KI-gestützte Applikationssicherheit
Applikationen unter Beschuss
der Sicherheitsvorfälle beinhalten Angriffe auf Anwendungen, die oft durch das Verwenden von gestohlenen Anmeldeinformationen von anderen Online-Dienstens, API-Missbrauch und Fehlkonfigurationen erfolgen.
der Sicherheitsvorfälle haben ihren Ursprung in anfälligen Anwendungen und sind ein Haupteinfallstor für Ransomware, Malware-Injection und Angriffe zur Ausweitung von Berechtigungen.
der Unternehmensanwendungen weisen kritische Sicherheitslücken auf, darunter unsichere Authentifizierung, API-Fehlkonfigurationen und ungepatchte Software, was die Anwendungen zu leichten Zielen macht.
Aus diesem Grund darf die Sicherheit auf der Anwendungsebene nicht auf die lange Bank geschoben werden. Angreifer haben es immer noch zuerst auf die Web- und SaaS-Eingangstüren abgesehen. Fortlaufende Analysen sind die einzige Möglichkeit, diese Einstiegspunkte zu erkennen und zu schliessen, bevor sie Ihre Daten exponieren.
Erkennung von Bedrohungen in Echtzeit
Stoppt Bedrohungen, bevor sie zu Ausfällen oder Sicherheitsverletzungen eskalieren.
Datenschutzgerechte Sicherheit
Wir sorgen dafür, dass Unternehmen die GDPR-, HIPAA- und andere Datenschutzvorschriften einhalten, damit ihre Daten die Unternehmensgrenzen nicht verlassen.
Umsetzbare Erkenntnisse & Widerstandsfähigkeit
Die Reaktionszeit wird verkürzt, Fehlalarme werden reduziert und die langfristige Widerstandsfähigkeit von Anwendungen wird erhöht.
Warum Exeon für die Überwachung der Applikationssicherheit wählen?
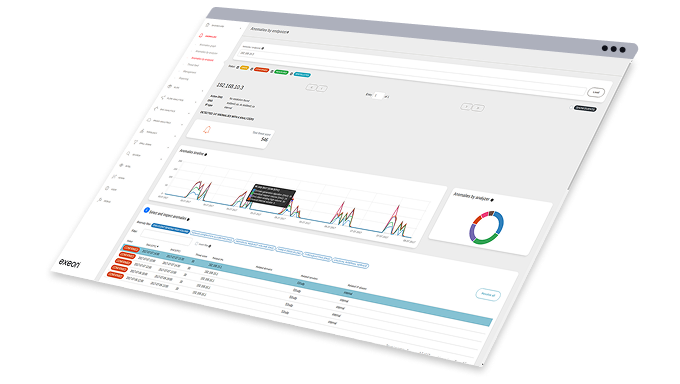
Erkennung von Anomalien in Echtzeit
Umfassende Sichtbarkeit
Hohe Leistung
Privatsphäre im Mittelpunkt
Stärkung der Sicherheitsteams weltweit
















