Datensouveränität ohne Kompromisse
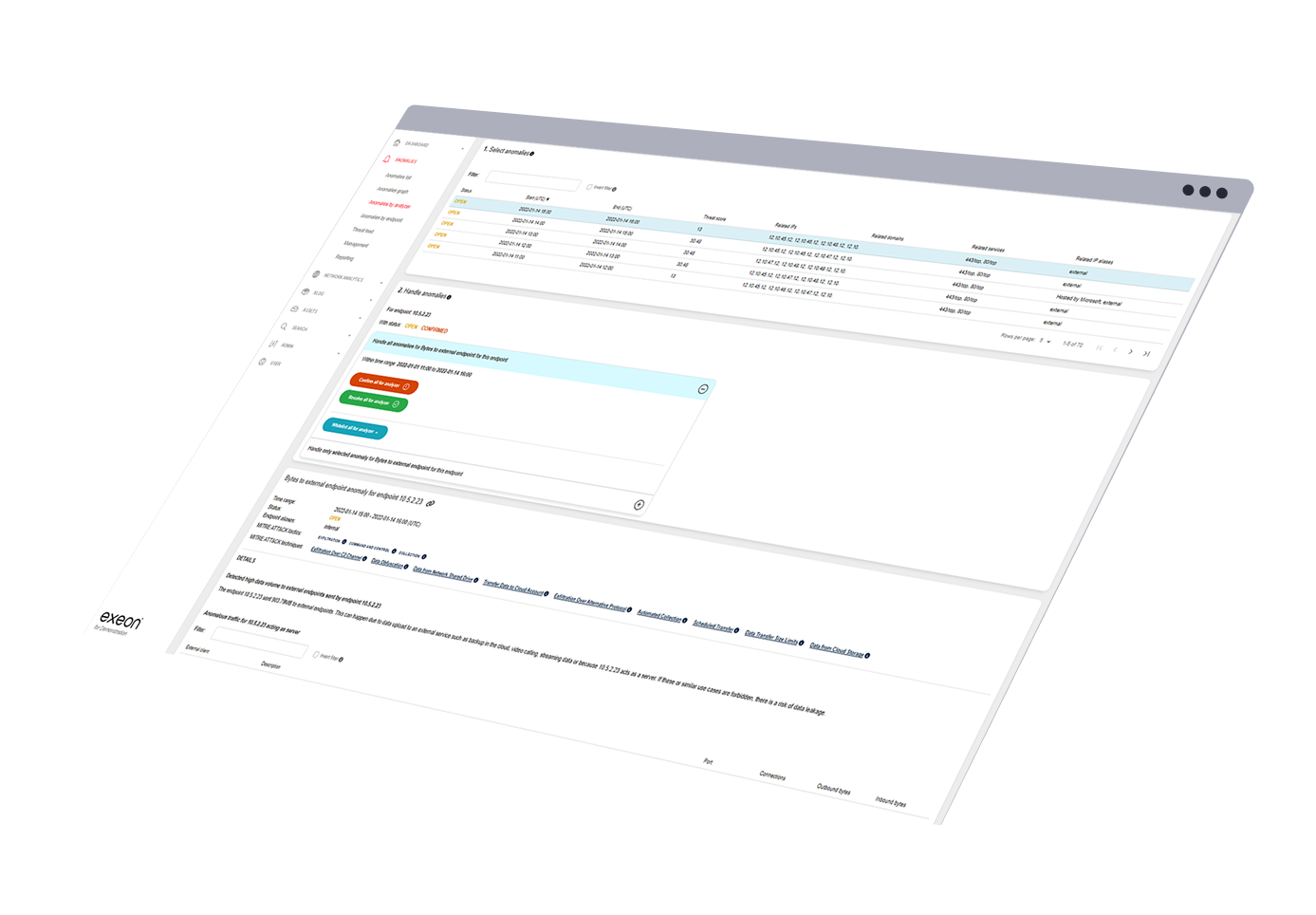
Ihre Daten sind gefährdet
Anstieg der verschlüsselten Bedrohungen im letzten Jahr.
