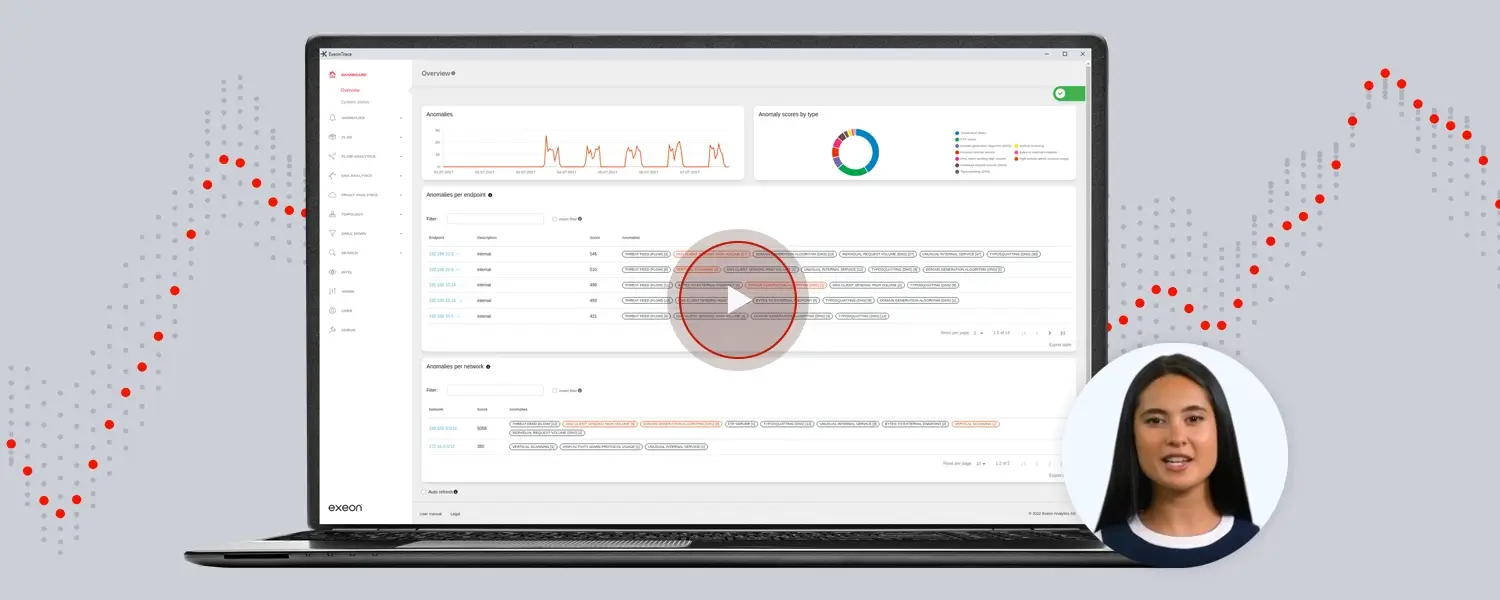
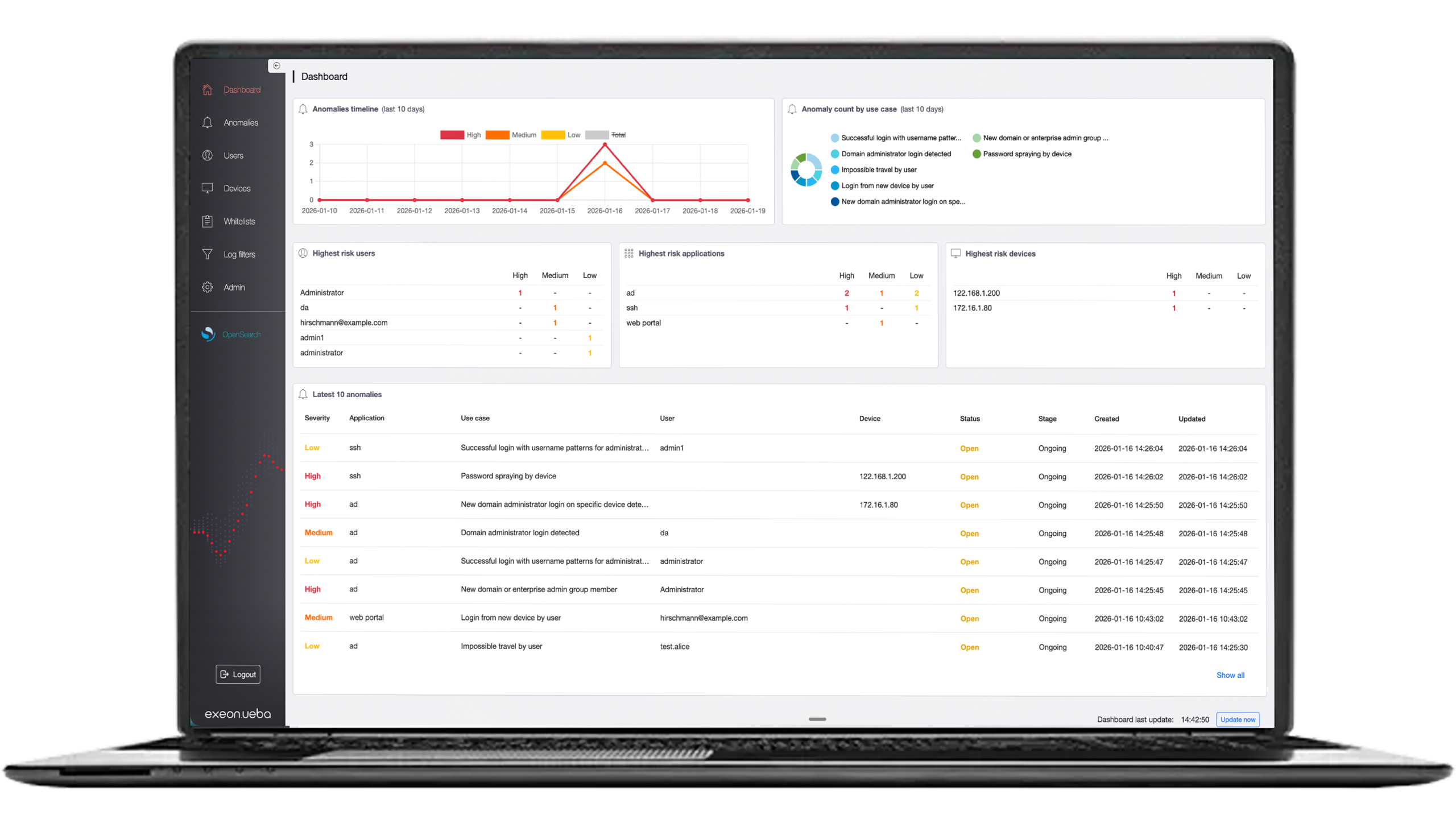
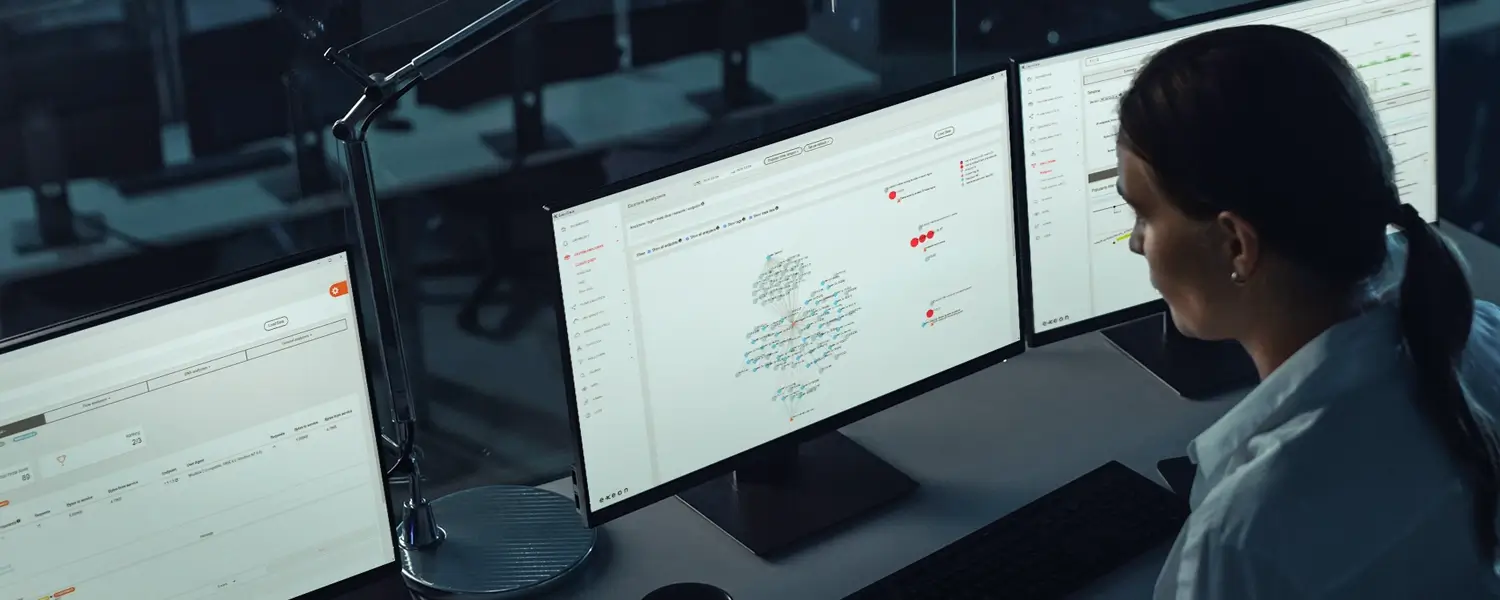
See the threats your SIEM and EDR miss—AI-powered NDR & UEBA from Exeon.
300% ROI
Through efficient threat detection and reduced response times with AI (Forrester®)
50% Faster
Incident response through AI automation (Gartner®)
70% Reduction
In false alarms with precise, machine learning-based detection (Gartner®)

















