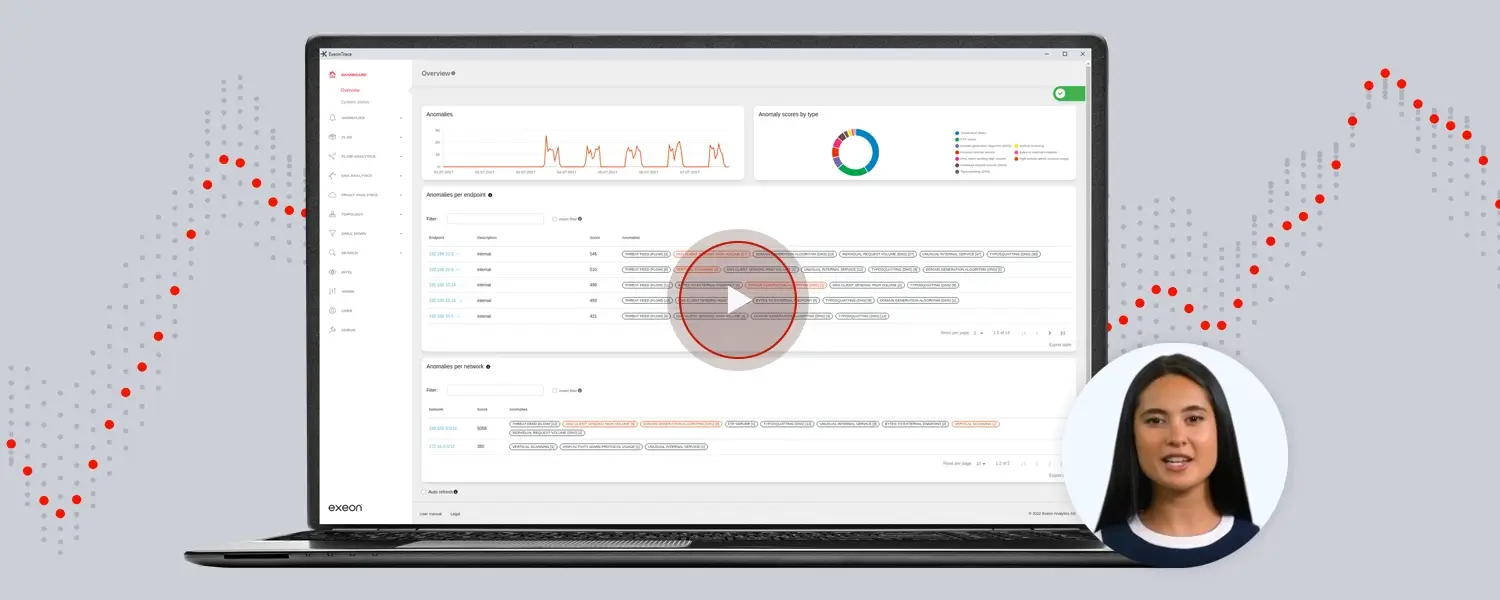
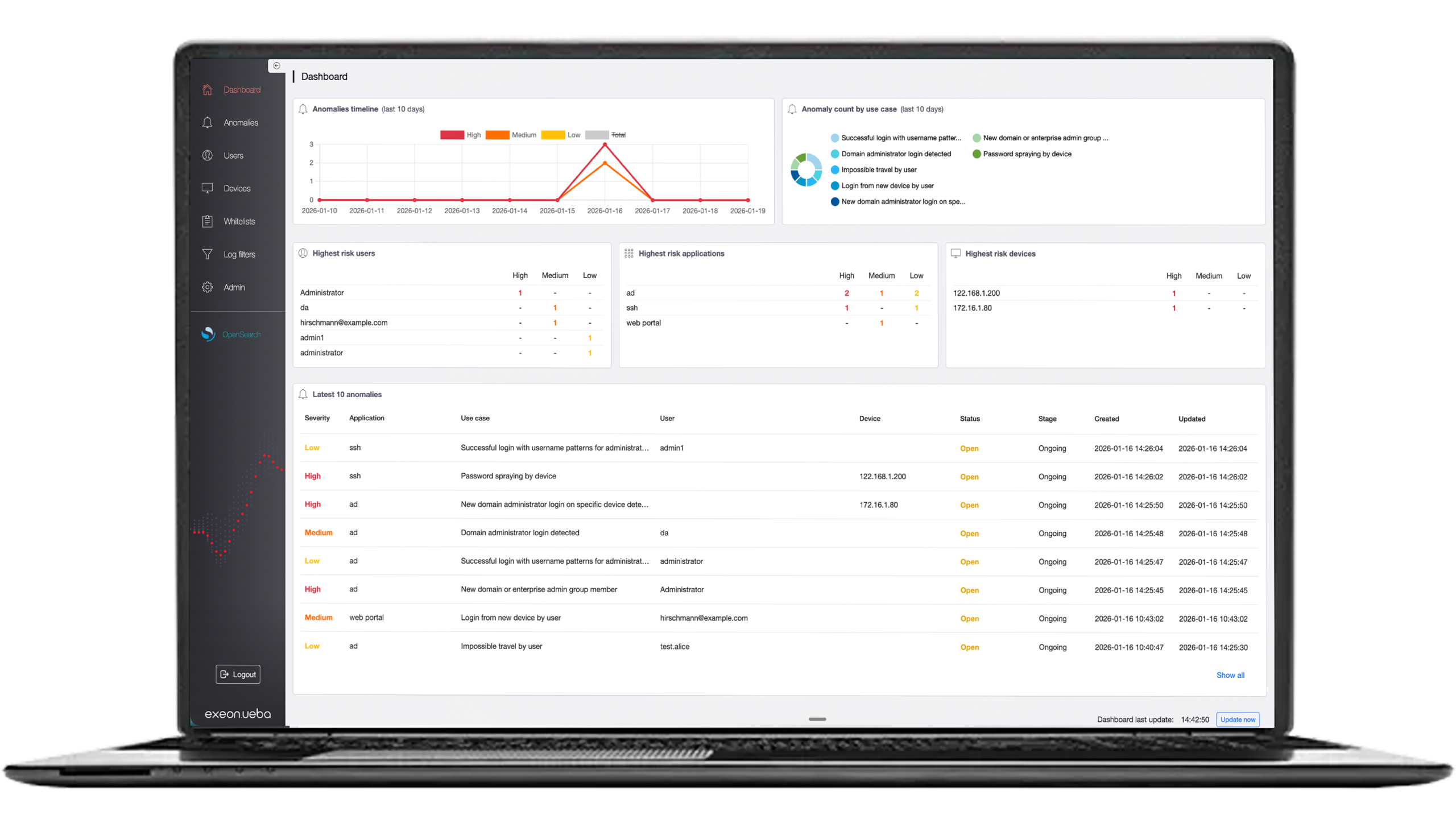
From Exeon’s security experts to you
As a team of cybersecurity experts, data scientists and innovators, we share insights gained from our research and work in the field—for today and the future.
Monthly Cyber Flash
Our monthly newsletter provides you with insights from IT security decision-makers and technical experts, events, webinars, and industry news. Sign up below!