All About the Common Vulnerability Scoring System
CVSS and threat scoring enables you to reach cyber resilience—proactive vulnerability management starts here.

What is Common Vulnerability Scoring System (CVSS)?
The key to prioritizing cybersecurity threats and maximizing risk management
What is CVSS and how does it work?
CVSS is a free and open industry standard to assess the severity of vulnerabilities. It helps you evaluate and rank reported vulnerabilities in a standardized and repeatable way. It is a general, i.e. universal assessment method, made to compare vulnerabilities in different applications and from different vendors. Understanding it helps organizations prioritize patching, integrate threat intelligence, and meet compliance requirements efficiently, ultimately enhancing their overall cybersecurity posture.
Not all security flaws pose the same level of risk, and without a structured approach, teams may waste time patching low-impact issues while missing high-severity threats. CVSS plays a critical role by offering a standardized scoring system, it allows security teams to align their remediation efforts with business risk rather than just technical severity, improve collaboration between IT, security, and compliance teams by speaking a common language of risk, justify security investments by demonstrating the potential impact of unpatched vulnerabilities.
Additionally, CVSS scores are often integrated into security platforms, enabling automation in vulnerability management, reducing manual effort, and ensuring real-time risk assessment.
Why use this framework?
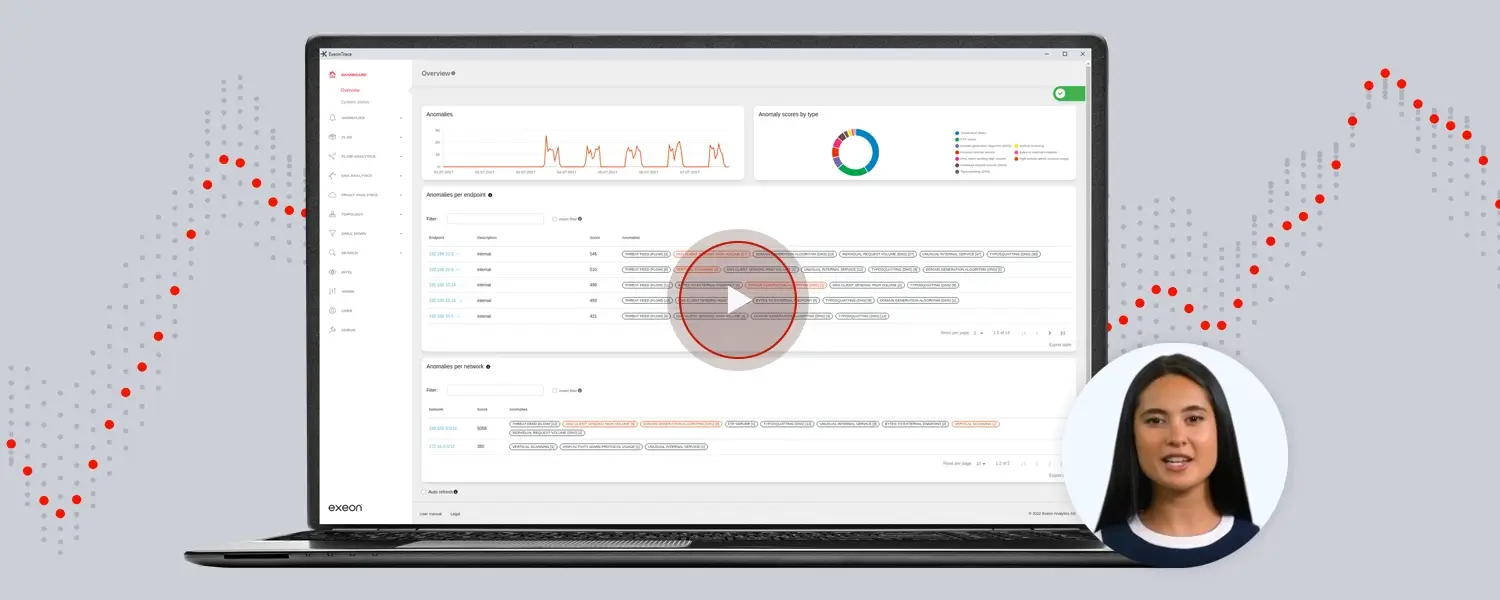
Network Detection and Response (NDR) goes beyond Endpoint Detection and Response (EDR) by integrating machine learning with a holistic approach to cybersecurity. Unlike EDR, NDR uses behavioral anomaly detection to identify both known and emerging threats. It doesn’t rely solely on historical data but adapts to evolving threats, making it effective against zero-day attacks.
By prioritizing alerts based on risk levels and leveraging CVSS scores, NDR optimizes resource allocation and enables swift, targeted responses to potential threats.
When coupled with risk-based alerting (RBA), NDR ensures that high-risk events receive immediate attention, reducing alert fatigue and enhancing overall cybersecurity posture.
