Your Advanced Persistent Threats (APT) Guide
Cyber knowledge base article and whitepaper on actions to increase cybersecurity in the context of APTs.

What are Advanced Persistent Threats (APTs)?
Knowledge base article & download on actions to increase cybersecurity in the context of an advanced persistent threat attack.
Definition & key characteristics
Advanced Persistent Threats (APTs) are a category of sophisticated and highly targeted cyberattacks with persistence and stealth. The main objective of an advanced persistent attack is to acquire intelligence or crucial information to harm a broader system, exploit weaknesses, tarnish an organization’s reputation, or achieve a competitive edge.
Unlike many other threats that focus on immediate, short-term objectives, these attacks are typically long-term campaigns orchestrated by well-funded, skillful attackers.
Such sophisticated threats pose a significant concern for governments, businesses, and organizations worldwide.
The main characteristics are:
Persistence: APT actors are patient and persistent. They aim to establish and maintain unauthorized access to a target network or system for an extended period, often measured in months or years. This persistence allows them to conduct reconnaissance, gather intelligence, and exfiltrate data over time.
Targeted: Attackers invest significant effort in researching and profiling their victims, and understanding their networks, vulnerabilities, and objectives. Targets may include government agencies, defense contractors, financial institutions, critical infrastructure, and multinational corporations.
Sophistication: Threat actors employ advanced, constantly evolving techniques. They may use zero-day vulnerabilities (previously unknown software flaws), custom malware, and complex attack chains to compromise their targets. They often have access to substantial resources, including talented hackers and significant financial backing.
Stealth: APTs prioritize remaining undetected for as long as possible. They employ evasion techniques such as encryption, steganography (hiding malicious code within legitimate files), and living off the land (using built-in system tools) to avoid detection by security software and analysts.
Data Exfiltration: A primary objective of such attacks is to steal sensitive information, including intellectual property, trade secrets, classified documents, and personal data. Attackers carefully exfiltrate this data over time, minimizing the chances of detection.
Nation-State Involvement: While some of these groups consist of cybercriminal organizations, many attacks are attributed to nation-state actors. Governments engage in APT campaigns to gain a competitive advantage, steal military or diplomatic secrets, or further political or economic objectives.
Typical stages of an APT attack
An Advanced Persistent Threats (APT) attack typically includes the following 6 stages:
- Initial Compromise: Advanced Persistent Threats often begin with spear-phishing emails or other targeted attack vectors. Once an initial foothold is gained, attackers escalate privileges and establish persistence in the compromised systems.
- Lateral Movement: Advanced Persistent Threats actors move laterally within the network, searching for valuable targets and information. They might exploit vulnerabilities in poorly secured systems or employ privilege escalation techniques.
- Persistence Mechanisms: Attackers use various methods to maintain access, such as backdoors, remote access trojans (RATs), and compromised credentials. These mechanisms allow attackers to return to the system even if the initial point of entry is discovered and closed.
- Data Collection: Attackers conduct extensive reconnaissance to identify valuable data. They may employ keyloggers, screen capture tools, and network sniffers to monitor and collect information.
- Data Exfiltration: These attackers exfiltrate stolen data gradually and discreetly, often using encryption and covert communication channels to avoid detection.
- Covering Tracks: These attackers erase or alter logs, delete traces of their activities, and attempt to cover their tracks to evade detection.
Advanced Persistent Threat Groups and Attackers
APT groups and attackers are highly sophisticated and well-funded organizations that conduct targeted cyberattacks against specific organizations or industries. These groups are often characterized by their persistence, advanced techniques, and strategic objectives.
There are several types of APT groups, each with distinct motivations and methods:
Nation-State Sponsored APT Groups
These groups are backed by nation-states and conduct cyberattacks to further political, economic, or military objectives. They target other countries or organizations to steal confidential data, disrupt operations, or gain a strategic advantage. Nation-state APT groups are known for their resources and sophistication.
Cybercrime APT Groups
These groups operate with the primary goal of financial gain. They conduct cyberattacks to steal private data, such as credit card information, personal identities, or intellectual property, which can be sold or used for extortion. Cybercrime APT groups are driven by profit and often target financial institutions, e-commerce platforms, and large corporations.
Hacktivist APT Groups
Hacktivist groups conduct cyberattacks for ideological or political reasons. Their objectives may include disrupting the operations of specific organizations, exposing perceived injustices, or promoting a particular cause. These groups often target government agencies, corporations, and other entities they view as adversaries.