Unsere Überwachung der Applikationssicherheit
Telemetrie sammeln
Exeon nimmt Protokolle und Datenströme von Applikationen, APIs und dem umgebenden Netzwerk auf - von kundenspezifisch programmierter bis hin zu kommerzieller Software und APIs. All dies geschieht, ohne dass Sie die Leitungen von Installationsagenten anzapfen müssen.
KI-gestützte Analyse
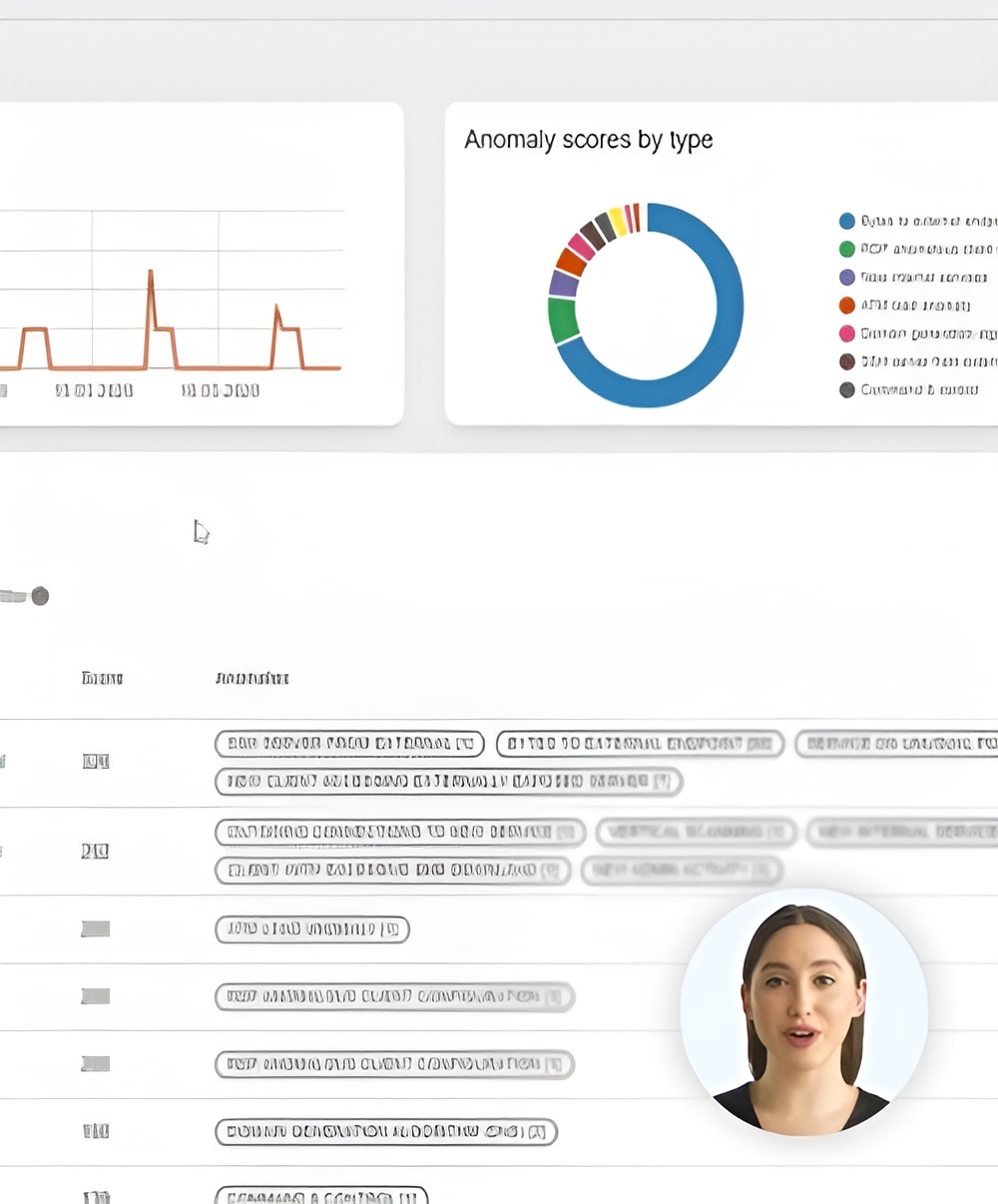
Modelle für maschinelles Lernen durchsuchen den Datenstrom in Echtzeit und erkennen Anomalien, die auf Kontomissbrauch, API-Missbrauch oder Versuche der Datenexfiltration hindeuten.
Sofortige Warnungen
Risikobewertete Benachrichtigungen erreichen Ihren SIEM/SOAR-Stack in Sekundenschnelle, so dass die zuständigen Mitarbeiter handeln können, bevor die Benutzer die Auswirkungen spüren.
Umsetzbare Erkenntnisse
Zu jedem Vorfall gibt es einen Ursachenkontext und empfohlene Abhilfemaßnahmen - Zuordnung zu MITRE ATT&CK, Optimierung von Richtlinien oder automatische Playbook-Links.
Exeon in Aktion

Ihre DORA-Checkliste

PostFinance Use Case

DORA, NIS2 & KRITIS Leitfaden

DORA Use Case

APTs erkennen: Finanz-Edition
Überwachung von Geldautomaten
Warum sich unsere Kunden für Exeon.NDR entscheiden

CISO, SWISS International Airlines
"Als Schweizer Nationalairline treibt uns die Leidenschaft für aussergewöhnliche Leistungen im Sinne unserer Leitsätze an. Eine stabile und sichere IT ist die wichtigste Grundlage für einen exzellenten Kundenservice. Für die Sicherheit der SWISS IT setzen wir Exeon als zentrales Cybersecurity-Tool ein, das vollständig von unserem langjährigen Partner Reist Telecom AG verwaltet wird. Eine perfekte Kombination und Lösung, um unser Netzwerk zu überwachen und Anomalien schnell zu erkennen."

