In this article, we share some ideas on how to detect and hunt the exploitation (meaning the abuse) of network device vulnerabilities and how Network Detection and Response (NDR) supports such analysis. When working in cybersecurity, you are familiar with the following headline:
Vulnerability XY on product Z may allow an unauthenticated user to execute unauthorized code or commands via specifically crafted requests to the network service 1234/tcp.
One of the first questions threat detection or incident response teams will try to answer is “Was the vulnerability already exploited?”. And often, required network logs for hardware devices are missing. Among other things, the following questions must be answered:
- Which endpoints connected to that network service and when?
- What outgoing connections were established by this network device?
- How is it possible to monitor the network service and network device from now?
Our Exeon.NDR platform covers the following use cases for such a detection and incident response analysis.
- The built-in network detections show clients newly accessing this vulnerable port based on the learned common behavior of that.
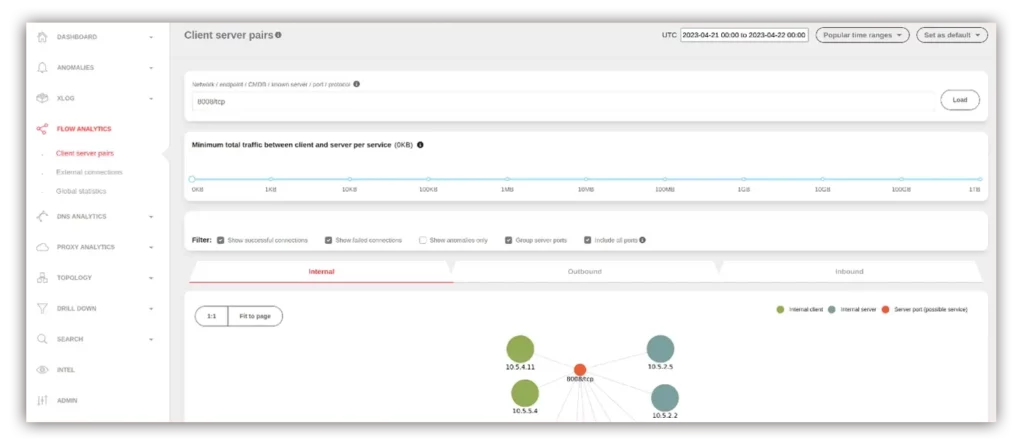
- Get the visibility to the flow logs in Active Services or Flow Analytics to inspect:
- if there are connections to/from that machine by searching for the IP or the port (e.g., 1234/tcp)
- what the traffic volume is for that port by inspecting the table below the graph in Flow Analytics
- how the connections/ports changed over time
Build new detections specifically for:
- Connections and traffic volume to the port or the network device in general and
- Connections and traffic from that network device to the rest of the network
- By creating XLOG tags for that port or IP for successful connections or traffic volume and corresponding analyzers for these tags.
Create new insights and actions for your incident response team:
- Automatically identify where and how an attack occurred
- The IR team can immediately contain the damage
- Eliminate the source of the incident
- For any instance where the Incident Response team gains a new team member. 😊
Even Better with Machine Learning
What Network Detection and Response does in general, and Exeon.NDR with its Machine Learning capacities in particular, can detect and remediate vulnerabilities and attack vectors in your network in the following ways:
Encompassing data collection and traffic monitoring:
Our NDR solution constantly collects and analyzes network data, such as log data, packet data, flow data, and other relevant information, delivering full insight into network activity and giving SOC teams a very good tool to identify and remediate potential threats or security incidents.
Behavioural analysis:
We use machine learning algorithms to see the baseline of normal network behaviour, by analysing historical data, our algorithms learn what is “normal” for the network (Its communication patterns, typical data flow and traffic, the applications and services used be an instance et al).
Using machine learning algorithms Exeon.NDR can detect deviations from the established baseline (suspicious connections, unusual data transfers traffic outside patterns, lateral movements, data exfiltration), etc. and identify unexpected events or unusual patterns and therefore alert the NDR.
Behavioural profiling:
Machine learning algorithms can create behavioural patterns for each user or device within the network. By understanding typical user and device behaviour, the system can detect deviations from these profiles that may indicate compromised accounts or devices.
Machine learning allows us to detect and respond to threats in real time, reducing the time between detection and response. By alerting SOC teams, we enable rapid mitigation of potential threats.
Fast and efficient:
As our system continuously learns from new data thanks to machine learning and improves its detection accuracy over time, false positives can be reduced, and the SOC teams can better focus on real threats. In addition, thanks to machine learning, we can also monitor huge amounts of data where rule-based systems would long ago become inefficient.
Interested in a guided tour of the Swiss-made network monitoring tool with one of our cybersecurity experts? Schedule your free consultation today.


