Definition
An Intrusion Prevention System (IPS) is an inline security tool that actively monitors and analyzes network traffic for potential threats or malicious activities. This system uses various methods to detect threats depending on predefined signatures, established behavior, or privacy policy. The main function of an IPS is to prevent threats by automatically taking action when suspicious activity is detected.
IPS vs. IDS
Although many people confuse IPS with Intrusion Detection System (IDS), the IPS was designed as a more advanced version of the IDS.
- As the name suggests, the Intrusion Detection System is helpful in detecting potential threats and it mainly serves in alerting the administrator where further investigation is needed.
- IPS, on the other hand, goes beyond detection by immediately blocking intrusive actions on the network. This proactive defence provided by the IPS should increase network security and reduce the risk of data leakage making an IPS an important component of any cybersecurity strategy.
How does IPS work?
An IPS is typically placed behind the firewall, between the source and the destination – every packet must pass through the IPS where it gets inspected before it can enter your network. This feature helps it prevent intrusion in real time, using three main methods to detect unusual behavior.
- Signature-based detection: With this detection method, the IPS uses its database of previously prevented threats to detect new network attacks. It takes action when a new packet matches one of the predefined signatures.
Cons: When using this method, the signature database must be regularly updated to prevent intrusion from the latest cyber-attackers. - Anomaly-based detection: Here, machine learning is used to establish a baseline model of normal network behavior. The anomaly-based IPS then analyzes ongoing traffic and compares it to the established model. It takes preventive action when it identifies activity that deviates from the normal baseline. In comparison to the signature-based method, the anomaly detection model can stop both known and unknown threats.
Cons: If the baseline is not accurately defined, or there are frequent changes in the normal activity the anomaly-based IPS may often generate false positives. - Policy-based detection: Policy-based IPS uses a set of network policies defined by the security team or the network administrator to detect malicious activity. The IPS enforces these policies by monitoring traffic and stops any action that violates these rules.
Cons: It’s very precise but requires extensive work on the creation and maintenance of the customized privacy policy.
Main methods of prevention used
- Blocking Malicious Traffic: The IPS inspects incoming and outgoing traffic and blocks packets that match known threat signatures or exhibit suspicious behavior. It’s highly effective at preventing known threats and immediate risks.
- Bandwidth Throttling: For potentially suspicious traffic that doesn’t warrant outright blocking, the IPS can limit the bandwidth allocated to it, reducing its impact. Useful for managing network resources and mitigating the effect of suspicious activities without fully disrupting legitimate traffic.
- Resetting Connections: when a threat is detected within an ongoing session, the IPS can reset the connection to disrupt the malicious activity. Effective at stopping ongoing attacks and preventing further malicious actions.
- Altering Configurations: The IPS can automatically apply patches, update security policies, or change configurations to mitigate detected threats Provides dynamic and adaptive protection by ensuring the security environment is up-to-date and resilient against emerging threats.
Types of deployments
- Network-Based Intrusion Prevention System (NIPS): A NIPS is installed on strategic points within the network, usually behind the firewall. It monitors traffic from all devices and is ideal for detecting a wide range of network threats, such as DoS attacks, unauthorized access attempts, or malware propagation.
- Host-Based Intrusion Prevention System (HIPS): This prevention system is deployed on specific endpoints; it monitors and controls the network only on those individual devices. It is recommended to pair a host-based intrusion prevention system with a network-based one, as it specializes in detecting threats that the NIPS may have missed.
- Network Behavior Analysis (NBA): The NBA prevention system uses the anomaly-based method to monitor traffic patterns and detect unusual behavior that may indicate potential threats. The network behavior analysis IPS focuses on the overall behavior instead of individual signatures. Hence, it’s effective at identifying new attacks that do not match any of the existing threat signatures.
- Wireless Intrusion Prevention System (WIPS): A WIPS is designed for wireless networks specifically. It is used to analyze and terminate the connection of unauthorized users or devices accessing the monitored Wi-Fi network. The Wireless Intrusion Prevention System is best suited for large organizations that rely on wireless networks for their data and transactions such as: corporate offices, retail stores, healthcare facilities, education institutions, and public spaces.