Leiter IT-Sicherheit, PostFinance AG
"PostFinance hat sich wegen der offenen und zukunftsfähigen Architektur für Exeon.NDR entschieden. Dank der Möglichkeit, auf Hardware Sensoren zu verzichten und der Kontrolle über die Datenflüsse musste PostFinance keine grossen Änderungen an der bestehenden Infrastruktur vornehmen. Die Zusammenarbeit mit den kompetenten, technisch hochstehenden Exeon Mitarbeitenden hat überzeugt."

CEO & Gründer, Planzer
"Als CEO und Inhaber einer eng getakteten Logistikfirma kann ich mir Systemausfälle wegen Cybervorfällen nicht leisten. Mit Exeon.NDR haben wir bei Planzer eine Schweizer Lösung gefunden, um unser Netzwerk zu überwachen und Cyberbedrohungen frühzeitig zu erkennen."

Leiter Infrastruktur & Anwendungen, 3 Banken IT
"Wir schätzen vor allem die umfassende Netzwerktransparenz, die uns Exeon.NDR bietet.
Die Anomalieerkennung ist zudem äußerst präzise und ermöglicht es unseren Analysten, sich auf die wesentlichen Bedrohungen zu konzentrieren."

Direktor der Cybersicherheitsforschung, KuppingerCole
"Die Management- und Analystenschnittstellen sind intuitiv und können den Kunden wichtige Erkenntnisse liefern. Der Ansatz von Exeon zur Datenaufbewahrung hilft den Kunden, die Daten zur Einhaltung gesetzlicher Vorschriften lokal zu halten und die Kosten für die langfristige Speicherung zu reduzieren, indem nur die Ereignis-Metadaten aufbewahrt werden. Die Lösung unterstützt die wichtigsten Standards für den Austausch von Bedrohungsinformationen."

Netzwerk- und Sicherheitsingenieur, Solothurner Spitäler
"Exeon ist unser Cybersicherheits-Alarmsystem, das uns bei Netzwerkanomalien alarmiert. Die intuitive Benutzeroberfläche der Plattform hat uns überzeugt – ein Werkzeug, das unsere Daten und unser Netzwerk zuverlässig überwacht und sichert."

ICT-Projektleiter, WinGD
"Exeon bietet uns einen vollständigen Einblick in unsere Netzwerkdatenströme und erkennt automatisch verdächtiges Verhalten. Dank der KI-Algorithmen erkennen wir potenzielle Cyber-Bedrohungen sofort und können schnell und effizient reagieren. So verhindern wir, dass sich Angreifer unbemerkt in unseren Systemen bewegen, in die Infrastruktur eindringen oder bestehende Sicherheitsmassnahmen umgehen."

Senior Produkt Portfolio Manager Cyber Defense, Swisscom
"Exeon bietet zahlreiche funktionale Vorteile gegenüber konkurrierenden NDR-Produkten. Mit Exeon sind wir in der Lage, innovative Technologien und fortschrittliche Analysen zu nutzen, um unseren Kunden eine erstklassige Sicherheitslösung zu bieten. Gemeinsam sind wir bestrebt, die Sicherheitslandschaft zu verbessern."

Regional Practice Head, Wipro
"Exeon ist die ideale Lösung für den Übergang von einem Legacy-SOC zu einem Next-Generation-SOC. Sie verbessert die Erkennungsmöglichkeiten, minimiert das Alarmrauschen und reduziert die Kosten erheblich."

CEO, REAL Security
"Als führender Distributor sind wir immer auf der Suche nach zuverlässigen, innovativen und leistungsstarken Lösungen, um unser Portfolio zu stärken und die Zukunft der Cybersicherheit zu gestalten. Exeon hat immer wieder bewiesen, dass sie ein vertrauenswürdiger Partner sind, mit dem man leicht zusammenarbeiten kann. Ihre Lösung exeon.ndr hat bereits in verschiedenen Bereichen große Wirkung gezeigt."
Weitere Lösungen

Management von Insider-Bedrohungen
- Umfassende Überwachung des gesamten Netzwerks und Transparenz der Anwendungen.
- Zero Trust-Integration zur Durchsetzung strenger Zugangskontrollen.
- Einblicke in die Sicherheit in Echtzeit über Live-Dashboards.

Skalierbarkeit
Modularer, flexibler Ansatz - Skalierung leicht gemacht: Die verteilte Architektur von Exeon skaliert dynamisch mit dem Verkehrsaufkommen und dem Wachstum der Infrastruktur.
- Keine Ausfallzeiten, unterbrechungsfreier Betrieb auch in Spitzenzeiten oder bei hoher Nachfrage.
- Es sind keine manuellen Eingriffe erforderlich.
- In Echtzeit angepasste Server- und Ressourcenzuweisungen.

