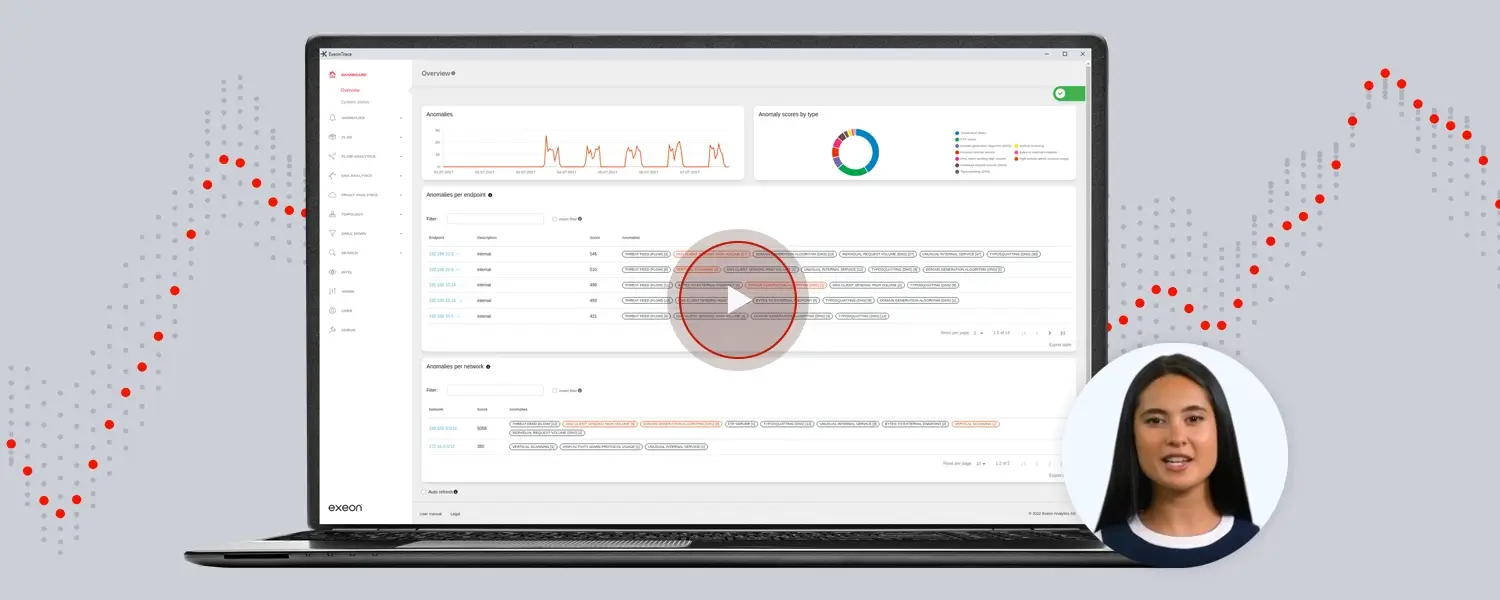
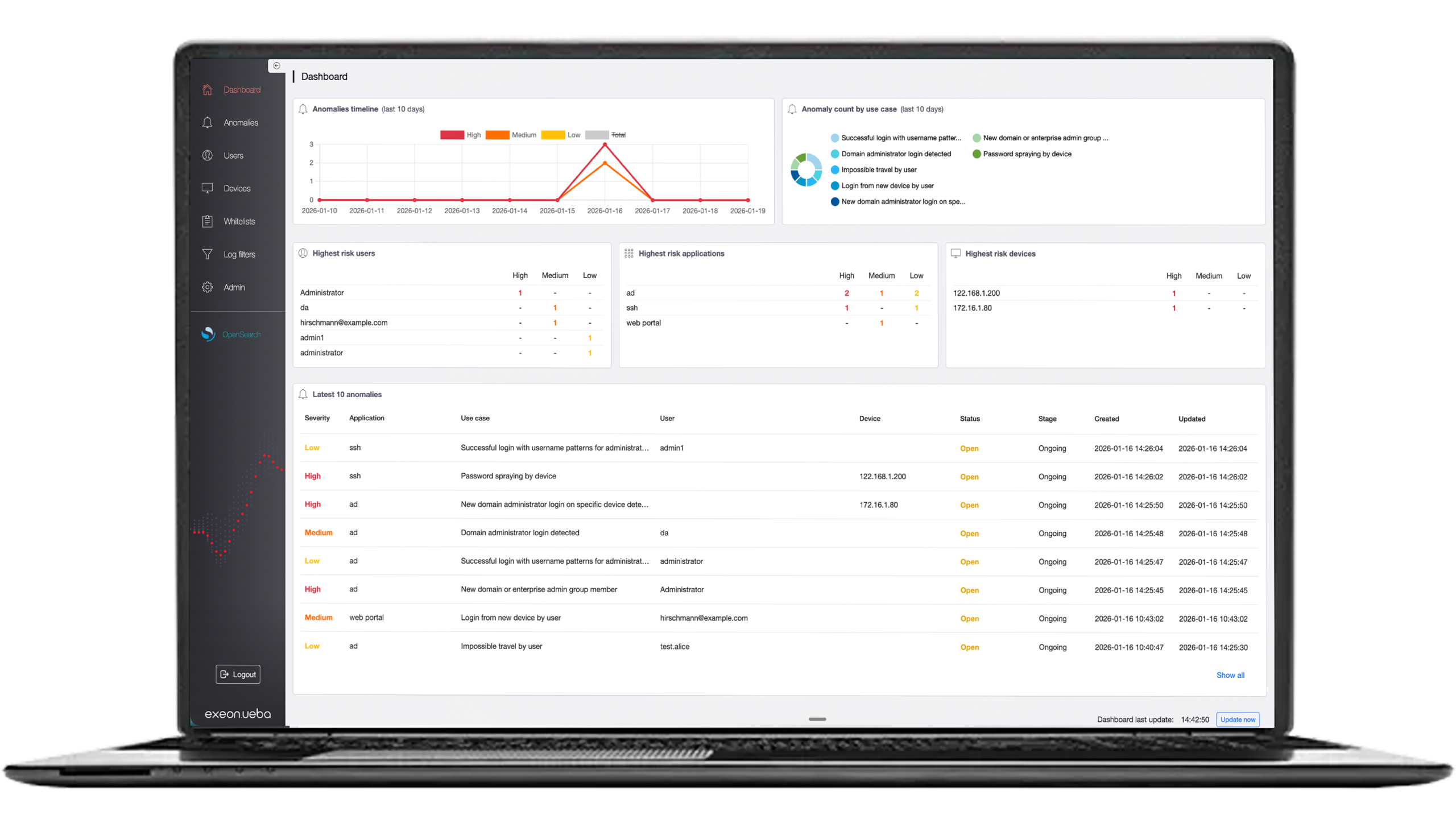
Von den Sicherheitsexperten von Exeon für Sie
Als Team von Cybersicherheitsexperten, Datenwissenschaftlern und Innovatoren teilen wir die Erkenntnisse aus unserer Forschung und Arbeit in diesem Bereich - heute und in Zukunft.
Monatlicher Cyber Flash
Unser monatlicher Newsletter bietet Ihnen Einblicke von IT-Sicherheitsentscheidern und technischen Experten, Veranstaltungen, Webinare und Branchennews. Melden Sie sich unten an!