Four Pillars of
Modern Cybersecurity
A unified framework of four core elements that protect systems, data, and digital operations from evolving threats.
01
Advanced Technology & Threat Detection
03
Operational Efficiency & Cost Savings
Global proven Excellence
Our advanced security products have been awarded and recognized worldwide for their innovative and future-proof capabilities.

Some of the many industries Exeon thrives in

Finance
From regulatory requirements to on-prem and air-gapped deployment and 100% data privacy.
Manufacturing & industrial
Sensorless detection across IT/IIoT converged environments — including legacy applications and OT devices — ensuring continuous monitoring with zero downtime operations.
Logistics & transportation
Secure and compliant logistics & transportation operations with seamless global deployment for highly distributed infrastructure.
Public sector
Empowering government organizations with the protection of highly sensitive data, using metadata insights for robust oversight, flexibility and privacy compliance.
Healthcare
Sensorless protection, deployed flexibly on prem or in the cloud, upholds clinic & patient data privacy for compliance and precise threat detection across even non agentable medical devices.
Some of the many industries Exeon thrives in
Real-world success stories
Here’s how we provide our unique AI-powered technology to support security teams and managed security service providers in safeguarding corporate and personal data, operations, and reputation.

CISO, SWISS International Airlines
“As the Swiss national airline, we are driven by a passion for exceptional performance, in the spirit of our guiding principles. A stable and secure IT is the most important basis for an excellent customer service. For the security of SWISS IT, we use Exeon as a central cybersecurity tool, fully managed by our long-term partner Reist Telecom AG. A perfect combination and solution to monitor our network and quickly detect any kind of anomalies.”