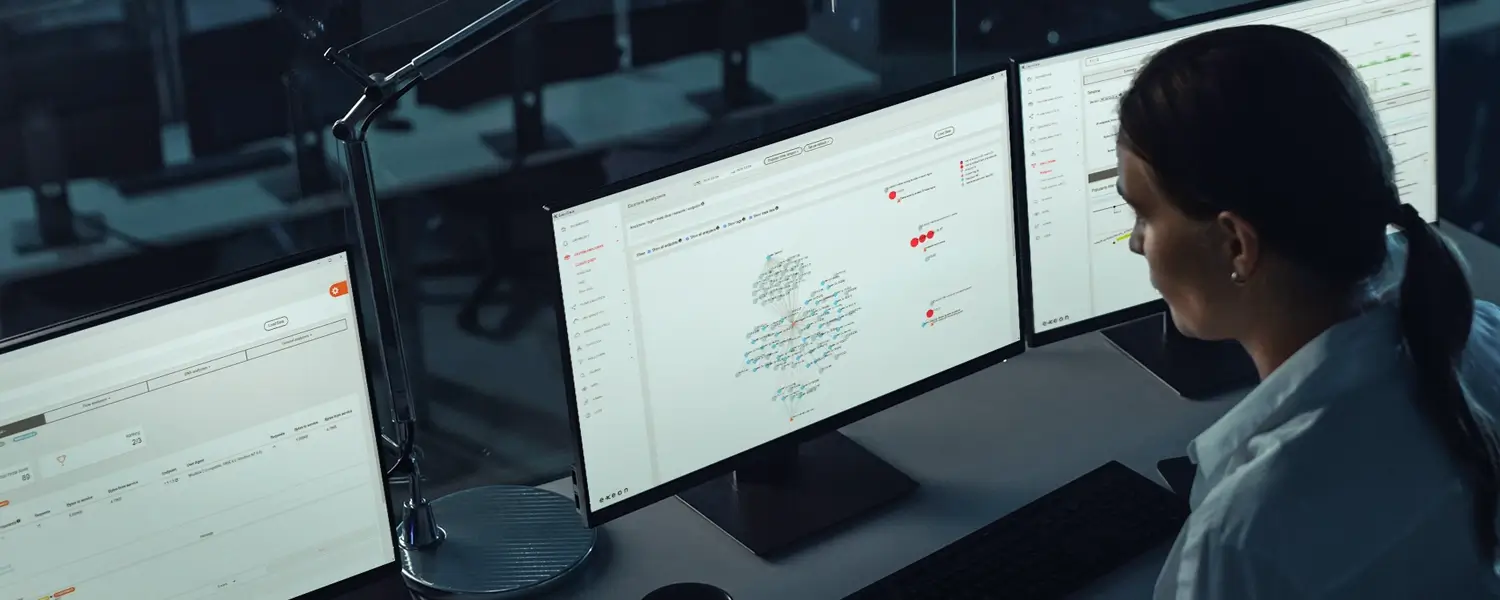
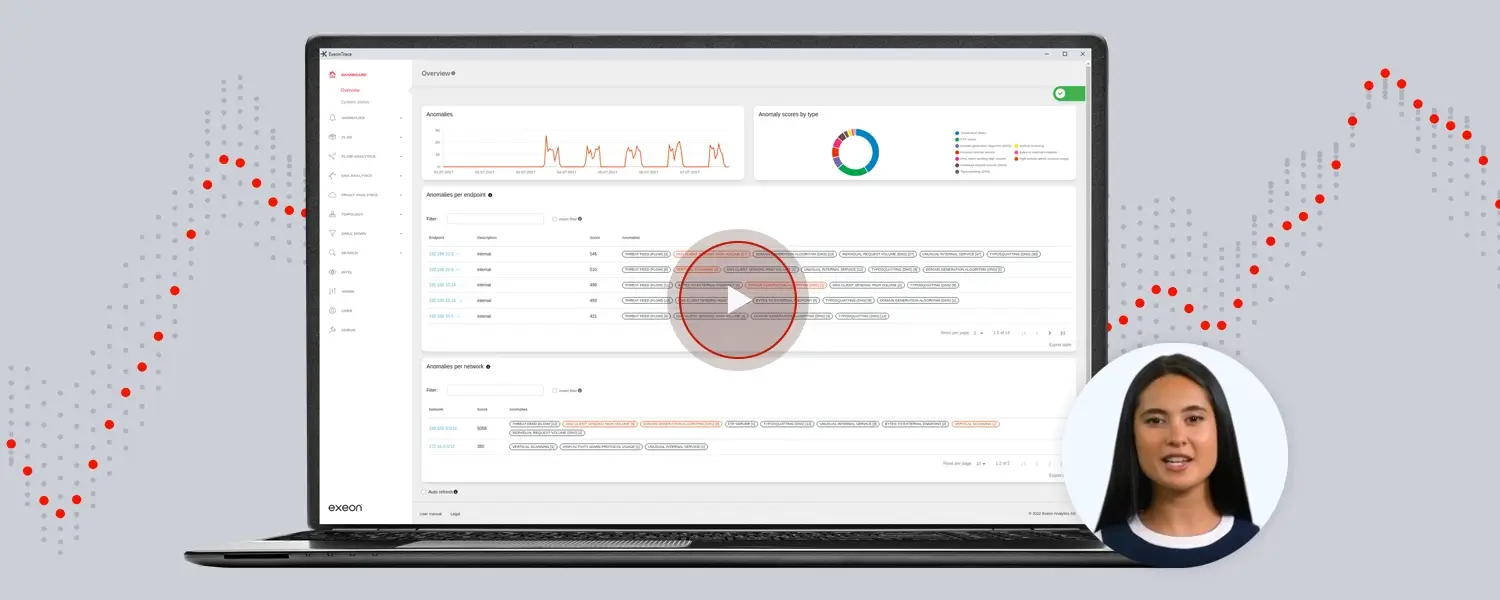
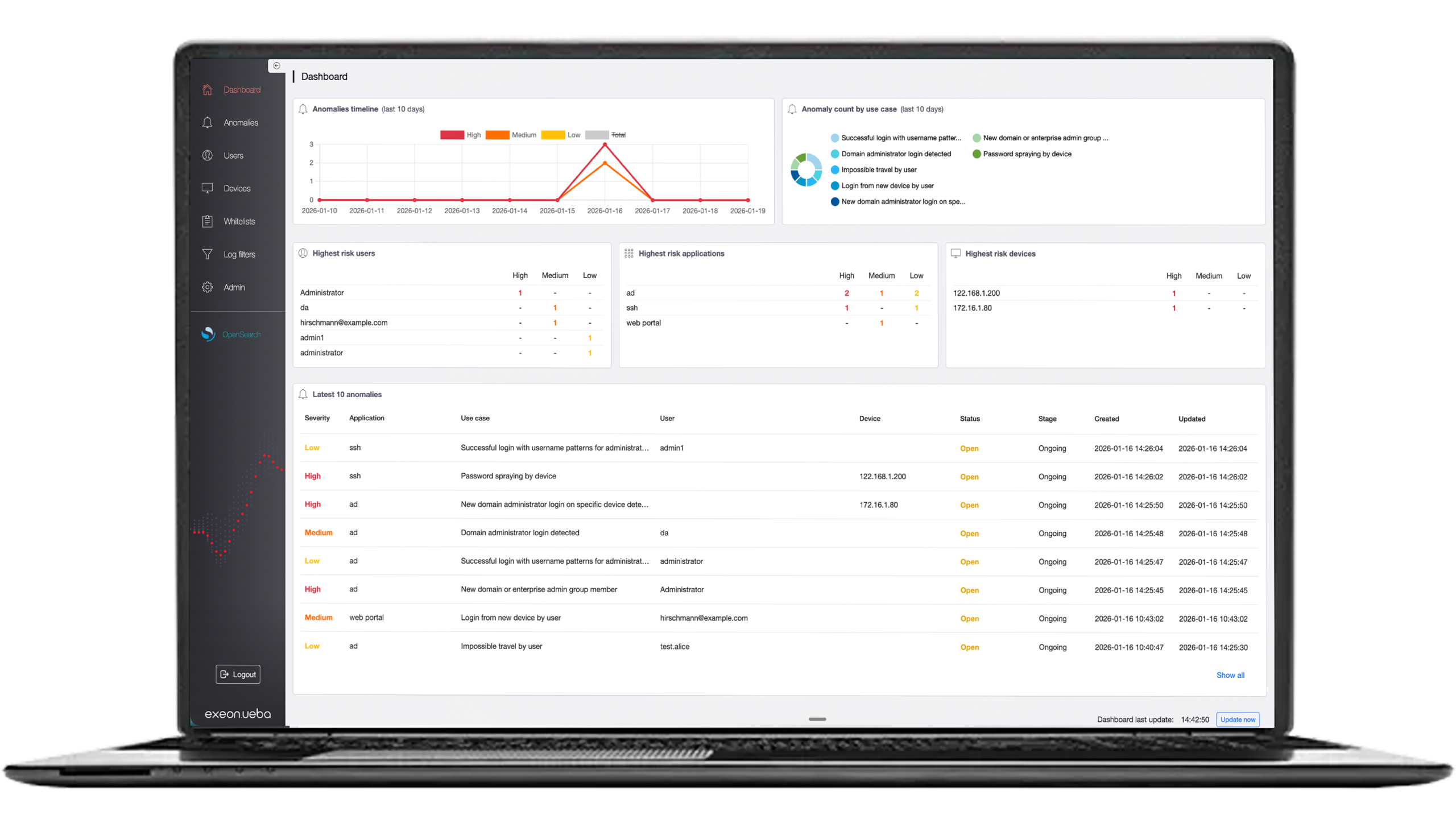
IPS provides real-time threat prevention, while NDR offers deeper network visibility and advanced threat detection for identify more complex incidents.
Its benefits
- Real-time Threat Prevention: The Intrusion Prevention System, not only detects but also prevents threats proactively by blocking malicious IP addresses or terminating suspicious sessions in real time.
- Strengthened Data Protection: Using an IPS is crucial when dealing with a large set of sensitive data. By immediately blocking unauthorized users and suspicious activity, an IPS reduces the risk of data breach, helping you protect confidential information.
- Improved Network Performance: Malicious attempts consume bandwidth and cause slowdowns in your system. An IPS will improve your overall performance and provide a smoother user experience by continuously filtering unauthorized traffic and minimizing the impact of security incidents.