Durchschnittliche Kosten einer Datenschutzverletzung (USD) im vergangenen Jahr, Anstieg um 10 % gegenüber dem Vorjahr.
aller Verstöße betreffen Kundendaten: Steuernummer, E-Mail, Telefonnummern, Adressen.
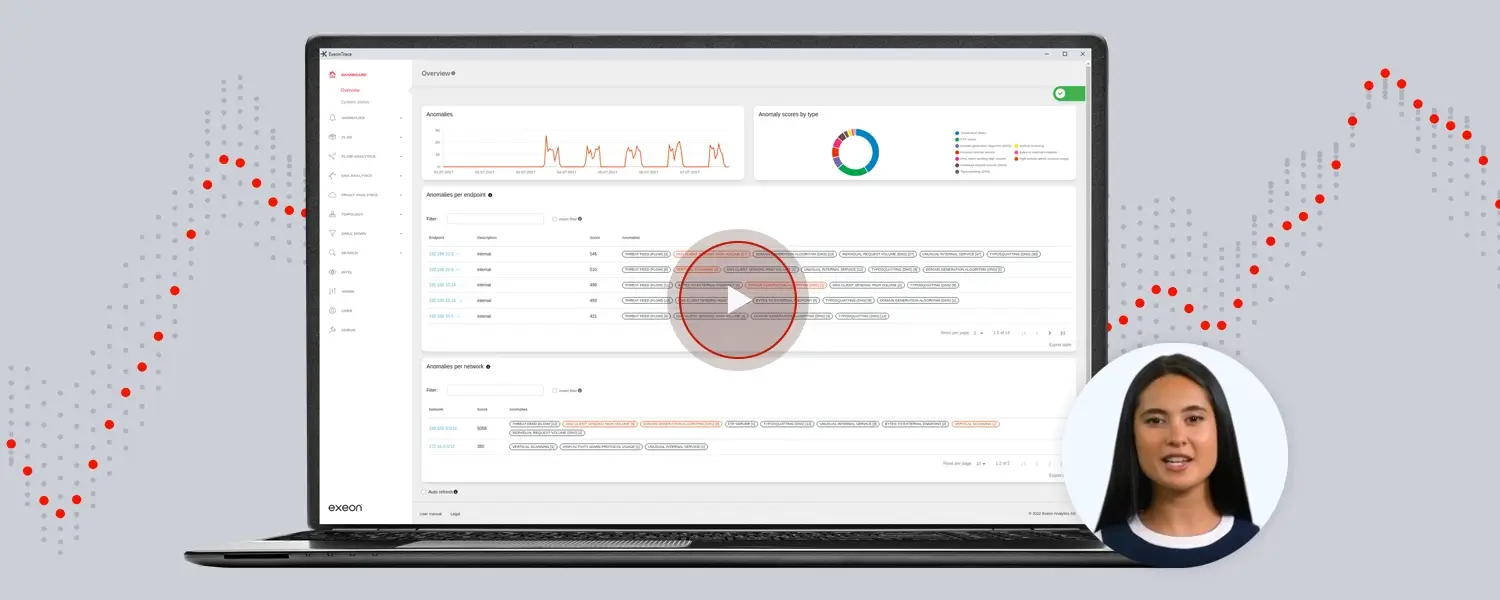
Wir unterstützen Sicherheitsteams dabei, kritische Daten zu schützen.
Wir sind darauf spezialisiert, Sicherheitsteams mit allen Funktionen auszustatten, die sie benötigen, um hochentwickelte Bedrohungen zu erkennen und darauf zu reagieren.
Erweiterte Bedrohungserkennung
Herkömmliche Sicherheitsmaßnahmen versagen oft im Kampf gegen APTs. Wir setzen KI-gesteuerte Analysen ein, um versteckte Bedrohungen zu erkennen, damit sensible Daten sicher bleiben.
Klarheit im Chaos der Daten und Warnungen
70 % der SOC-Analysten fühlen sich von der Menge der Warnmeldungen überfordert. Unsere intelligenten Korrelations- und Priorisierungsmechanismen filtern das Rauschen heraus, damit sich die Sicherheitsteams auf die wirklich wichtigen Dinge konzentrieren können.