APT Attack Techniques
Advanced Persistent Threat (APT) attacks employ a range of sophisticated techniques to gain access to a targeted network and remain undetected for an extended period. Some common APT attack techniques include:
- Social Engineering: APT attackers often use social engineering tactics, such as spear-phishing and pretexting, to trick employees into divulging sensitive information or granting access to the network. These highly targeted attacks exploit human psychology to bypass technical defenses.
- Malware: Custom-made malware is a staple in APT attacks. These malicious programs are designed to infiltrate the network, establish a foothold, and maintain a persistent presence. They can be tailored to evade detection by traditional security measures.
- Exploiting Software Vulnerabilities: APT attackers frequently exploit software vulnerabilities to gain access to the network and move laterally within the system. By targeting unpatched or zero-day vulnerabilities, they can bypass security controls and escalate privileges.
- Insider Threats: Sometimes, APT attackers leverage insider threats, such as compromised employees or contractors, to gain access to the network. These insiders may be coerced, bribed, or unwittingly manipulated into assisting the attackers.
- Advanced Threat Intelligence: APT attackers use advanced threat intelligence to gather detailed information about the target network. This intelligence helps them identify vulnerabilities, plan their attack strategies, and remain undetected for as long as possible.
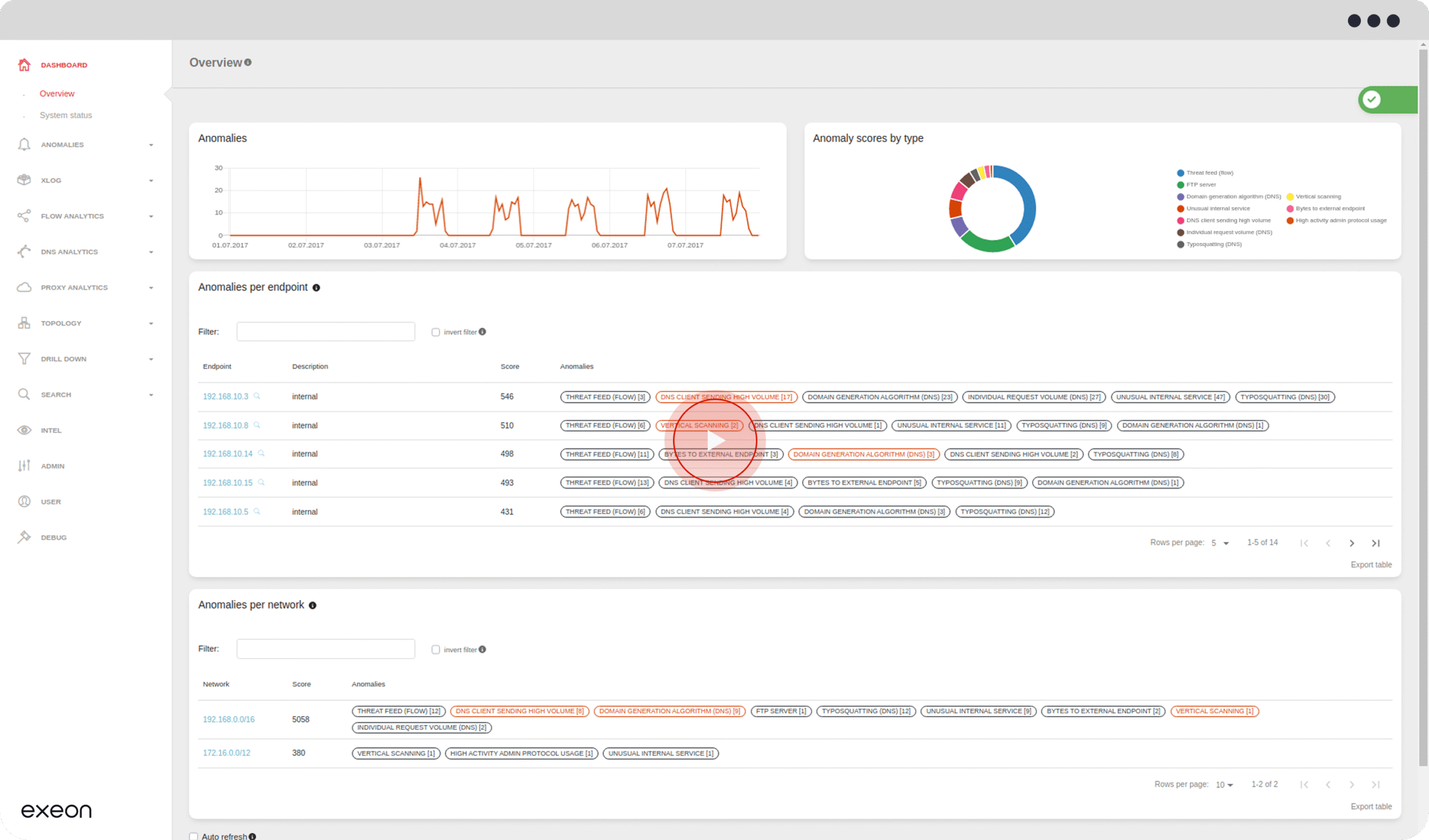
Detecting advanced persistent threats
Watch this demo video to see precisely how Exeon.NDR works to detect advanced threats.