- Security-Standard Compliance: An IPS will help your business meet the regulatory compliances and industry standards set by frameworks such as Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standard (PCI-DSS), and General Data Protection Regulation (GDPR).
- Enhanced Network Visibility: Continuous monitoring and detailed reporting provide a clear view of network activity, helping to identify and address vulnerabilities.
- Efficiency: It’s an automated tool so it requires minimal to no effort from the network security team. Since an IPS detects malicious activity before it can pass through the system, it also helps simplify further controls of the advanced security stages.
Disadvantages
- False Positives: Due to limited updates, complex environments, or misconfigurations, the Intrusion Prevention System can often incorrectly mark benign traffic as malicious and/or fail to detect actual threats.
- Performance Lag: An IPS needs extensive bandwidth to operate efficiently. In high traffic environments, it can struggle handling the large data volume and therefore cause delays in the system.
- Configuration & Maintenance Costs: To ensure proper performance, it needs in-depth configuration of the dataset that will be used to compare and detect malicious activity. Moreover, constant maintenance is a must to keep your business protected from all new threats as well as the predefined ones. This can be costly and may not be suited for all businesses.
How NDR helps
Faster & more precise detection: Network Detection and Response (NDR) extends IPS with machine learning and advanced analysis protocols.
While IPS relies on signature-based detection and often misses zero-day attacks and encrypted traffic, NDR continuously analyzes network traffic and detects anomalous behavior. It also provides a more holistic threat detection, reduces false positives, and supports network forensics to better investigate and prevent security incidents.