Bekämpfung von Insider-Bedrohungen mit KI-gestützter Erkennung
Exeon erkennt, bewertet und korreliert auffälliges Benutzerverhalten in dem Moment, in dem es auftritt, und verschafft so Sicherheitsteams die Sichtbarkeit und Schnelligkeit, die herkömmlichen Tools fehlt.
Einschränkungen herkömmlicher Cybersicherheitsmaßnahmen
der Unternehmen fühlen sich auf die Erkennung von und die Reaktion auf Insider-Bedrohungen vorbereitet.
der Insider-Angriffe bleiben mehr als zwei Jahre lang unentdeckt, bevor sie entdeckt werden.
der Insider-Bedrohungen gehen von fahrlässigen Mitarbeitern oder Auftragnehmern aus, während nur 23 % in böser Absicht erfolgen.
Aktuelle Probleme im Zusammenhang mit dem Schutz vor Insider-Bedrohungen unterstreichen die dringende Notwendigkeit fortschrittlicher NDR-Lösungen, die eine Echtzeitüberwachung und schnelle Erkennung von Bedrohungen in hybriden Umgebungen ermöglichen.
Fragmentierte Sichtbarkeit in hybriden Umgebungen
Mit den Fortschritten bei Zero Trust-Architekturen melden sich immer mehr Mitarbeiter, Auftragnehmer und Lieferanten von potenziell nicht vertrauenswürdigen Standorten aus an. Ohne konsolidierte/vollständige Sichtbarkeit von On-Premise-, SaaS- und OT-Datenverkehr bleibt riskantes Verhalten unbemerkt.
Missbrauch von Zugangsdaten und böswillige Insider
Kompromittierte Anmeldedaten, missbräuchlich verwendete Zugriffstoken und die Ausweitung von Berechtigungen ermöglichen es Angreifern oder Insidern, unter vertrauenswürdigen Identitäten zu operieren und herkömmliche Kontrollen zu umgehen.
Verzögerte Entdeckung einer verdeckten Datenexfiltration
Große, aber verdeckte Dateiübertragungen und Cloud-Synchronisationen nutzen oft verschlüsselte Kanäle, die von herkömmlichen DLP-Suites nicht überprüft werden können. Das macht es schwer, zu reagieren, bevor kritische Daten durchsickern und möglicherweise veröffentlicht werden.
Wie Exeon Insider-Bedrohungen bekämpft
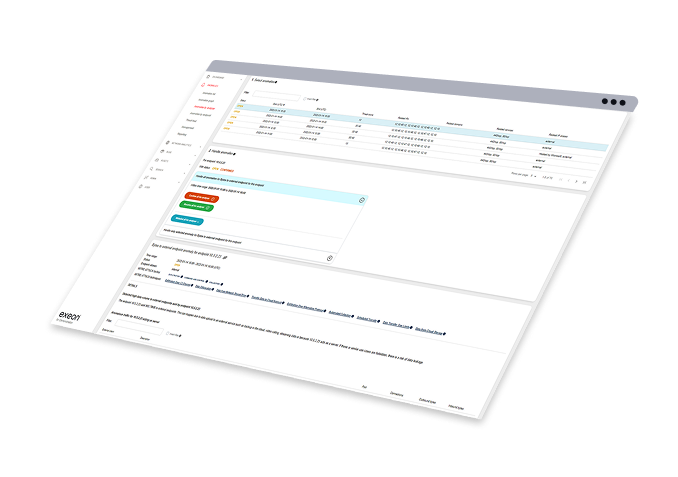
Ganzheitliche Sichtbarkeit
Bereitstellung von Kontext für Anomalien
Erkennung in Echtzeit
Zuverlässige Alerts und Reporting
Globale Unternehmen und kritische Infrastrukturen bauen auf unsere Sicherheit
