Effizienz trotz Grenzen
Wir automatisieren die Erkennung, Untersuchung und Reaktion auf Bedrohungen und ermöglichen es Sicherheitsteams, Risiken zu minimieren und wertvolle Daten zu schützen.
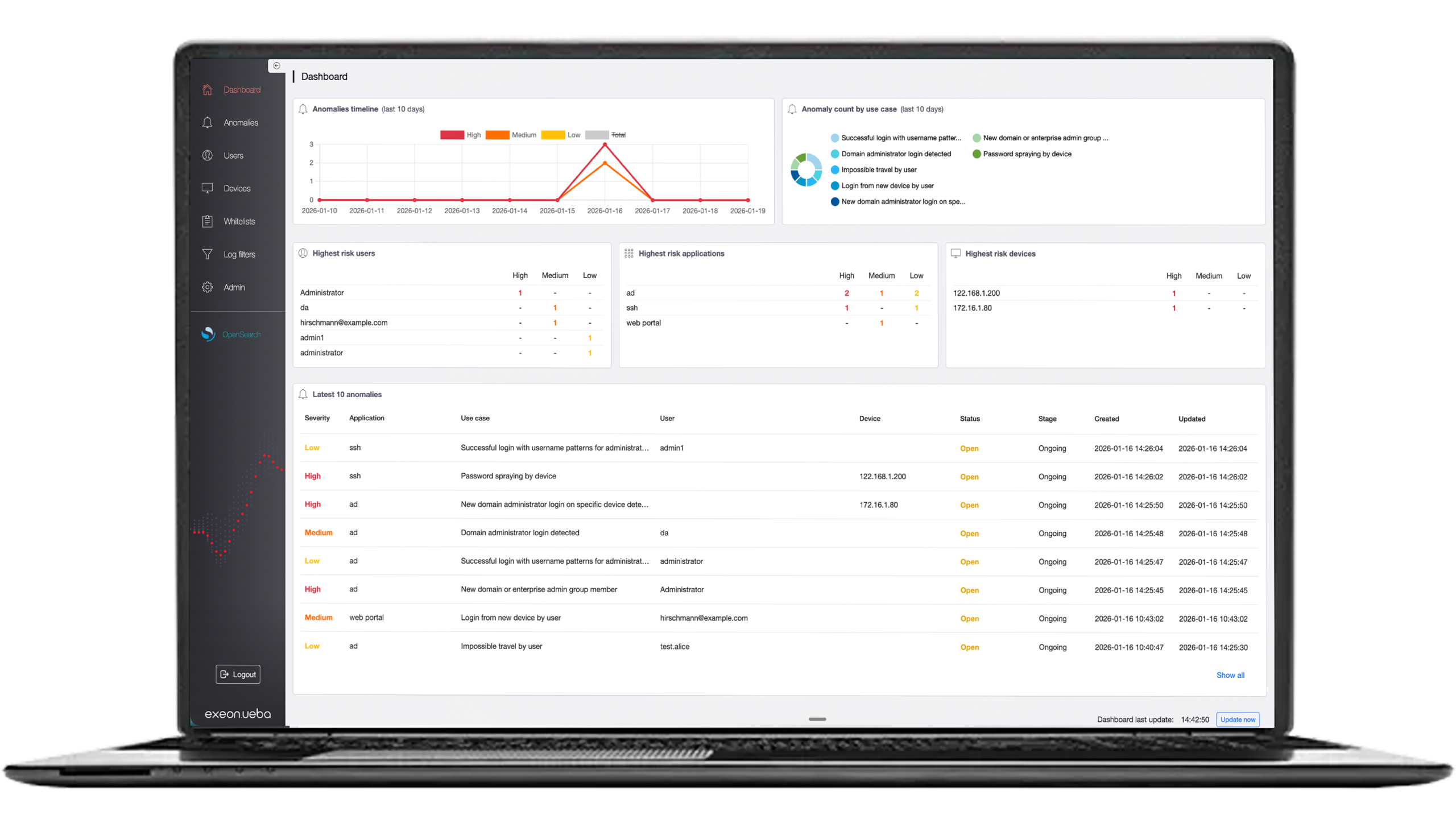
Wie Sicherheitsteams von unserer Datensicherheit profitieren
Echtzeit-Erkennung und -Reaktion auf Bedrohungen
Unsere Lösung analysiert kontinuierlich Netzwerkprotokolldaten, um laterale Bewegungen und Datenexfiltration in Echtzeit mit maximaler Genauigkeit zu identifizieren und zu stoppen.