Head IT Security, PostFinance AG
“PostFinance has chosen Exeon.NDR because of its open and future-proof architecture. Not needing any hardware sensors and being able to control data flows, we didn’t have to make any significant changes to our existing infrastructure. We are also convinced by the cooperation with the competent and technically outstanding Exeon team.”

CEO & Founder, Planzer
“As CEO and owner of a fast moving, international logistics company, I cannot afford any system interruptions due to cyber incidents. With Exeon.NDR, we have found a Swiss solution to monitor our network and quickly detect cyber threats.”

ICT Project Leader, WinGD
“Exeon provides us with complete visibility of our network data flows and automatically detects suspicious behavior. Thanks to their AI algorithms, we immediately identify potential cyber threats and can respond quickly and efficiently. This way, we prevent attackers from moving undetected in our systems, infiltrating the infrastructure, or bypassing existing security measures.”

Director of Cybersecurity Research, KuppingerCole
“The management and analyst interfaces are intuitive and can yield important insights for customers. Exeon’s approach to data retention helps customers keep data local for regulatory compliance and reduces costs for long-term storage by only retaining event metadata. The solution supports the most pertinent standards for exchanging threat information.”

Network & Security Engineer, Solothurner Spitäler
“Exeon is our cybersecurity alarm system, alerting us to any network anomalies. What also really convinced us is the platform’s intuitive interface—it has become a tool to reliably monitor and secure our data and network.”
How it works
An overview of the Exeon customer journey to elevated cybersecurity.
01Get in touch
View Exeon threat detection videos or schedule a demo to speak with our security experts to explore Exeon's security analytics products. Meet with us to solidify an implementation plan for our solution, where we transparently discuss pricing, deployment, and timelines to match your requirements with our capabilities.
02Straightforward installation
Deploy Exeon as a virtual machine in minutes and connect to your existing data sources without installing agents or changing your infrastructure. Instantly gain complete, real-time visibility into all traffic flows, identity interactions across your IT and OT environments without impacting ongoing operations.
03Eye-opening analysis
By making all devices and communications and identity interactions, Exeon enables you to understand what is really happening on your infrastructure. Eliminate blind spots, discover legacy assets/protocols/identities, identify unusual behavior, reduce false positives and focus on the threats that matter.
04Immediate & ongoing protection
Our supervised algorithms protect you from all known and unknown threats and scenarios from day one. After a few days, the unsupervised algorithms quickly learn your system—just a short period of automated learning is enough to recognize corporate patterns, and their efficiency continues to grow. Once the unsupervised algorithms are fully trained, Exeon further improves its detection by uncovering anomalies and unusual behaviors that would otherwise go unnoticed.
Experience Exeon
Committed to data sovereignty and confidentiality, we ensure top compliance, empowering security teams to navigate any challenge with confidence. Are you ready?
NDR market comparison
Exeon eliminates the need for deep packet inspection (DPI) with metadata driven analysis, providing continuous visibility across on prem, virtual, and cloud networks — completely non invasive, without agents and without hardware appliances.
Capabilities
Lightweight, efficient data analysis without traffic mirroring or sensors
Security analytics unaffected by encryption
Superior network visibility, not restricted to core switch traffic only
Powerful Machine Learning algorithms
Fully on-prem data processing
Exeon
Vectra
Darktrace
ExtraHop
Exeon in action
Learn how our next-gen analytics empower teams with precision, speed, and efficiency.

Guided threat detection tour

NIS2, DORA & KRITIS Guide

DORA Compliance Checklist

NIS2 Manufacturing Use Case

AI against advanced threats

Public Sector Use Case
Insights from our security experts
Cut through the cyber noise: blogs written by our thought leaders in AI-powered cybersecurity.
Book a short, hassle-free demo.
Schedule a demo today and discover how advanced security analytics improves cyber resilience and Swiss excellence.