Strategie zum Management interner Bedrohungen
Einsetzen und integrieren
- Implementieren Sie Exeon.NDR für eine umfassende Netzwerküberwachung (Nord-Süd- und Ost-West-Datenverkehr).
- Setzen Sie Exeon.UEBA ein, um die Echtzeitüberwachung des Benutzer- und Geräteverhaltens zu ermöglichen.
- Nahtlose Integration mit SIEM, SOAR und EDR für einen einheitlichen Sicherheitsansatz.
- Validieren Sie Zero Trust und andere Sicherheitsrichtlinien, um sicherzustellen, dass der eingeschränkte Zugang durchgesetzt wird.
Überwachung und Festlegung von Referenzwerten
- Kontinuierliche Erfassung und Analyse des Netzwerkverkehrs und der Benutzeraktivitäten.
- Nutzen Sie KI-gesteuerte Analysen, um Referenzwerten für regelmässiges Nutzerverhalten festzulegen.
- Nutzen Sie den Exeon-Ansatz, um Sicherheit, Datenschutz und Vertraulichkeit in einem zu erreichen.
Erkennen und Analysieren von Bedrohungen
- Identifizieren Sie Anomalien im Netzwerk- und Benutzerverhalten, die auf potenzielle Insider-Bedrohungen hinweisen.
- Nutzen Sie maschinelles Lernen und KI-gestützte Erkennung, um subtile bösartige Aktivitäten zu erkennen.
- Klassifizierung und Priorisierung von Risiken durch verhaltensbasiertes Scoring von Anomalien.
Automatisieren Sie Reaktion und Schadensbegrenzung
- Lösen Sie kontextbezogene Echtzeitwarnungen für integrierte Reaktionswerkzeuge aus.
- Nahtlose Verbindung mit SOAR, SIEM und Firewalls für automatisierte Maßnahmen.
- Erkennung und Eskalation von Datenexfiltration, lateraler Bewegung und Kompromittierung von Konten.
- Lassen Sie Ihren vorhandenen Stack den Zugriff beschränken oder Bedrohungen sofort isolieren.
Kontinuierliche Verbesserung und Datensouveränität
- Abstimmung und Verfeinerung der Modelle zur Anpassung an eine sich entwickelnde Bedrohungslandschaft.
- Definieren und schreiben Sie Ihre eigenen Analyzer oder bereiten Sie sich auf zukünftige Erweiterungen in der anwendungszentrierten Sicherheitsanalyse vor.
- Behalten Sie die Kontrolle über Ihre Daten mit vollständig lokaler Verarbeitung und Berichterstattung.
Exeon.NDR in Aktion
KI-gestützte Anomalieerkennung, die ungewöhnliche Verhaltensweisen und Zugriffsmuster erkennt, bevor sie eskalieren – lesen Sie die Anwendungsfälle, um mehr über unsere Technologie zu erfahren.

Wie KI bei der Bedrohungsanalyse hilft

Geführte Bedrohungserkennungstour

NIS2, DORA & KRITIS Leitfaden

KI gegen fortgeschrittene Bedrohungen
Was unsere Kunden sagen

Regional Practice Head, Wipro
"Exeon ist die ideale Lösung für den Übergang von einem Legacy-SOC zu einem Next-Generation-SOC. Sie verbessert die Erkennungsmöglichkeiten, minimiert das Alarmrauschen und reduziert die Kosten erheblich."

Netzwerk- und Sicherheitsingenieur, Solothurner Spitäler
"Exeon ist unser Cybersicherheits-Alarmsystem, das uns bei Netzwerkanomalien alarmiert. Die intuitive Benutzeroberfläche der Plattform hat uns überzeugt – ein Werkzeug, das unsere Daten und unser Netzwerk zuverlässig überwacht und sichert."

ICT-Projektleiter, WinGD
"Exeon bietet uns einen vollständigen Einblick in unsere Netzwerkdatenströme und erkennt automatisch verdächtiges Verhalten. Dank der KI-Algorithmen erkennen wir potenzielle Cyber-Bedrohungen sofort und können schnell und effizient reagieren. So verhindern wir, dass sich Angreifer unbemerkt in unseren Systemen bewegen, in die Infrastruktur eindringen oder bestehende Sicherheitsmassnahmen umgehen."

CISO, SWISS International Airlines
"Als Schweizer Nationalairline treibt uns die Leidenschaft für aussergewöhnliche Leistungen im Sinne unserer Leitsätze an. Eine stabile und sichere IT ist die wichtigste Grundlage für einen exzellenten Kundenservice. Für die Sicherheit der SWISS IT setzen wir Exeon als zentrales Cybersecurity-Tool ein, das vollständig von unserem langjährigen Partner Reist Telecom AG verwaltet wird. Eine perfekte Kombination und Lösung, um unser Netzwerk zu überwachen und Anomalien schnell zu erkennen."

Direktor der Cybersicherheitsforschung, KuppingerCole
"Die Management- und Analystenschnittstellen sind intuitiv und können den Kunden wichtige Erkenntnisse liefern. Der Ansatz von Exeon zur Datenaufbewahrung hilft den Kunden, die Daten zur Einhaltung gesetzlicher Vorschriften lokal zu halten und die Kosten für die langfristige Speicherung zu reduzieren, indem nur die Ereignis-Metadaten aufbewahrt werden. Die Lösung unterstützt die wichtigsten Standards für den Austausch von Bedrohungsinformationen."
Weitere Lösungen

Alarmierung und Reporting
- Kontinuierliche Analyse des Netzwerkverkehrs.
- KI und ML zur Minimierung von Fehlalarmen und Ermüdungserscheinungen.
- Zukunftssichere Analysetechnologie mit einer intuitiven Benutzeroberfläche.

Echtzeit-Erkennung von Bedrohungen und Verhaltensanomalien
Die KI-gestützte Echtzeiterkennung von Exeon identifiziert fortschrittliche Bedrohungen sofort und reduziert Risiken nachhaltig.
- Fluss- und protokollbasierte Erkennung mit überwachten, unüberwachten und statistischen ML-Modellen.
- Automatische Ereignis-Kennzeichnung und Risikobewertung zur Unterstützung der Analysten.
- Modelle lassen sich durch Analysten-Feedback und Tuning gezielt verfeinern.