Notable APT Attacks
There have been several notable APT attacks in recent years, each demonstrating the significant impact and sophisticated methods employed by these threat actors. Examples of APT Attacks include:
The Sony Pictures Hack
In 2014, a group of hackers sponsored by the North Korean government conducted a devastating cyberattack against Sony Pictures. The attackers stole sensitive data, including unreleased films and confidential employee information, and released it publicly. The attack caused significant financial and reputational damage to Sony Pictures.
Cybercrime APT Groups
In 2015, a group of hackers sponsored by the Chinese government targeted Anthem, a major health insurance company. The attackers gained access to the personal information of millions of customers, including names, birthdates, and Social Security numbers. The breach highlighted the vulnerability of highly sensitive data in the healthcare sector.
The Equifax Hack
In 2017, a group of hackers sponsored by the Chinese government conducted a cyberattack against Equifax, a leading credit reporting agency. The attackers stole private data from millions of customers, including credit card numbers, Social Security numbers, and personal information. The breach had far-reaching consequences, affecting millions of individuals and prompting widespread scrutiny of data security practices.
By understanding these notable APT attacks, organizations can better appreciate the real-world implications of advanced persistent threats and the importance of robust cybersecurity measures.
Defending against APTs
Strong cybersecurity measures
Employee training
Phishing Awareness
Conducting regular training sessions to educate employees about the dangers of phishing attacks. Employees should be able to recognize phishing emails and avoid clicking on malicious links or downloading suspicious attachments.
Social Engineering Awareness
Teaching employees to be cautious about social engineering attempts, such as pretexting and baiting, which Advanced Persistent Threats actors often use to access sensitive information.
Cybersecurity Best Practices
Encouraging employees to follow cybersecurity best practices, such as strong password management, two-factor authentication (2FA), and secure communication protocols.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are critical security measures used to detect and prevent APT attacks.
These systems work together to provide a comprehensive defense against unauthorized access and malicious activities.
IDS Systems
IDS systems monitor network traffic for signs of unusual or unauthorized activity. They can detect APT attacks by identifying anomalies such as unusual login attempts, unexpected data transfers, or other suspicious behaviors. When potential threats are detected, IDS systems alert security teams, enabling them to investigate and respond promptly.
IPS Systems
IPS systems take a more proactive approach by not only detecting but also blocking malicious traffic. They can prevent APT attacks by intercepting and neutralizing threats before they can gain access to the network. By actively blocking known attack vectors and suspicious activities, IPS systems help to safeguard the network from infiltration.
Combined Defense
When used together, IDS and IPS systems provide a robust security solution. IDS systems offer detailed monitoring and alerting capabilities, while IPS systems deliver real-time threat prevention. This combination enhances the organization’s ability to detect and mitigate APT attacks effectively.
Network Detection and Response (NDR):
As sophisticated APT hackers try to gain access to organizations, proactive cybersecurity measures with machine learning-based NDR and a solid Endpoint Detection and Response (EDR) solution are essential for identifying and mitigating advanced threats and suspicious activities.
