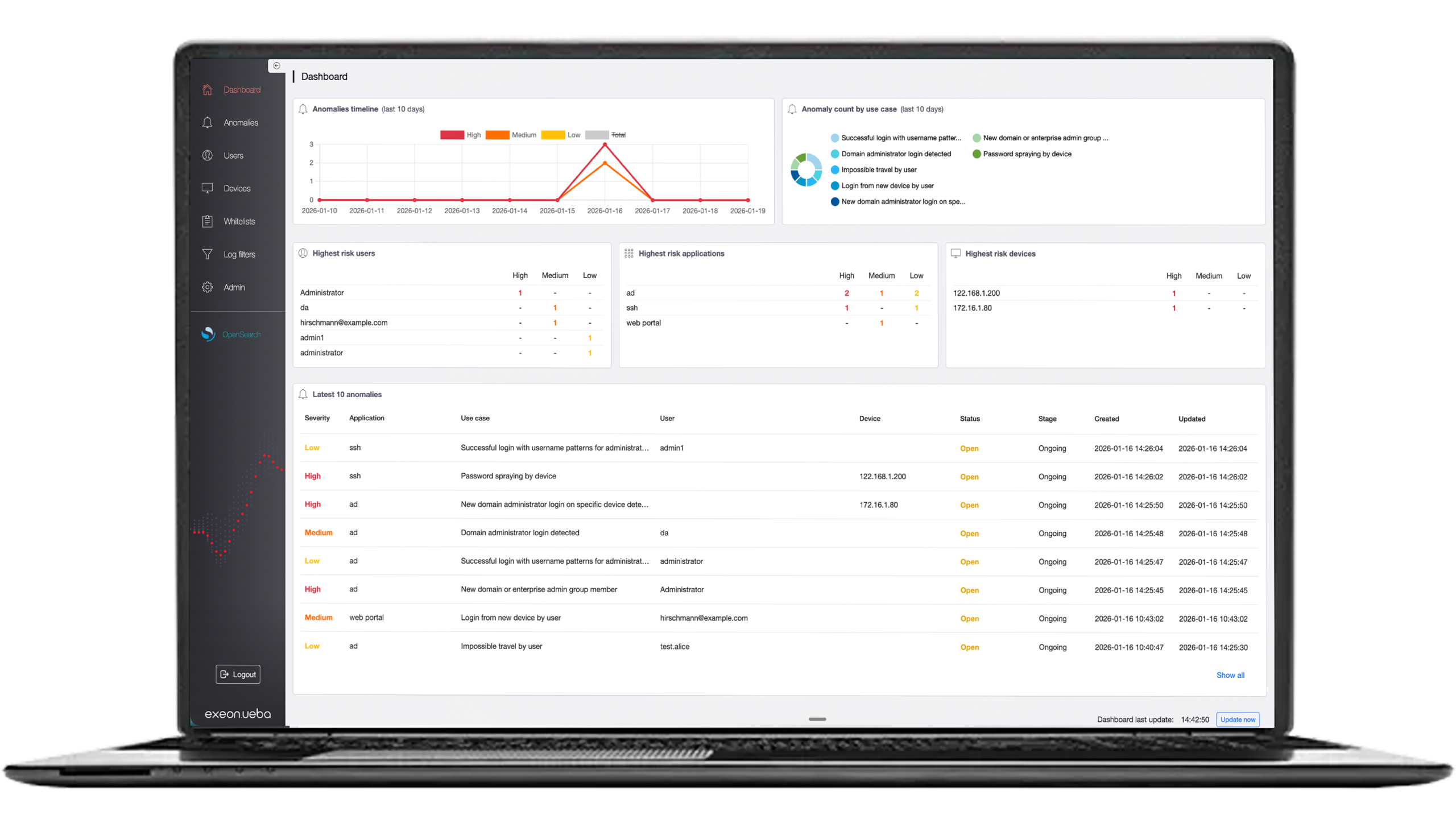
Exeon.NDR, a premier Network Detection and Response solution developed by Exeon, harnesses the power of machine learning to revolutionize cybersecurity. By addressing various IT security challenges, it not only assists security teams in their routine tasks but also significantly elevates an organization’s cybersecurity posture.
Cutting-edge with advanced threat detection: leveraging machine learning algorithms with Exeon.NDR means identifying sophisticated cyber threats swiftly. Its capability for rapid network anomaly detection sets it apart, providing a critical edge in the fast-paced realm of cybersecurity. This advanced detection is a testament to the power of machine learning in identifying and reacting to cyber threats in a timely manner.
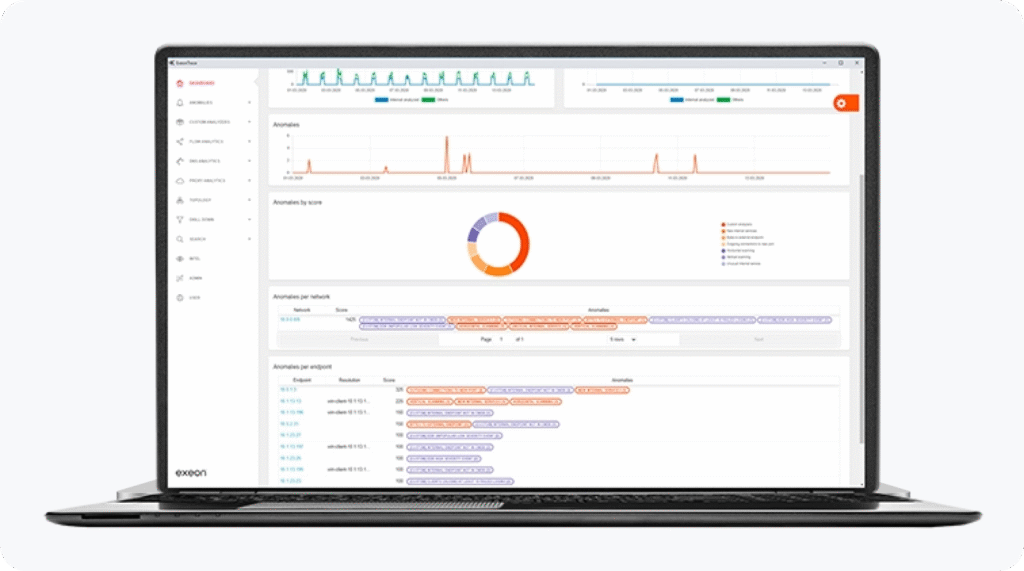
Incorporating Exeon.NDR into a cybersecurity strategy offers a modern approach to digital threats. Leveraging machine learning and AI, it improves threat detection and response, adding sophistication and efficiency to security operations. As cyber threats evolve, Exeon.NDR is key for organizations aiming to stay ahead and effectively protect their digital assets.