Boosted by the continual advancement of digital technologies, cyberattacks are increasing in number and sophistication. The variety of legacy and modern IT systems in use, the interconnection of appliances (that used to run isolated), and the vast number of third-party suppliers are increasingly challenging to holistically protect the IT landscape.
As some of those systems were not designed to be connected, security tends to be an afterthought. And the clean-up of the existing infrastructure is highly challenging with a risk of unintentionally overlooking something, which can lead to entry doors for attackers.
Hence, a holistic understanding of the IT network is essential to monitor potential threats. However, no single solution can give complete protection in today’s complex IT landscape. Consequently, it is essential to bring different security angles together.
Addressing this challenge, Gartner has introduced the SOC Visibility Triad to support IT security professionals in defining and furthering their architectural setup and closing entry points that adversaries can exploit to gain unauthorised access.
In this article, we’ll first elaborate on Gartner’s SOC Visibility Triad before going more in-depth regarding the special role Network Detection & Response (NDR) solutions take within this framework.
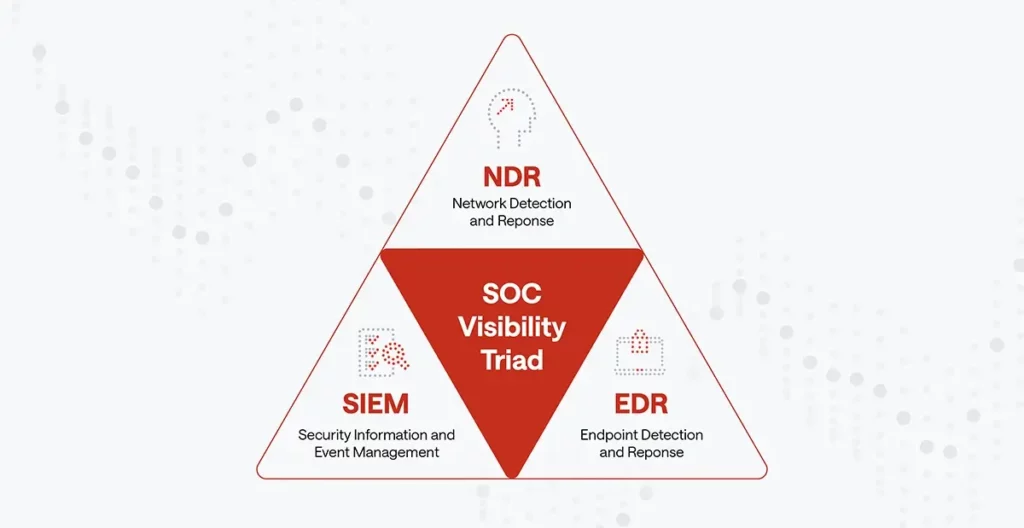
Defining SOC Visibility triad
The SOC Visibility Triad aims to prevent cyber attackers from remaining in your network long enough to achieve their malicious goals. Traditionally, enterprises relied on Security Information and Event Management (SIEM) systems to detect and stop cyberattacks.
However, a lot of manual analysis was needed to interpret the collected data in a SIEM until Endpoint Detection & Response (EDR) and Network Detection & Response (NDR) solutions were introduced. EDR and NDR both specialise in different use cases:
While EDR relies on a piece of software (agent) that is installed on the monitored endpoint to inspect the endpoints’ activities in details, NDR monitors all aspects of network communication for a bird’s eye view of the IT activities independent of whether an agent is installed or not.
Security Information and Event Management (SIEM)
A SIEM solution works by collecting and aggregating security log data from all devices across the network, such as endpoint devices, servers, network devices (switch, router), security solutions (firewalls, IDS/IPS, and EDR), custom applications, and even cloud services. The SIEM stores these logs in a central location using one unified format, where the SOC team checks these logs to detect abnormal activities that can signal a potential cyberattack.
Although SIEM has become an integral part of every enterprise arsenal to detect cyber threats, it still suffers from significant drawbacks:
- The analysis capabilities of SIEMs are limited and often very time-consuming as the primary purpose of SIEMs is to collect and aggregate log data.
- SIEM solutions tend to trigger many false-positive alerts; this wastes the time of SOCs and prevents them from investigating all security alerts.
- SIEMs have little visualisation capabilities, making threat hunting highly complex and cumbersome.
Endpoint Detection and Response (EDR)
EDR is an integrated software solution that monitors endpoint devices (laptops, desktops, and servers) activities in real-time to detect malicious behaviour. EDR collects data from endpoints devices and analyses the collected data to discover malicious patterns. Once found, the EDR will automatically respond to threats or isolate the infected host to prevent spreading the infections to other network areas and devices.
Even though EDR is a critical component of corporate security, its abilities to stop advanced cyberattacks are limited:
- Inability to install on IoT and OT devices. An EDR solution requires installing an agent on endpoint devices for monitoring, which is not feasible on most IoT devices.
- EDR cannot monitor employee-owned devices, which have especially become popular during the COVID19 pandemic.
- EDR fails to provide comprehensive visibility across hybrid IT environments as it focuses on endpoints only.
Network Detection and Response (NDR)
NDR is the backbone of the SOC triad to gain holistic visibility. NDR analyses network traffic passing through the complete IT environment to detect malicious behaviour and respond accordingly.
NDR provides a plethora of security functions that SIEM solutions cannot offer. For instance, NDR can detect advanced cyberattacks and unknown malware by utilising advanced technologies such as domain-specific machine learning models. In contrast to EDR, NDR provides comprehensive visibility (East-West, North-South) over all interactions across the IT environment, independent of agents, including cloud assets.
Future-proof NDR solutions, such as Exeon.NDR, rely on self-learning device behaviour models that can detect threats independent of traffic encryption. In contrast to traditional security solutions, such as firewalls, IDS, and IPS, that rely on deep packet inspection and become blind with the increasing traffic encryption.
Thus, a state-of-the-art NDR is able to discover covert communication channels commonly employed by advanced threat actors such as APT and ransomware operators.
By combining an NDR solution with SIEM and EDR, SOC teams will gain complete visibility over their network and become able to detect unknown threats that continue to emerge daily.
Summary
Gartner’s SOC Visibility Triad outlines the three angles needed to provide a holistic IT security and mitigate the weaknesses resulting from using each one separately. Whilst SIEMs are already widely adopted, EDR and NDR are relatively new aspects of a state-of-the-art corporate IT Security as suggested by Gartner’s framework.
To gain complete visibility, the timely deployment of EDR and NDR makes perfect sense. Among the two newer concepts, NDR is considered the backbone of Gartner’s SOC Visibility Triad providing holistic visibility across all network activities and forming a cornerstone of modern defence strategies.