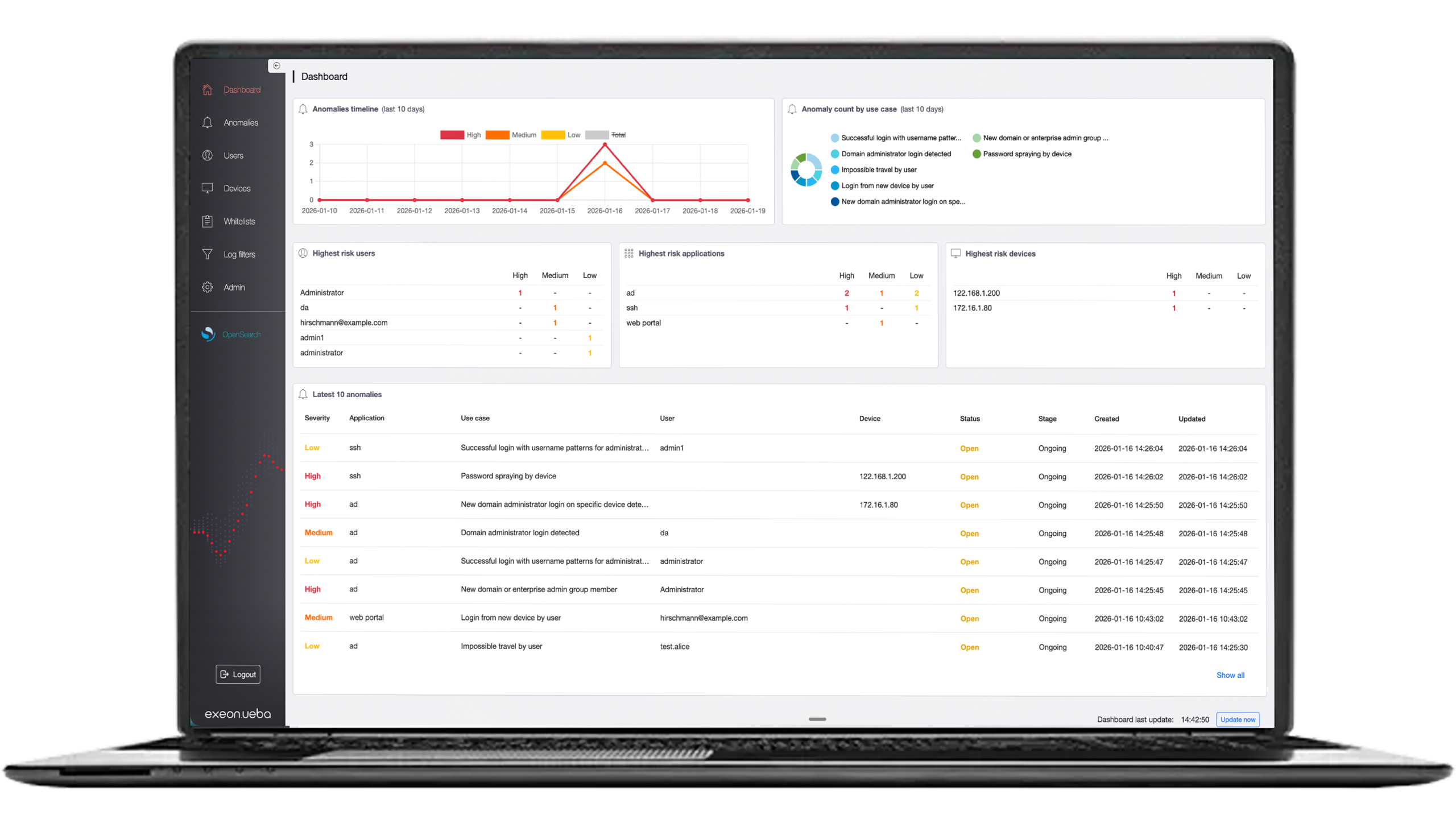
Verifying already corrupted applications and their communication and recognizing machine-learned irregularities is only possible with a machine learning-enabled Network Detection and Response solution like Exeon.NDR: it monitors the data traffic in the network using AI and machine learning and recognizes anomalies based on models of normal and inconspicuous network traffic.
In looking for proactive and dynamic cybersecurity defense that significantly enhances their ability to detect and mitigate threats effectively, machine learning algorithms should be in the driver’s seat for the detection of advanced threats and suspicious patterns.
While automation can help in rapidly responding to identified threats, minimizing the dwelling time of attackers, ML models can stay continuously updated with evolving threats and attack techniques and regularly retrained to stay relevant.
Network monitoring
Continuous Surveillance: Employing network monitoring tools and Security Information and Event Management (SIEM) systems to continuously monitor network traffic for unusual patterns or anomalies, especially those that may indicate an APT that remains undetected. Real-time alerts can help security teams respond promptly to potential APT activities.
Behavioral Analysis: Implementing behavioral analysis to identify deviations from normal network behavior. Advanced Persistent Threats often try to blend in with legitimate traffic, making behavioral analysis a valuable detection method.
Other main protection measures against APTs include patch management, threat intelligence, and incident response.
For a guide on how to proactively detect and respond to APTs, download our 24-page guide below!
Strengthen cyber resilience through
AI-driven APT detection
This comprehensive 24-page guide covers the current threat landscape, key security challenges, improved threat detection strategies, the role of NDR and AI, and best practices.
Insights from our security experts
Cut through the cyber noise: blogs written by our thought leaders in AI-powered cybersecurity.