Definition
Security Orchestration, Automation, and Response, also known as SOAR, is a category of security solutions that combines three core functions:
- Orchestration
- Automation
- Response
These platforms gather security data and alerts from multiple sources, automate responses, and streamline security management through comprehensive workflows.
These functions are essential in elevating an organization’s ability to manage and respond to threats, with security operations automation playing a crucial role in enhancing the efficiency of cybersecurity teams.
Security Operations and SOAR
Security operations play a pivotal role in the implementation and effectiveness of Security Orchestration, Automation, and Response solutions. These platforms are designed to automate and streamline security workflows, enabling the security team to manage and mitigate risks more efficiently and effectively.
By integrating various security tools and systems, SOAR platforms provide a unified approach to managing and mitigating threats. This orchestration automation and response capability ensures that security operations are not only more cohesive, but also more proactive in addressing potential security breaches.
As a result, organizations can significantly enhance their overall security posture and reduce the time and effort required to handle security incidents.
The Role of Security Operations in SOAR
Security operations teams are at the forefront of monitoring, detecting, and responding to security incidents. In a SOAR environment, the security team collaborates within a security operations center (SOC) to ensure that security incidents are properly identified, analyzed, and responded to.
The role of security teams includes:
- Monitoring Security Alerts and Incidents: Continuously overseeing security alerts to identify potential threats.
- Analyzing Security Data: Utilizing the SOAR platform to analyze security data and pinpoint suspicious activities.
- Responding to Security Incidents: Leveraging SOAR playbooks and workflows to execute timely and effective incident responses.
- Collaborating with Other Teams: Working alongside incident response and threat intelligence teams to ensure a coordinated approach to incident management.
- Improving Workflows: Regularly updating and refining SOAR workflows and playbooks to enhance the efficiency of security operations.
By integrating these responsibilities, security operations teams can maximize the benefits of SOAR platforms, ensuring a robust and responsive security infrastructure.

SOAR streamlines cybersecurity by automating alert management, investigation, and response, reducing overwhelm, aiming for efficient incident handling.
Security Orchestration and Automation
Security orchestration and automation are critical components of SOAR solutions. Security orchestration involves the coordination and integration of multiple security tools and systems to provide a unified view of security operations.
This integration allows for seamless data flow and communication between different security technologies, enhancing the overall effectiveness of the security infrastructure. On the other hand, security automation involves the use of automated workflows and playbooks to respond to security incidents.
By automating repetitive and time-consuming tasks, security automation frees up security analysts to focus on more complex and high-value tasks, thereby improving the efficiency and effectiveness of security operations.
How SOAR Automates Security Processes
SOAR platforms automate security processes by using pre-defined playbooks and workflows to respond to security incidents. These playbooks and workflows are designed to automate repetitive and time-consuming tasks, freeing up security analysts to focus on more complex and high-value tasks.
SOAR automation includes:
- Automated Incident Response: SOAR platforms can automatically respond to security incidents using pre-defined playbooks and workflows, ensuring a swift and consistent response.
- Automated Threat Detection: Utilizing machine learning and advanced analytics, SOAR platforms can automatically detect potential threats, reducing the time to identify and mitigate risks.
- Automated Security Alerts: Based on predefined rules and criteria, SOAR platforms can automatically generate security alerts, ensuring that security teams are promptly informed of any suspicious activities.
By automating these processes, SOAR platforms significantly enhance the efficiency and effectiveness of security operations, allowing security teams to stay ahead of potential threats.
Challenges addressed
SOAR addresses several significant challenges in cybersecurity. A key component in managing these challenges is the security team within the security operations center (SOC), which utilizes SOAR platforms to collect, analyze, and respond to security data and threats.
One primary issue is the high volume of security alerts that organizations face on a daily basis. Managing these alerts manually can be overwhelming and inefficient.
SOAR platforms automate the prioritization, investigation, and response processes, bridging the gap between different security tools and systems, and allowing for a more cohesive and efficient response to incidents.
Common use cases
- Incident Response: Automating the detection, investigation, and remediation of security incidents.
- Threat Intelligence Management: Integrating and correlating threat intelligence feeds to identify potential threats.
- Vulnerability Management: Automating the process of identifying, prioritizing, and remediating vulnerabilities.
- Compliance and Reporting: Streamlining the collection of data and generation of reports to meet compliance requirements.

Incident Response and Threat Intelligence Management
Incident response and threat intelligence management are critical components of SOAR solutions. Incident response involves the process of responding to security incidents, while threat intelligence management involves the collection, analysis, and dissemination of threat intelligence to support incident response.
SOAR platforms provide robust capabilities in these areas, including:
- Incident Response Playbooks: Pre-defined playbooks for responding to security incidents, ensuring a consistent and effective response.