- Intelligente Anomalieerkennung: Fortschrittliche Machine-Learning-Algorithmen erkennen ungewöhnliche Verhaltensmuster genau in dem Moment, in dem sie auftreten.
- Risikobasierte Alarmierung: Auf Grundlage des Sicherheitswerts sensibler Daten erhält Ihr Security-Team sofortige Warnmeldungen – priorisiert nach Echtzeit-Risikobewertung.
Netzwerküberwachung zur Sicherung der Datenintegrität
Exeon.NDR gewährleistet die Integrität Ihrer Daten, indem es den Netzwerkverkehr kontinuierlich auf Anzeichen von Manipulation, unbefugten Änderungen oder Beschädigungen analysiert.
- Schnelle Anomalieerkennung: Potenzielle Verstösse gegen die Datenintegrität werden in Echtzeit identifiziert, sodass sichergestellt ist, dass Ihre Informationen unverändert und vertrauenswürdig bleiben.
- Verhaltensbasierte Analyse: Der Fokus liegt nicht auf der inhaltlichen Inspektion der Daten, sondern auf der Erkennung abweichender Kommunikationsmuster und typischer Angriffsszenarien – ohne in die Privatsphäre sensibler Inhalte einzugreifen.
Einhaltung der Datenschutzbestimmungen
Exeon-Produkte unterstützen die Einhaltung von Datenschutzgesetzen wie der DSGVO und DORA in vielerlei Hinsicht und stellen sicher, dass Ihr Unternehmen alle gesetzlichen Anforderungen erfüllt.
- Sichere Datenverarbeitung und Ereignisprotokollierung.
- Automatisierte aufsichtsrechtliche Meldungen im Detail.
- Die kontinuierliche Überwachung aller Geräte und Benutzerinteraktionen ermöglicht präzise historische Untersuchungsinformationen.
End-to-End-Datensicherheit
Umfassender Einblick in das gesamte Netzwerk und die Endpunkte, um Schwachstellen und Bedrohungen zu erkennen, die die Sicherheit und Vertraulichkeit sensibler Daten gefährden könnten.
- Erkennung von Lateral Movement
- Bedrohungserkennung ohne blinde Flecken
- Erkennung von Sicherheitsverstößen bei allen Anlagen, einschließlich nicht verwalteter Geräte.
Exeon.NDR – Maximale Datensicherheit ohne Kompromisse
Keine Entschlüsselung erforderlich
Blitzschnelle Erkennung lateraler Bewegungen
Keine Blind Spots – keine unbemerkte Datenexfiltration
Unser Produkt überwacht kontinuierlich die gesamte Netzwerkkommunikation und lässt keine blinden Flecken zu. Datenexfiltration wird sofort erkannt und unterbunden.
100 % Compliance und Datenschutz
KI-basierte Angriffs- und Anomalieerkennung durch NDR
Metadatenanalyse: skalierbar und sicher für Leistung und Datenschutz
Während Deep Packet Inspection (DPI) eine tiefgehende Inhaltsanalyse ermöglicht, bietet die Analyse von Netzwerk-Metadaten einen deutlich effizienteren, skalierbareren und zugleich datenschutzfreundlichen Ansatz. Durch den Fokus auf Kommunikationsmuster statt Inhalte erkennt sie zuverlässig anomales Verhalten und typische Angriffsszenarien, ohne die Netzwerkperformance zu beeinträchtigen. Damit ist die Metadatenanalyse eine sichere, compliance-konforme und zukunftssichere Lösung für moderne, komplexe Netzwerke.