Skalierbarkeit
Modularer, flexibler Ansatz, einfache Skalierung: Die verteilte Architektur von Exeon skaliert dynamisch mit dem Datenverkehrsvolumen und dem Wachstum der Infrastruktur.
- Keine Ausfallzeiten, unterbrechungsfreier Betrieb auch in Spitzenzeiten oder bei hoher Nachfrage.
- Es sind keine manuellen Eingriffe erforderlich.
- In Echtzeit angepasste Server- und Ressourcenzuweisungen.

Integration
- Einfache Bedienung und intuitive Navigation.
- Effiziente Alarmierung und risikobasierte Priorisierung.
- Native Kompatibilität mit Cloud-Plattformen und vieles mehr.
Branchenorientierte use cases

Öffentliche Sicherheit, Schutz privater Daten
Robuste und präzise Überwachung und Sicherheit für kritische Infrastrukturen und vertrauliche Behördendaten.

Sichere Patientendaten und Compliance
Schutz sensibler Patientendaten und Einhaltung von Vorschriften (HIPAA usw.) durch Erkennung anomalen Verhaltens von Benutzern und Geräten.

Anwendungen im Finanzsektor
Exeon überwacht Transaktionen und Benutzerverhalten in Echtzeit, um verdächtige Aktivitäten zu erkennen, Insider-Bedrohungen zu verhindern und vieles mehr.

Für die industrielle Welt gemacht
Umfassende OT- und IT-Überwachung zur Sicherung von Produktionsanlagen und Maschinensteuerungen, Erkennung von Anomalien und mehr.

Zero Trust im Finanzsektor
Unterstützen Sie die Einhaltung von DORA und beseitigen Sie gleichzeitig das inhärente Vertrauen in Netzwerke, indem Sie eine kontinuierliche Identitätsüberprüfung erzwingen, den Zugang zu kritischen Anlagen beschränken und vieles mehr.
Häufig gestellte Fragen
Exeon revolutioniert das Management von Insider-Bedrohungen mit KI-gesteuerter Erkennung, Echtzeit-Verhaltensanalysen und Zero-Trust-Sicherheit und stellt sicher, dass Unternehmen Risiken von innen heraus schnell erkennen und abmildern können. Durch die nahtlose Integration in hybride und Multi-Cloud-Umgebungen bietet Exeon unvergleichliche Transparenz, automatisierte Reaktion und skalierbaren Schutz vor von Insidern verursachten Datenverletzungen.
Was sind Insider-Bedrohungen und warum sind sie ein erhebliches Risiko?
Insider-Bedrohungen sind Sicherheitsrisiken, die von Einzelpersonen innerhalb einer Organisation ausgehen, z. B. von Mitarbeitern oder Auftragnehmern. Dabei kann es sich um böswillige Handlungen oder unbeabsichtigte Fehler handeln. Insider-Bedrohungen sind für 60 % der Datenschutzverletzungen verantwortlich und können zu erheblichen finanziellen und rufschädigenden Schäden führen. Die Erkennung und Eindämmung dieser Bedrohungen ist besonders schwierig, vor allem in Cloud- und Hybrid-Umgebungen.
Was ist heute die größte Gefahr für Unternehmen in Bezug auf Insider-Bedrohungen?
Eine der größten Gefahren von Insider-Bedrohungen ist die zunehmende Raffinesse von Insider-Angriffen, insbesondere bei KI-gestützten Bedrohungen und Datenexfiltrationstechniken. Zu den Hauptrisiken gehören Datendiebstahl und Spionage, KI-gestützte Insider-Bedrohungen, kompromittierte Zugangsdaten, Cloud-Sicherheitsrisiken, finanzielle und betriebliche Schäden und sogar die Beteiligung von Nationalstaaten und organisierter Kriminalität. Unternehmen müssen Verhaltensanalysen, Zero-Trust-Sicherheit und strenge Zugangskontrollen implementieren, um Insider-Bedrohungen wirksam zu entschärfen.
Wie unterstützt Exeon hybride und Multi-Cloud-Umgebungen?
Wie nutzt Exeon KI für das Management von Insider-Bedrohungen?
Exeon nutzt KI und maschinelles Lernen, um Verhaltens-Baselines für Benutzer und Geräte zu erstellen, Anomalien im Netzwerk- und Benutzerverhalten zu erkennen, Abweichungen von normalen Aktivitäten zu markieren und potenzielle Risiken hervorzuheben sowie den Erkennungs- und Reaktionsprozess zu automatisieren, um die Sicherheit zu verbessern und den manuellen Aufwand zu reduzieren.
Benötigt Exeon Endpunkt-Agenten für die Bereitstellung?
Nein, Exeon arbeitet in einem agentenlosen Modus, wodurch es skalierbar und einfacher in großen, verteilten Umgebungen ohne die Notwendigkeit von Endpunkt-Agenten einzusetzen ist. Weitere Details zu spezifischen, einfachen und schnellen Bereitstellungen finden Sie hier.
Verhindern Sie Insider-Bedrohungen, bevor sie zuschlagen.
Erfahren Sie, wie die KI-gestützten Produkte von Exeon Insider-Bedrohungen in Echtzeit erkennen und Datenverstöße verhindern, bevor sie auftreten. Sprechen Sie noch heute mit uns.