- Threat Intelligence Feeds: Integration with threat intelligence feeds to provide real-time threat intelligence, enhancing the ability to detect and respond to emerging threats.
- Threat Intelligence Analysis: Advanced analytics to analyze threat intelligence, identify potential threats, and support incident response efforts.
By automating security processes and providing comprehensive incident response and threat intelligence management capabilities, SOAR platforms enable security teams to respond more efficiently and effectively to security incidents.
This holistic approach ensures that organizations can maintain a strong security posture in the face of evolving cyber threats.
What are the key benefits of SOAR?
- Efficiency: Automates repetitive tasks, freeing up security analysts to focus on more complex issues.
- Consistency: Ensures that responses to incidents follow best practices and are consistent across the organization.
- Dashboards and Reporting: Tools for monitoring security operations and generating detailed reports.
- Scalability: Ensuring the SOAR platform can scale with the growing size and complexity of the organization’s security needs.
What does a SOAR platform include?
SOAR platforms typically include the following components:
- Playbooks: Predefined workflows that guide the automated response to specific types of security incidents.
- Integration Connectivity with various security tools and systems, such as SIEM (Security Information and Event Management), firewalls, and endpoint protection platforms.
- Dashboards and Reporting: Tools for monitoring security operations and generating detailed reports.
- Case Management: Features for tracking and managing security incidents from detection to resolution.
Challenges
Despite its benefits, its implementation comes with challenges:
- Complexity: Integrating it with existing security infrastructure can be complex.
- Customization: Developing and maintaining playbooks and workflows require continuous effort and expertise.
- Scalability: Ensuring the SOAR platform can scale with the growing size and complexity of the organization’s security needs.
How it works with other tools
SOAR platforms are designed to integrate seamlessly with other security tools and systems. This integration allows for the automated collection and correlation of data from various sources, such as Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), firewalls, and threat intelligence feeds.
By doing so, SOAR enhances the capabilities of these tools, providing a more comprehensive and coordinated approach to threat detection and response.
SOAR vs. SIEM
In cybersecurity, SOAR and SIEM are essential tools with distinct functions. SIEM focuses on collecting, analyzing, and correlating security events and logs from various sources, providing real-time monitoring and alerts. Its key functions include log management, event correlation, incident detection, and compliance reporting.
SOAR, on the other hand, not only collects and analyzes security data but also automates and orchestrates responses to incidents. While SIEM emphasizes detection and log analysis, SOAR enhances efficiency and effectiveness by automating and coordinating responses across the security infrastructure.
Together, they provide a comprehensive approach to cybersecurity.
How NDR helps
Our advanced threat detection platform, Exeon.NDR, provides comprehensive visibility into IT and OT networks, helping organizations identify vulnerabilities and detect malicious activity in real-time.
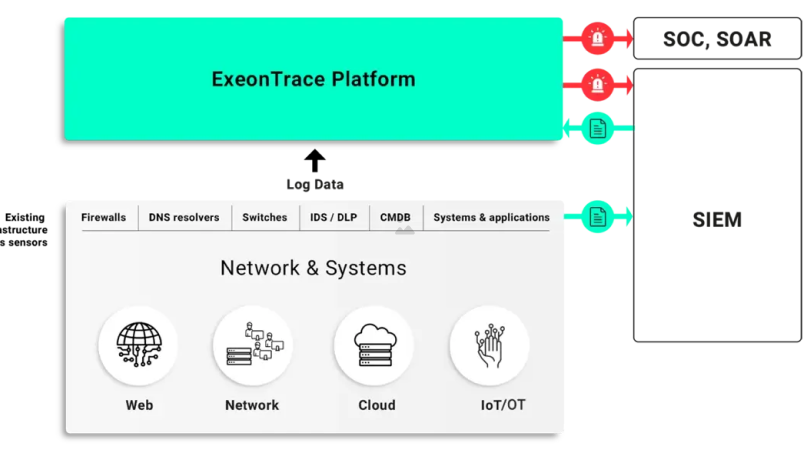
“By analyzing network log data instead of data-heavy traffic mirroring, it ensures that the platform is not affected by encryption and can operate without the need for hardware sensors.”
— Dr. Markus Happe, CTO, Exeon Analytics
Exeon.NDR enhances SOAR platforms by providing comprehensive visibility, efficient data handling, advanced threat detection, seamless integration, and AI-driven automation. These features collectively improve the efficiency and effectiveness of security operations.
SOAR is an indispensable component of modern cybersecurity strategies, offering automation, orchestration, and enhanced response capabilities.
While it comes with implementation challenges, the benefits in efficiency, consistency, and speed make it a considerable tool for organizations.
Solutions like Exeon.NDR bring forward the advanced capabilities of SOAR platforms, always staying ahead in the ever-evolving landscape of cyber threats.