Its benefits for your organization
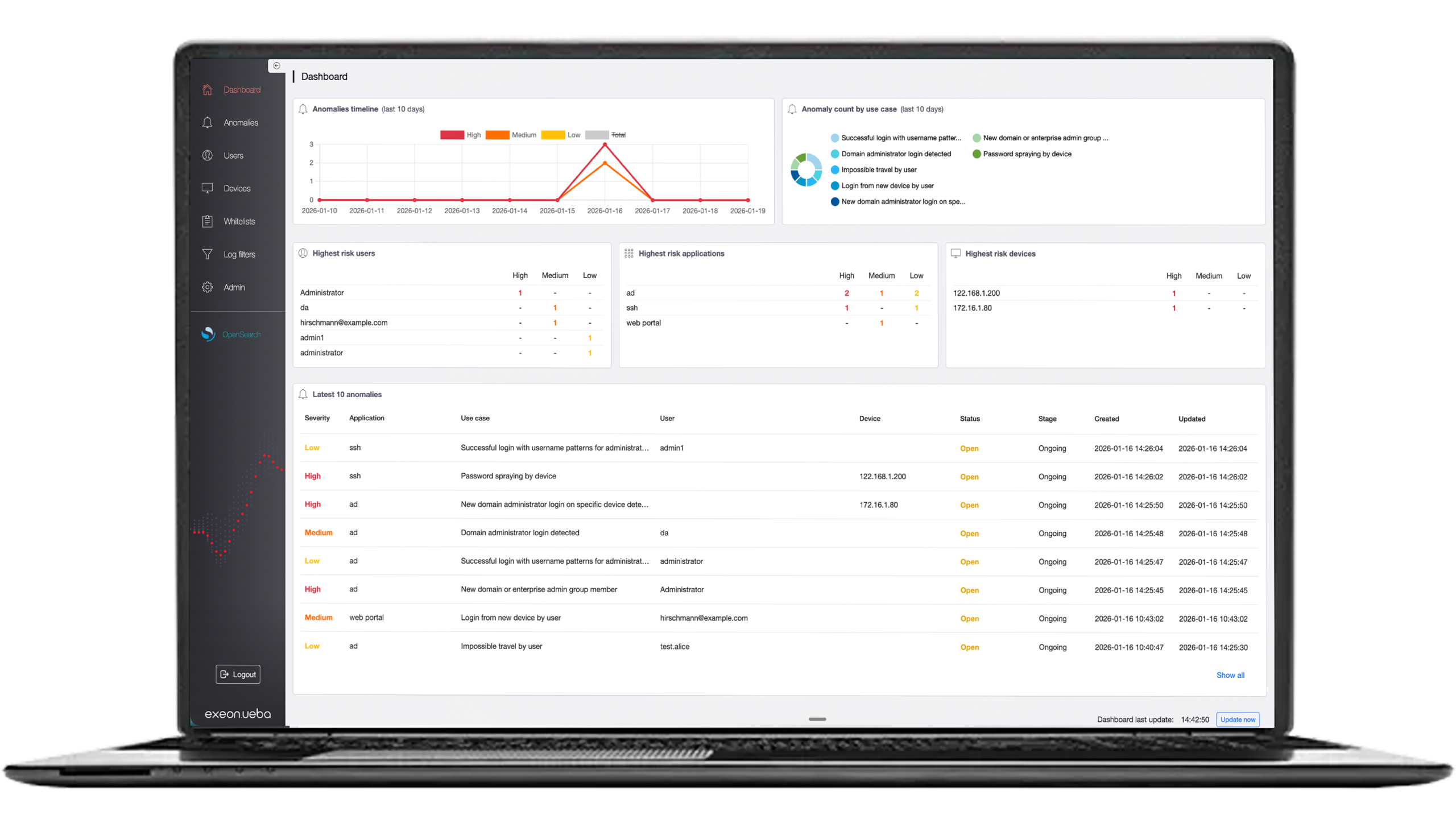
As a standardized framework for assessing the severity of vulnerabilities based on predefined metrics, CVSS calculates a severity score ranging from 0.0 to 10.0, with 10.0 representing the highest severity. It utilizes base metrics, impact metrics, temporal metrics, and environmental metrics to provide a comprehensive evaluation of vulnerabilities. Understanding CVSS and Common Vulnerabilities and Exposures (CVE) offers several benefits for organizations:
Resource allocation
By utilizing CVE identifiers, organizations can prioritize resources for patching and remediation based on the level of risk posed by each vulnerability.
Interoperability
Standardization through CVSS and CVE enhances interoperability between security tools and systems, enabling more accurate detection and response to potential threats.
Threat intelligence integration
Combined with CVE, it facilitates the integration of threat intelligence feeds into security tools, enabling the identification and prioritization of potential threats based on their association with known vulnerabilities.
Enhanced incident response
Knowledge of scores and CVE identifiers enables faster and more effective incident response by providing actionable information to investigate and mitigate security incidents promptly.
Compliance requirements
Understanding CVSS and CVE helps organizations align with regulatory compliance requirements by enabling them to identify, prioritize, and address vulnerabilities in a timely manner.
Risk assessment
It allows organizations to assess the severity of vulnerabilities and prioritize patches and mitigation efforts effectively, focusing resources on addressing the most critical vulnerabilities first.
For a guide on how to integrate it within your systems and optimize your security, download our booklet below!
Download the CVSS guide
A guide to help you prioritize patching, enhance interoperability, integrate threat intelligence, improve incident response, meet compliance requirements, and effectively manage security risks.
Insights from our security experts
Cut through the cyber noise: blogs written by our thought leaders in AI-powered cybersecurity.