Alarmierung und Reporting
Ein innovatives, risikobasiertes Warnsystem, mit dem Sie sich auf kritische Sicherheitsvorfälle konzentrieren können, eliminiert Rauschen und verbessert die betriebliche Effizienz.
- Kontinuierliche Analyse des Netzwerkverkehrs.
- KI und ML zur Minimierung von Fehlalarmen und Ermüdungserscheinungen.
- Zukunftssichere Analysetechnologie mit einer intuitiven Benutzeroberfläche.

Compliance & Cybersicherheit
Mit dem Datenschutz-First-Ansatz von Exeon und der Möglichkeit zur Self-Hosted-Installation wird die Einhaltung komplexer Vorschriften deutlich vereinfacht – ob On-Premises, in der Cloud oder in sensiblen, abgeschotteten Netzwerken (Air-Gapped).
- Verbessert die Compliance durch vollständige Netzwerktransparenz, Erkennung von Anomalien und den für die Berichterstattung und Integration in SOAR-Playbooks erforderlichen Kontext.
- 100%ige Netzwerktransparenz und frühzeitige Erkennung fortschrittlicher Bedrohungen.
- Gewährleistet die Einhaltung von NIS2, ISO 27001, GDPR und mehr.
Use Cases für Branchen

Anwendungen im Finanzsektor
Exeon überwacht Transaktionen und Benutzerverhalten in Echtzeit, um verdächtige Aktivitäten zu erkennen, Insider-Bedrohungen zu verhindern und vieles mehr.

Für die industrielle Welt gemacht
Umfassende OT- und IT-Überwachung zur Sicherung von Produktionsanlagen und Maschinensteuerungen, Erkennung von Anomalien und mehr.

Sichere Patientendaten und Compliance
Schutz sensibler Patientendaten und Einhaltung von Vorschriften (HIPAA usw.) durch Erkennung anomalen Verhaltens von Benutzern und Geräten.

Öffentliche Sicherheit, Schutz privater Daten
Robuste und präzise Überwachung und Sicherheit für kritische Infrastrukturen und vertrauliche Behördendaten.
FAQs: Alles, was Sie wissen müssen
Die Applikationssicherheitsüberwachung von Exeon schützt Geschäftsanwendungen mit Echtzeittransparenz, fortschrittlicher Bedrohungserkennung und datenschutzgerechter Sicherheit. Durch die Analyse des Benutzerverhaltens und die Verarbeitung anwendungsspezifischer Protokolle werden Anomalien erkannt und Bedrohungen verhindert, bevor sie eskalieren. Durch kontinuierliche Überwachung und fortschrittliche Analysen erhöht Exeon die Widerstandsfähigkeit der Cybersicherheit und gewährleistet die betriebliche Integrität.
Wie gewährleistet Exeon den Datenschutz bei gleichzeitiger Überwachung der Sicherheit?
Wie schützt die KI-gestützte Applikationssicherheitsüberwachung von Exeon kritische Applikationen und verhindert Bedrohungen?
Wie funktioniert die KI-gestützte Sicherheitsüberwachung von Exeon?
Was sind die wichtigsten Vorteile des Einsatzes von Exeon für die Applikationssicherheit?
- Proaktive Risikominderung - Erkennt Bedrohungen, bevor sie eskalieren.
- Verbessertes Sicherheitsverhalten - Bietet einen tiefen Einblick in Bedrohungen auf der Anwendungsebene.
- Einhaltung gesetzlicher Vorschriften - Hilft Unternehmen bei der Einhaltung von GDPR-, HIPAA-, PCI DSS- und DORA-Standards.
- Geringere Ermüdung durch Alarme - KI priorisiert echte Bedrohungen und minimiert Fehlalarme.
- Skalierbarkeit und Integration - Unterstützt hohe Ereignismengen und lässt sich mit SIEM-, SOAR- und Cloud-Sicherheitstools integrieren.
Welche Arten von Umgebungen werden von Exeon geschützt?
Exeon schützt kritische Anwendungen, SaaS-Umgebungen, Cloud-native Anwendungen und Microservices-Architekturen und unterstützt Zero Trust-Sicherheitsmodelle durch kontinuierliche Überwachung.
Sprechen Sie mit einem Experten, sichern Sie Ihre Anwendungen.
Sprechen Sie mit unseren Sicherheitsexperten, um zu erfahren, wie die Echtzeit-Bedrohungserkennung von Exeon Ihre Anwendungen vor komplexen Cyber-Risiken schützen kann.