Best Practices for SOAR Implementation
Implementing such a platform requires careful planning and execution to ensure successful integration with existing security tools and processes. Here are some best practices to consider:
- Define Clear Goals and Objectives: Start by identifying the specific security challenges you aim to address with SOAR, such as reducing alert fatigue or improving incident response times. Clear goals will guide your implementation strategy and help measure success.
- Assess Your Security Maturity: Evaluate your organization’s current security maturity level. Understanding your strengths and weaknesses will help determine the best approach for implementing a new platform and ensures that the platform complements your existing security operations.
- Choose the Right SOAR Platform: Select a SOAR platform that aligns with your organization’s needs and integrates seamlessly with your existing security tools. Consider factors such as scalability, ease of use, and the ability to customize workflows.
- Develop a Comprehensive Implementation Plan: Create a detailed plan that includes timelines, milestones, and resource allocation. A well-structured plan will ensure a smooth implementation process and help manage expectations across the organization.
- Train and Educate Security Teams: Provide thorough training and education to your security teams on the use and benefits of the SOAR platform. Ensuring that your team is well-versed in the platform’s capabilities will maximize its effectiveness and improve incident response.
- Monitor and Evaluate Performance: Continuously monitor and evaluate the performance of your SOAR platform. Regular assessments will help identify areas for improvement and ensure that the platform evolves with your organization’s security needs.
The Role of Threat Intelligence in SOAR
Threat intelligence plays a critical role in SOAR by providing context and enrichment to security data, enabling more effective incident response and threat detection.
Here are some ways threat intelligence enhances SOAR:
- Enriches Security Data: Threat intelligence feeds provide additional context to security data, enabling more accurate threat detection and incident response. By correlating threat intelligence with internal data, security teams can gain deeper insights into potential threats.
- Improves Incident Response: Threat intelligence helps security teams respond more effectively to incidents by providing information on the tactics, techniques, and procedures (TTPs) used by attackers. This knowledge allows for more informed decision-making and quicker mitigation of threats.
- Enhances Threat Detection: Threat intelligence enables SOAR platforms to detect threats more effectively by identifying patterns and anomalies in security data. Advanced analytics and machine learning can further enhance this capability, allowing for proactive threat detection.
- Supports Proactive Defense: Threat intelligence enables organizations to take a proactive approach to defense by identifying potential threats before they occur. By staying ahead of emerging threats, security teams can implement preventive measures and reduce the risk of successful attacks.
SOAR and Compliance
SOAR platforms can help organizations meet compliance requirements by providing a centralized platform for managing security incidents and data.
SOAR can support compliance requirements in the following areas:
- Streamlines Incident Response: SOAR platforms automate and orchestrate incident response processes, ensuring that incidents are handled consistently and in accordance with regulatory requirements. This consistency helps organizations maintain compliance with industry standards.
- Provides Audit Trails: SOAR platforms provide detailed audit trails of all security incidents and responses, enabling organizations to demonstrate compliance with regulatory requirements. These audit trails are essential for regulatory audits and internal reviews.
- Supports Data Retention: SOAR platforms can help organizations meet data retention requirements by storing security data and incident response records for extended periods. This capability ensures that organizations can access historical data when needed for compliance purposes.
- Enables Reporting: SOAR platforms provide reporting capabilities that enable organizations to generate compliance reports and demonstrate adherence to regulatory requirements. These reports can be customized to meet specific regulatory needs and provide valuable insights into security operations.
Future of SOAR
The future of SOAR is promising, with advancements in artificial intelligence, machine learning, and cloud computing expected to drive innovation and adoption.
Trends worth highlighting include:
- Increased Adoption of Cloud-Based SOAR: Cloud-based SOAR platforms will become more prevalent, offering greater scalability, flexibility, and cost savings. Organizations will benefit from the ability to quickly deploy and scale their SOAR solutions without the need for extensive on-premises infrastructure.
- Integration with Emerging Technologies: SOAR platforms will integrate with emerging technologies such as artificial intelligence, machine learning, and Internet of Things (IoT) devices. These integrations will enhance the capabilities of SOAR platforms, enabling more sophisticated threat detection and response.
- Greater Emphasis on Automation: SOAR platforms will place greater emphasis on automation, enabling organizations to respond more quickly and effectively to security incidents. Advanced automation will reduce the burden on security teams and allow them to focus on strategic initiatives.
- Improved Threat Intelligence: SOAR platforms will incorporate more advanced threat intelligence capabilities, enabling organizations to detect and respond to threats more effectively. Enhanced threat intelligence will provide deeper insights into the threat landscape and support proactive defense strategies.
By staying ahead of these trends, organizations can leverage the full potential of SOAR platforms to enhance their security operations and maintain a strong security posture in the face of evolving cyber threats.