The Akira ransomware group quickly gained notoriety. The group emerged in March 2023 and is already the fourth most active group worldwide. If they keep up with this speed, they will be surpassing Lockbit soon, demanding millions in ransom from its victims.
Akira mainly targets companies in various industries, including public, finance, real estate, manufacturing, and consulting.
The Akira ransomware gang uses several extortion tactics, including maintaining a dedicated leak website on the Dark Web. This site lists victims and exposes any stolen data if they do not meet their demands. What the victims all have in common is, that once the malware has struck, the files are encrypted and have the file extension .akira. The ransom message later provides Akira’s victims with instructions on how to negotiate the ransom through their TOR portal. The blackmailers will only hand over the key after a ransom has been paid. It is currently not known how high the demands will be in each case. Akira is primarily targeting companies able to pay the ransom and its encryption Trojan is targeting Windows as well as Linux PCs.
What is Akira Ransomware?
Akira Ransomware is a rapidly emerging cyber threat that first appeared in early 2023 and has already positioned itself among the most active ransomware groups worldwide. It operates by infiltrating targeted companies—often through exploiting vulnerabilities in VPNs or other network components—and encrypting critical files with the “.akira” extension. Like other ransomware strains, Akira then demands a hefty ransom in exchange for a decryption key, threatening to leak stolen data if victims fail to comply. With the group’s swift proliferation and its strategic focus on organizations capable of paying large sums, Akira Ransomware presents a serious and evolving challenge to businesses across numerous industries. Understanding its tactics and the vulnerabilities it exploits is essential for implementing effective defenses, such as multi-factor authentication (MFA), network segmentation, and advanced detection solutions like Network Detection & Response (NDR).
The decryptor works, but only on previous versions
An already published decryptor for Akira Ransomware from June 2023 regrettably is now only effective against historic versions of the ransomware, while the hackers have constantly being developed new features and capabilities in each campaign.
While the specific vulnerability of the ransomware was not known for a long time, it is now known that Akira is focusing its efforts on exploiting Cisco ASA VPNs, lacking multi-factor authentication, utilizing CVE-2023-20269 to infiltrate and deploy their ransomware.
The attackers could perform a brute force attack to identify valid username and password combinations, or seemingly authenticated remote attackers could establish a clientless SSL VPN session with an unauthorized user in Cisco ASA (Adaptive Security Appliance) and Cisco Firepower Threat Defense (FTD) Software due to a vulnerability arising from improper separation of authentication, authorization, and accounting (AAA) between the remote access VPN feature and the HTTPS management and site-to-site VPN features. The leak in the remote access VPN functionality of Cisco’s ASA and FTD Software enables them to execute a brute force attack, aiming to discover valid username and password combinations or to establish a clientless SSL VPN session with an unauthorized user.
What Can You Do Now to Mitigate Akira Ransomware?
In general, it is imperative for companies to vigilantly assess risks posed by Akira Ransomware and adopt suitable protective measures, such as keeping software and systems up to date, scrutinizing privileged accounts, and implementing network segmentation.
In this scenario, the implementation of multi-factor authentication can be or could have been a decisive factor, distinguishing between a potentially devastating cyberattack and a relatively harmless attempted intrusion. Certain Security Information and Event Management (SIEM) systems might offer tools and capabilities to identify, evaluate, and mitigate the impact of ransomware, but only with pre-defined Use Cases on board. Additionally, native endpoint solutions -again, only if equipped with preconfigured playbooks – can execute incident response procedures and expedite the detection and remediation of malware.

Put yourself in a better position: NDR and metadata analysis
In monitoring and bringing visibility into the VPN connections, companies using Network Detection & Response (NDR) can detect ransomware attacks like the one explained, in constantly analyzing network traffic for any unusual or unexpected patterns. These may include unexpected spikes in data transfer or unusual communication between devices.
With the use of a network monitoring tool like Exeon.NDR, companies will identify abnormal VPN traffic, especially traffic that deviates from the established (and machine-learned) baselines. The system looks for unusual patterns, unexpected increases in traffic, or repeated login failures. It also reviews logs coming, for instance from Cisco ASA devices or other firewalls. As unusual log-ins, multiple failed login attempts, or simultaneous logins from different locations may indicate an attack, its behavioral analytics tools detect and alert on unusual behavior on the network, analyzing patterns in the system’s behavior to identify anomalies that indicate the security incident.
While network devices are difficult to monitor for most Cybersecurity tools, an NDR provides visibility into normal as well as potentially suspicious activities, seeing the entire network communication. With ExeonTrace, users have the capability to monitor the incoming traffic from external sources or inspect internal connections to network devices.
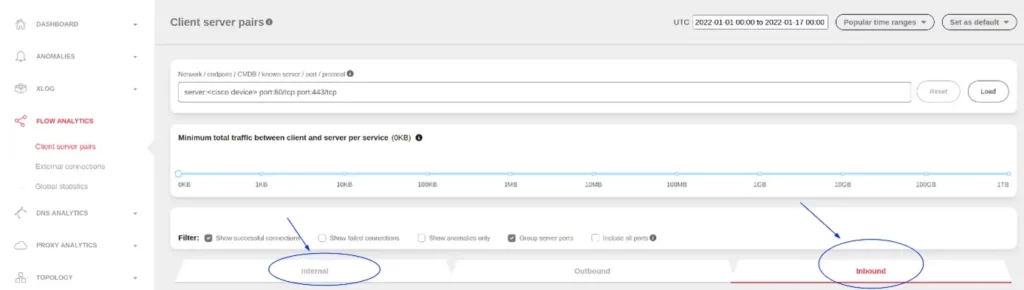
Machine Learning represents a fundamental technological advancement that distinguishes Network Detection and Response (NDR) from other products that could come in handy in the given scenario: in contrast to traditional detection capabilities that focus on identifying only “known” attacks, ML empowers ExeonTrace to discover “unknown” attacks by correlating historical data or identifying anomalous activities that are likely to be malicious. This approach is probabilistic rather than deterministic, and its meta-data analysis can process enormous amounts of data and therefore gains a significant historical correlativity, enabling proactive threat handling.
The bottom line: Preventing ransomware such as Akira
Akira ransomware has swiftly become notorious, ranking as the fourth most active group, and escalating in speed, demanding millions in ransom from targeted companies in various sectors. Akira exploits a vulnerability in Cisco ASA VPNs, focusing on those lacking multi-factor authentication.
Vigilant risk assessment, protective measures, and especially Network Detection and Response (NDR) with AI and Machine Learning are recommended for enhanced cybersecurity and to be armed, as ML enables NDR to uncover unknown attacks without pre-defined use cases.
Think you might be at risk of such a ransomware attack or interested in discussing cybersecurity solutions such as ExeonTrace and its ML power? Speak to one of our experts right here, quickly and easily.
Detect ransomware efficiently: Talk to an expert
Discuss machine learning and future-proof security options with our experts today. No cost, no obligations.