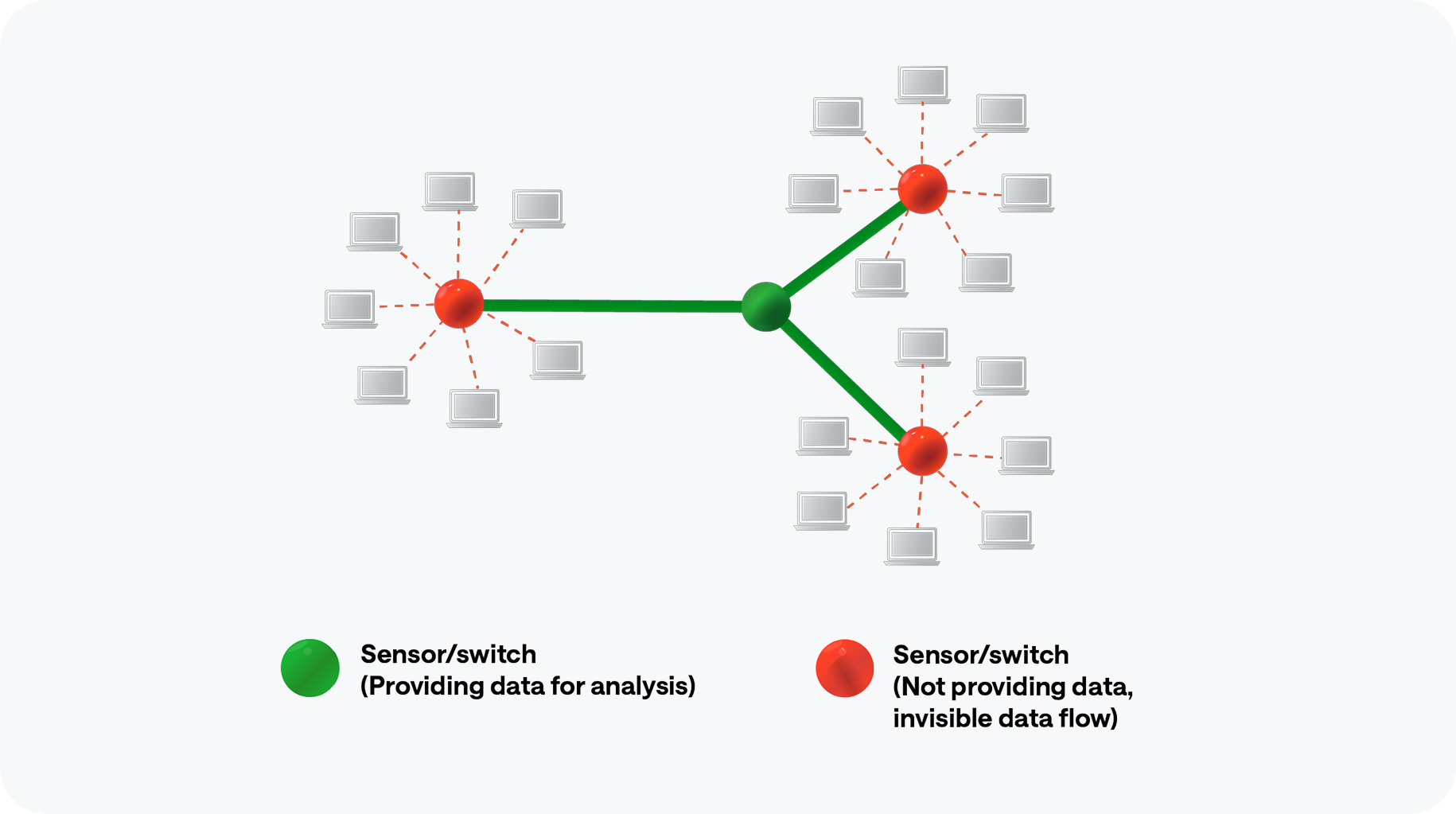
Tiefgreifende Packet Inspection
Nur der über gespiegelte Core-Switches laufende Datenverkehr
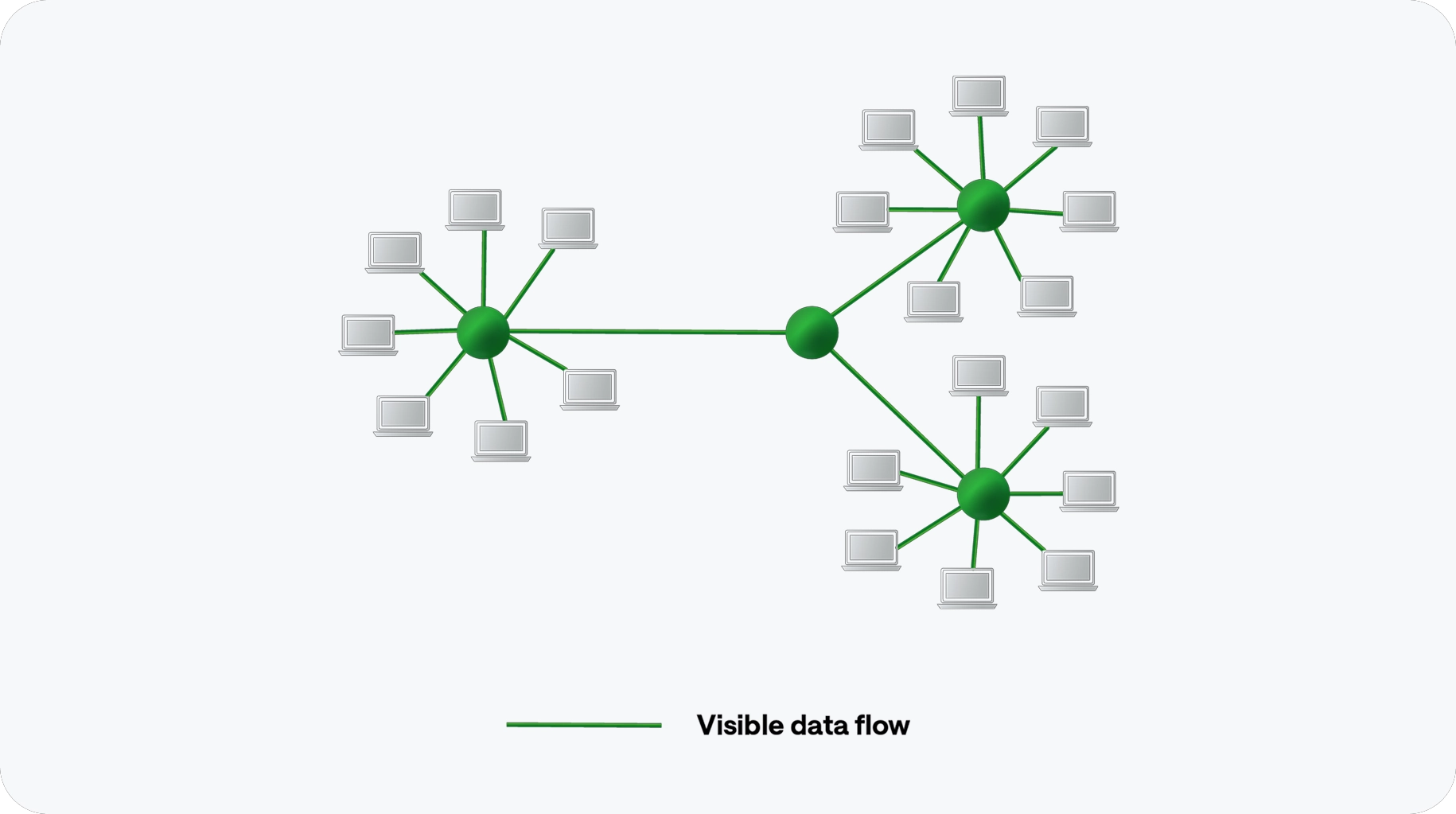
Metadaten-Analyse
Sämtliche Netzwerkkommunikation über physische und virtualisierte Netzwerke
Verwandte Lösungen für Sie
Verschlüsselung
Deployment
Bewährt bei global agierenden Unternehmen


















Factsheet

Einblicke von unseren Sicherheitsexperten
Klarheit im Cyber-Dschungel: Fachbeiträge unserer Vordenker im Bereich KI-gestützter Cybersicherheit.
Erleben Sie schon heute zukunftssichere Datensicherheit
Erfahren Sie von einem unserer Experten, wie Exeon-Produkte Ihre Daten schützen, ohne Ihre Privatsphäre zu beeinträchtigen.